| Week 1 | T&L Activities:Welcome to Cyber SecurityUnit introduction Our increasing reliance on computer systems and the data they contain makes us vulnerable to attacks from cyber criminals, and also to the loss of these systems if there is an accident or a natural disaster. As IT system security is improved, more sophisticated methods of attack are developed, and it is important that organisations have robust plans in place to deal with a cyber security incident before it occurs. All IT professionals require a good understanding of the current threats to systems, how to apply appropriate and effective protection methods and how to manage a cyber security incident. In this unit, you will examine the many different types of cyber security attacks, the vulnerabilities that exist in networked systems and the techniques that can be used to defend an organisation’s networked systems. You will investigate the techniques used to assess risks and ways of planning to deal with the results of a cyber security incident and recover systems following an incident. You will examine scenarios, carry out risk assessments and prepare protection plans before protecting networked systems. You will also examine evidence from cyber security incidents and relevant security documentation, using the evidence to make recommendations for improvement. To complete the assessment tasks within this unit, you will need to draw on your learning from across your programme. As IT systems evolve, there is an increasing need for IT professionals to protect networked systems and the information they contain, while providing enhanced features and benefits for organisations, customers and individuals. This unit will help prepare you for IT courses in higher education and for technician-level roles and apprenticeships in a variety of related areas.
Summary of assessmentThis unit is externally assessed by a task set and marked by Pearson. The set task will be completed under supervised conditions in sessions: Part A is five hours and Part B is four hours. Part A must be completed before Part B and both parts need to be completed during the three-week assessment period set by Pearson. The set task will assess learners’ ability to design appropriate cyber security measures for networked systems and to analyse a security incident. The number of marks for the unit is 80. The tasks will be marked using a levels-based mark scheme that is located in the sample assessment materials. The availability of the task is December/January and May/June each year. The first assessment availability is May/June 2018. Sample assessment materials will be available to help centres prepare learners for assessment.
Assessment outcomes AO1 Demonstrate knowledge and understanding of technical language, security threats, system vulnerabilities and security protection methods, and implications resulting from successful threats AO2 Apply knowledge and understanding of security threats, system vulnerabilities, and security protection methods and implications in order to risk assess systems and select appropriate tools to secure them AO3 Analyse forensic evidence data and information to identify security breaches and manage security incidents AO4 Evaluate protection methods and security documentation to make reasoned judgments and draw conclusions about their efficacy AO5 Be able to plan a secure computer network and manage security incidents with appropriate justification
A1 Cybersecurity threats All systems are vulnerable to attack from external and internal threats.Scale of the cyber threat 2017 was punctuated by cyber attacks on a scale and boldness not seen before. This included the largest recorded cyber heist, the largest DDoS attack and the biggest data breach ever being revealed (2 NCSC/NCA – The Threat to UK Business report 2016/2017) .
For more information about the cyber threat or for news on the latest cyber incidents, visit ncsc.gov.uk/index/report twitter.com/ncsc (@NCSC) nationalcrimeagency.gov.uk/news nationalcrimeagency.gov.uk/publications twitter.com/NCA_UK (@NCA_UK) twitter.com/CyberProtectUK (@cyberprotectUK) actionfraud.police.uk/news
How internal threats occur, including:Employee sabotage and theft, including of physical equipment or data, and damage such as fire, flood, power loss, terrorism or other disasters
Case study - a 37-year-old former IT staff member for the U.S. subsidiary of Japanese drug company, Shionogi, pleaded guilty to remotely infiltrating and sabotaging the company's IT infrastructure this past February. The damage scrambled the company's operations for days and cost Shionogi more than $800,000 in damages, according to IDG News Service. The former employee, Jason Cornish, logged in to the network using a hidden virtual server he had previously created, then wiped out the company's virtual servers one by one, taking out e-mail, order tracking, financial and other services, according to IDGNS and court filings. IDGNS also reported that Cronish's former boss at Shionogi refused to turn over network passwords and was eventually fired. Prevention strategies; 1. Create and maintain good documentation for networks and resources. 2. Maintain "super administrator" access where possible a company can maintain the highest level of control over the systems to prevent infiltration. 3. Have fast and clear change procedures for administrative passwords so that no worker can make system changes once they leave the company. 4. Use IT tools that allow you to set thresholds and alerts when there are unexpected activities inside the network to aid in the detection of possible sabotage events.
Employees may remove data using USB or external devices to hold a company to ransom or sell it to competitors. Hardware equipment may also be vulnerable, this has the ability to be physically removed or deliberately damaged through a number of ways, fire, water.
Why might an employee commit sabotage or theft of a business’s computer systems or data?
Unauthorised access by employees and other users to secure areas and administration functions, including security levels and protocols It is vital that companies consider the use of access levels and privileges that are provided to its staff and employees. Password policies must be put in to place to protect the system from brute force attacks where individuals can cycle through passwords to gain access. Systems can be put in to place to protect the company that for example locks out the users from the system after a sequence of wrong password attempts.
Weak cyber security measures and unsafe practices, including security of computer equipment and storage devices, security vetting of visitors, visiting untrustworthy websites When visiting a website or
Accidental loss or disclosure of data, including poor staff training and monitoring. Employees who aren’t aware of their cyber security obligations are prone to ignore relevant policies and procedures, which could lead to unintentional disclosures of data or successful cyber attacks. There is also the threat of phishing and ransomware (which is often delivered through phishing emails). CyberEdge’s report found that spear phishing – sending malicious emails that claim to be from a legitimate source – dominates traditional phishing scams.
Create an information leaflet (A5) with examples for the following, employee sabotage and theft.
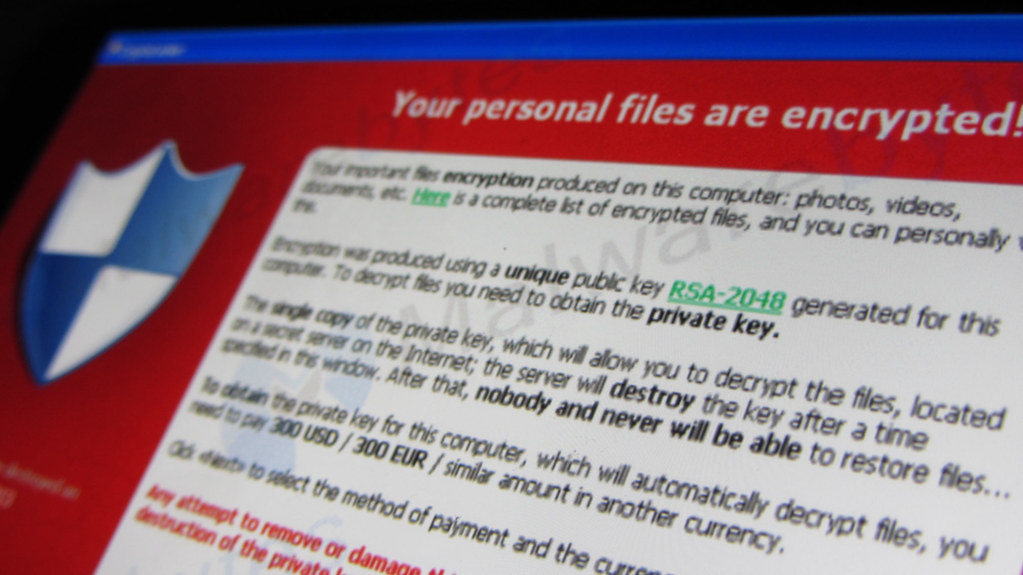
• Understand how external threats function, including:Malicious software (malware), including spyware, adware, ransomware; viruses, including worms, rootkits and trojans o hacking, including commercial, government, individuals.
Ransomware
Classic case of ransomware hit the NHS in 2017 where almost all systems were hit. Any machine not affected was required to remain off until the issue was resolved, so to stop any further infection or spreading of the original error Trojans
Sabotage, including commercial, government, terrorism, individuals.
Social-engineering techniques used to obtain secure information by deception. What is social engineering?Social engineers take advantage of human behavior to pull off a scam. If they want to gain entry to a building, they don't worry about a badge system. They'll just walk right in and confidently ask someone to help them get inside. And that firewall? It won't mean much if your users are tricked into clicking on a malicious link they think came from a Facebook friend or LinkedIn connection.
Getting a free dinner when being ‘stood up’I’m not one to turn down a free dinner, but I wouldn’t go as far as Kyle Baldinger did to get one. Kyle saw a tweet that said “If you go to dinner alone always ask for a table for two. Look sad as you eat and you almost always get a free dessert”. So, he thought he’d give it a go, and live-tweeted what happened. [Warning: long image]
If you’d rather not read the whole thing, the short version is that Kyle bagged himself a free dinner after fooling a restaurant into believing he was stood up. Whilst this example is playful is demonstrates the ways in which social engineering can be used to gain an advantage. Social engineering has proven to be a very successful way for a criminal to "get inside" your organization. Once a social engineer has a trusted employee's password, he can simply log in and snoop around for sensitive data. With an access card or code in order to physically get inside a facility, the criminal can access data, steal assets or even harm people. What are the ways in which an employee could give out information?
Understand that the impact of a credible threat is likely to result in some form of loss, such as:Operational loss, including manufacturing output, service availability and service data
Financial loss, including organisational, compensation and legal liability
Reputation loss, including lack of service and employee or customer information
Intellectual property loss, including new product design or trade secret.
Understand that the impact level of a successful attack on an organisation is determined by the value of the loss, and that the value may not always be a monetary one.
Know that cyber security threats vary over time and cyber security organisations provide regular updates on the current and changing threat landscape.
Files that support this week | English:
0 0 |
Assessment:
Just a Minute - At the end of the lesson teachers ask learners to summarise their learning. The comparison of these summaries against learning objectives informs planning. 0 |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 2 | T&L Activities:A2 System vulnerabilities• Understand that different types of computer and/or system are exposed to different threats and that they contain different vulnerabilities. Possible vulnerabilities include: o network, including firewall ports and external storage devices o organisational, including file permissions or privileges, password policy o software, including from an untrustworthy source, downloaded software, illegal copies, SQL injection and new zero-day exploits o operating system, including unsupported versions, updates not installed o mobile devices reliant on Original Equipment Manufacturers (OEMs) to update system software o physical, including theft of equipment, Universal Serial Bus (USB) storage devices with sensitive data, collection of passwords and other information by social-engineering methods o process of how people use the system, including leaks and sharing security details o security implications of cloud computing and of the Internet of Things (IoT) devices. • Understand where to find up-to-date sources of information on specific known hardware and software vulnerabilities. • Attack vectors, including: Wi-Fi, Bluetooth®, internet connection, internal network access. Files that support this week
| English:
er |
Assessment:
More Than Just a Minute - Learners assess themselves against key learning points indicating a level of understanding to inform teacher planning. Traffic Lights - Learners use green, amber and red traffic lights to indicate levels of understanding and to attract support from peers and the teacher. |
Learning Outcomes:
test |
Awarding Organisation Criteria:
|
| Maths:
re |
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 3 | T&L Activities:A3 Legal responsibilitiesUnderstand how the current and relevant European Union (EU) General Data Protection Regulation (GDPR) and United Kingdom legislation or other international equivalents apply to different systems, including: • Data Protection Act 1998 and amendments, requirements for organisations to keep data secure • Computer Misuse Act 1990 and amendments, its definitions of illegal practices and applications • Telecommunications (Lawful Business Practice) (Interception of Communications) Regulations 2000 and amendments, requirements to allow companies to monitor an employee’s communication and internet use while at work • Fraud Act 2006 and amendments, requirements to deal with services using IT-based methods to steal information for fraudulent purposes • Health and Safety at Work etc. Act 1974 – duties of employers, employees, the Health and Safety Executive (HSE) and others, general prohibitions Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 4 | T&L Activities:A4 Physical security measuresUnderstand the use and effectiveness of physical security measures, including: • site security locks, card entry, biometrics, closed-circuit television (CCTV), security staff, alarms, protected cabling and cabinets • data storage, data protection and backup procedures, including planned automated backup, on- and off-site data storage and cloud storage. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 5 | T&L Activities: A5 Software and hardware security measures • Understand the use and effectiveness of software and hardware security measures, including: o antivirus software and detection techniques, including virus signatures, heuristics techniques used to identify potentially suspicious file content, techniques for dealing with identified threats o software and hardware firewalls and the filtering techniques they use, including: – packet filtering and inspection – application layer awareness – inbound and outbound rules – network address o user authentication: – user login procedures – strong password – text and graphical password – biometric authentication – two-step verification – security tokens, including USB-based and near field keys – knowledge-based authentication, including question and response pairs – Kerberos network authentication for Windows® and Linux®-based operating systems – certificate-based authentication o access controls and the methods to restrict users’ access to resources, including applications, folders, files and physical resources o trusted computing. • Understand the purpose and uses of encryption, including: o safe password storage o digital rights management (DRM) o file, folder, disc encryption o communications encryption: – built into devices, including smartphones and tablets – The Onion Router (Tor) – virtual private networks (VPNs) – digital certificates and certificate authorities – Hypertext Transfer Protocol Secure (HTTPS) – public/private keys. • Precautions that can be taken to protect a wireless local area network (WLAN) from unauthorised access, including: o MAC address filtering and hiding the service set identifier (SSID) o wireless encryption – Wired Equivalent Privacy (WEP), Wi-Fi Protected Access 2 (WPA2) and Wi-Fi Protected Setup (WPS), mitigating known wireless vulnerabilities o consideration of security issues during network and system design to ensure security is built-in from the development stage. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 6 | T&L Activities:Use of networking architectures and principles for security
B1 Network types• Applications and features of networks: o local area network (LAN), WLAN, wide area network (WAN), storage area network (SAN), personal area network (PAN) o intranet, extranet, internet, cloud o wired and wireless integration. • Applications and features of network topologies: o physical topologies, including star, extended star, hierarchical, wireless mesh, ad-hoc (mix of wired and wireless for bring your own device (BYOD)) o logical topologies, including Ethernet standards for wired and wireless (802 family). • Applications and features of network architecture: o peer to peer o client/server o thin client. • Modern trends, including applications and features of: virtualisation, cloud computing, BYOD, software-defined networking (SDN), storage-defined networks and the IoT. • Be able to interpret and amend network schematic diagrams using suitable software. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 7 | T&L Activities: Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 8 | T&L Activities:B2 Network components• Application and features of hardware components, including: o end-user devices, including mobile o connectivity devices, including switches, routers, access points, multi-functional devices, USB hubs and modems o connection media, including cable, wireless (Wi-Fi, Bluetooth, and infrared (IR)), fibre and Li-Fi. • Applications and features of external media and storage, including flash drives and optical media. • Applications and features of software components, including: o network and device operating systems o network monitoring, management and troubleshooting tools, including performance monitor, events and logs viewer, vulnerability scanners and packet sniffers o network applications, including database, document management and network discovery tools. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 9 | T&L Activities:B3 Networking infrastructure services and resources• Understand the application and function of: o Transmission Control Protocol/Internet Protocol (TCP/IP) o ports o packets o network address translation (NAT), including the structure of IPv4 and IPv6 addressing and RFC 1918 private addresses. • Understand the application of network operating systems, including domains and sub-domains. • Understand the application of network devices to configure networks, including network segmentation. • Understand the function and application of network infrastructure services, including: o domain name system (DNS) o directory services (DS), including active directory, open directory, OpenLDAP o authentication services o Dynamic Host Configuration Protocol (DHCP) o routing o remote access services. • Understand the function and application network services and resources: o file and print services o web, mail and communications services. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 10 | T&L Activities:Cyber security protection plan
C1 Assessment of computer system vulnerabilitiesUnderstand that: • the types and uses of tools and methods to assess the vulnerabilities in computer systems, including port scanners, registry checker, website vulnerability scanners, vulnerability detection and management software, and assessing user vulnerabilities • the purpose of independent third-party review of a system and network designs before implementation • the applications and features of penetration testing for common threats, those in the Open Web Application Security Project (OWASP) top 10. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
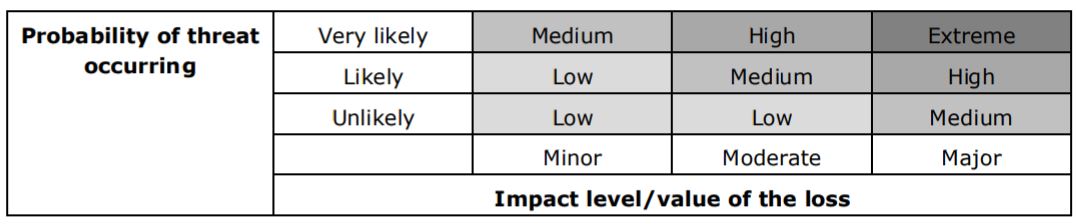
| Week 11 | T&L Activities: C2 Assessment of the risk severity for each threat • A risk is a threat that could result in some form of loss at some point in time. • Risk severity = probability of the threat occurring × expected impact level/value of the loss. • Measures for risk severity include: o risk severity = low, medium, high and extreme o probability of the threat occurring = unlikely (approximately every year), likely (approximately every week or month) and very likely (approximately once or more a day) o impact level/value of the loss = minor, moderate and major. • Be able to use the following risk severity matrix: • Risk assessment approach: o risk assessments are carried out during system design (review) and at regular intervals during operation (audit) and following a security breach, as threats are constant and ever changing o a risk assessment method: – identify possible threats and assess the probability of different threats occurring – assess the vulnerabilities of a computer-networked system to specific threats – assess the impact level/value of the potential loss – determine the risk severity (low, medium, high and extreme). Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 12 | T&L Activities: C3 A cyber security plan for a system A plan for a networked system, including: • cyber security protection measures to be taken (actions) for the most severe (medium, high and extreme) risks with the largest impact level/loss value and that are most likely to occur, to include: o hardware protection measures, including firewalls, routers, wireless access points o software protection measures, including anti-malware, firewall, port scanning, access rights and information availability o physical protection measures, including locks, CCTV, alarms, data storage and backups o alternative risk management measures, including risk transfer to a third party (commissioning a service provider), risk avoidance by stopping an activity and risk acceptance • a justification about how each planned protection measure would protect the system from attack • an overview of any technical and financial constraints • an overview of legal responsibilities • an overview of usability of the system, including the degree to which security restrictions impact on the efficiency of the system in terms of the ease of completing tasks and the user experience • outline cost–benefit analysis of implementing the protection measures • test plan to check that the protection measures work as intended, including the test description, expected outcome, and possible further action following the test. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 13 | T&L Activities:D Cyber security documentation
D1 Internal policiesGeneral IT policies • The purpose and content of general security-related IT policies and their effectiveness, including: o understanding the requirements to prepare a cyber security policy using the Plan-Do-Check-Act loop derived from part of the International Organization for Standardization (ISO) 27001:2013 o organisation policies and their application, including policies on internet and email use, security and password procedures, staff responsibilities, staff IT security training o security audits and their application to check compliance against policies o backup policy – selection of data, methods (full and incremental), frequency and storage o data protection policy – to ensure organisational compliance with the relevant legislation. Incident response policy • The purpose and content of an incident response policy and associated procedures: o assembling the Computer Security Incident Response Team (CSIRT), roles in the team, including team leader, incident lead, associate members o incident reporting procedures, including what constitutes a security incident, and how to report it and to whom o initial assessment of the incident, including identifying if this is a real incident, the type of attack and its severity o communicating the incident to the CSIRT and other relevant individuals o containing the damage and minimising the risk o protect people’s safety: – protect sensitive data and other data, protecting the most valuable first – protect hardware and software – minimise disruption to computing resources o identifying the type and severity of the compromise, including the nature of the attack, its intent, its origin and the systems and files that have been compromised o protecting evidence and creating backups for evidence and data recovery, including the removal and storage of original hard disks o notifying external agencies, if appropriate, and discussing options with legal representatives, contact external agencies such as law enforcement, external security and virus experts o recovery of systems and identification of the point in time when the compromise occurred and restore backups from before that point in time o compile and organise incident documentation, including documentation created by the CSIRT identifying the details of the breach and actions taken o know the importance of preserving and collating documentation that may be needed to prosecute offenders o review outcomes to update policies and improve training. Disaster recovery policy • Understand the topics typically covered in a disaster recovery plan and their purpose: o identification of critical systems, definitions of recovery time objective (RTO) and recovery point objective (RPO) o prevention, response and recovery strategies for critical systems, including: – people responsible – facilities and equipment required – data backup location and format – network connectivity and bandwidth – suppliers of equipment and people o definition of recovery procedures for each critical system o disaster recovery plan structure following ISO 27031/24762 or other relevant international equivalents, including: – introduction – roles and responsibilities – incident response procedures – activating the disaster recovery plan – procedures to be followed. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 14 | T&L Activities:D2 External service providers• External service provider (ESP) agreements will include: o cloud o hardware o software. • Understand the implications of ESP agreements, including: o legal ownership and jurisdiction, including geographical location, data movement across borders, procedures when an agreement ends Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 15 | T&L Activities:E Forensic proceduresE1 Forensic collection of evidenceUnderstand the forensic collection of evidence following a security incident and its purpose: • desktop forensics: o meeting requirements for desktop forensics, including: – confiscation of devices – taking an image of the system – using a forensic analysis tool – reviewing files and settings – reviewing system logs – reviewing user activity – malware analysis and alerts o the challenges of live forensics: – changing data in situ – recovering corrupted data and preventing data corruption – capturing data in active memory – losing temporary files • network forensics: o agreeing a network-testing methodology with forensic supervisory and investigatory authority o scanning of local infrastructure: – ensuring permission is granted – ensuring that testing protocol will not disrupt a live system – passive and active analysis tools o reviewing and analysing firewalls, infrastructure devices, including switch, router, wireless access point, client or server logs o analysing malware activity and alerts. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |
| Week 16 | T&L Activities:E2 Systematic forensic analysis of a suspect system• Requirements for maintaining an accurate record, made at the time, or as soon after the incident as possible. • Retaining snapshots of the system. • Requirements for the recording of all findings and considering how reliable the evidence is. • Requirements for the recording of any alterations that have been intentionally and unintentionally imposed by the investigator. • Requirements for the creation of visual evidence of findings. • Ensuring the evidence is relevant and not a false positive. • Evaluation of the findings to determine whether or not they: o provide evidence of a crime and/or an incident o show that the system has been externally and/or internally compromised o strongly support one possible cause more than other possible causes. • Make recommendations to prevent security incidents from reoccurring in the future, including improvement(s) to the: o content of cyber security documentation (policies and/or agreements) o adherence of cyber security documentation (policies and/or agreements) o security protection measures (physical, software and/or hardware). Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
| Maths:
|
|||||
| Stretch and Challenge:
|
E&D / BV | ||||
| Homework / Extension:
|
ILT | ||||
| → | → | → | → | → | → |