| Week 1 | T&L Activities:
Welcome To The World Of TomorrowUnit introductionHow do websites work? How do emails reach your computer? How does the use of computer applications affect your daily life? This unit provides an introduction to the modern online world. Starting with your own experiences, you will extend your knowledge of online services and investigate the technology and software that supports them. You will learn more about a range of services including email, online data storage, collaborative software, search engines and blogging. TASK Learning Aims and Objectives: Online servicesCommunication, real-time information, commerce, government, education, virtual learning environments, business, entertainment, download services Key terms in online communication
Whats an online service? How do i know if im using one!
The devices that you have provided all have some way of accessing the internet be it mobile or other, so when you consider that these devices are able to do this what other devices could be developed to do this?
DISCUSSION TIME!!!
Now that we have briefly looked at the devices that you could use to connect to the internet we should look at how the online services can be and are used.
FACTIOD:
When we look at the Govenment services that are available we can look closer to home! If you consider your local council, these are run by individuals that are linked in some way to central govenment. The policys and legislation this is created by MPS (Members of Parliment) and Lords in parliment are enforced by your council. So all of this information can be found in a couple of areas. These being your local councils web sites and the government site.
EducationThis section of the online services area should be easy for you to recall. You should refer to your past experiances in school and at college. Now that you have been studying at this institution for a number of weeks now you have without a doubt accessed a learning area online. You will have probably been prompted to use your username and password to login. In most cases you will be using Moodle.
We know that there are more than we can list however below are a couple
There are a mixture of VLE's (Virtual Learning Environment) and online websites that allow access to information and learning resources.
BusinessBanking is an area where businesss can access information about thier accounts, they can also send money to others and between accounts, as well as make payments to clients, individuals and companies.
We know that there are more than we can list however below are a couple
There are a mixture of VLE's (Virtual Learning Environment) and online websites that allow access to information and learning resources.
EntertainmentThese services enable the access to the areas that we would consider and enjoyable and pleasing to use. These services can be catagorised in a number of areas.
Download ServicesThese services enable you to gain access to programs, music, information and other. These are most often linked to sites like, Piratebay and other torrent sites, however, we must not forget legitimate and legal sites and services such as iTunes e.t.c
Downloading is widely used by players and user and also machines. When we break down the area of download services we must consider ALL the users, and not limit this to humans.
Online servicesCommunication, real-time information, commerce, government, education, virtual learning environments, business, entertainment, download services Key terms in online communication
We as users of the internet can find that we are in situations where it appears and we don’t even realise it.
When we are look ing at the use and effectiveness of the onilne services we should also consider the business uses. When we in business company's will try to promote themselves and thier products online. This is important as this method can be seen by billions of people accross the world. ACTIVITY:
Other advertising that can be used online is the use of Banners and Pop-ups. Business can register with search engines such as Google, Bing and Yahoo! so that their websites appear high up in a list of keyword searches, this is done by the company paying for links that appear when a user does a search. This can be seen when a search is done by the top two sites having the word sponsored against it.
ACTIVITY:
Banners and pop-ups are a frustration of most web users, whether they are just browsing or looking for something specific. In most situations the banners and pop-up's are annimated so that they draw attention to themselves. These are in most cases distractions from the content of the page and an iratation to the visitor to the pages. Banner and pop-up ads often appear at the top of web pages or pop up on web pages and in
DISCUSSION TIME!!! Email is an alternative option for advertising.
Email in the most part is informative and is used to make contact with individuals to present them with information that could be focused to thier needs, requirements and or interests. This can be both benificial to businesses and to clients however there are common issues associated with this, these could be,
These issues are likely to stop communication reaching individuals. We must remember that the use of this method of communication has areas that the bussiness must consider inorder for it to be effective, these are,
FACTIOD:
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 2 | T&L Activities: Learning Aims and Objectives: Online servicesCommunication, real-time information, commerce, government, education, virtual learning environments, business, entertainment, download services Key terms in online communication
We as users of the internet can find that we are in situations where it appears and we don’t even realise it. When we are look ing at the use and effectiveness of the onilne services we should also consider the business uses. When we in business company's will try to promote themselves and thier products online. This is important as this method can be seen by billions of people accross the world.
Other advertising that can be used online is the use of Banners and Pop-ups. Business can register with search engines such as Google, Bing and Yahoo! so that their websites appear high up in a list of keyword searches, this is done by the company paying for links that appear when a user does a search. This can be seen when a search is done by the top two sites having the word sponsored against it.
Banners and pop-ups are a frustration of most web users, whether they are just browsing or looking for something specific. In most situations the banners and pop-up's are annimated so that they draw attention to themselves. These are in most cases distractions from the content of the page and an iratation to the visitor to the pages. Banner and pop-up ads often appear at the top of web pages or pop up on web pages and in
Email is an alternative option for advertising.
Email in the most part is informative and is used to make contact with individuals to present them with information that could be focused to thier needs, requirements and or interests. This can be both benificial to businesses and to clients however there are common issues associated with this, these could be,
These issues are likely to stop communication reaching individuals. We must remember that the use of this method of communication has areas that the bussiness must consider inorder for it to be effective, these are,
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 3 | T&L Activities: Learning Aims and Objectives: Online communication
Contemporary social mediaIn our society today people with common interests gather together to share their views and opinions as well as create ideas. In many situations people that share these interests form club’s for example, football clubs, hockey clubs, chess clubs and gaming clubs these are not limited to just clubs there are gatherings of groups that create a society where they read, discuss and develop ideas as well as review others that may have been created already, an example is an historical society. However, with the ever increasing use of the internet there has been an impact on the way that we communicate and share information with each other. Online communitiesAnyone that has some computer skills and knowledge can use equipment and services to create a groups or ‘societies’ online using things like blogs. The groups are often known as online communities, which allow users access to a place where people with similar interests can come together discuss and swap their views and opinions. Sometimes the communities exist in a virtual world online. This is an unreal world created by the computer. Popular examples include SecondLife, Twinity and Habbo. The World of Warcraft virtual world a wide covering online community covering a large global area the gaming virtual world supports multi-player gaming enables users to buy, sell and share virtual reality products and equipment between them as well as create loyalty and allegiances between groups.
NetetiquetteWhen using the online world to communicate a special behaviour or etiquette should be used and is often know as netiquette. The use of netiquette is designed to reduce, restrict and prevent abusive online behaviour. These rules are used widely across the internet online areas and if a user is found to be breaking these rules they may be removed from the online communication areas that they are in and in more severe cases reported to the police. Other individuals may also report users to the site admins of the possible breach of the netetiquette rules. Exam Question: What do you understand by the term "Netetiquette" [2]
Create a poster to educate a teenager to the rules of Netetiquette Information exchangesWhen using communities’ members often make available information to its members by the use of contemporary social media, this could be information to gatherings offline, special events that maybe coming up soon that have financial gains, for example discounts, or free previews. Other ways that users are able to share information other than through social media would be via the use of
Exam Question: Which of these is NOT an example of an Information exchange?
DISCUSSION TIME!!!
When we look in to the use of online communication in most parts we think to “Real Time” however online communications can be done in the past and then reused at a later date, this can come in the form of Podcasts. Podcasts are a number of audio or video files that are downloadable from internet sites. These are usually published in episodes of events, this could be a radio shows morning schedule, an example would be that of Radio One or Heart FM. These allow fans of the show to catch up with the music, interviews, news and general chat. This process is also known a vlog when the use of videos are involved. One of the world’s most recognizable vlogs is Youtube.
Communication as we know happens anywhere and at any time, we just have to remember that we are doing it. So when we learn we are communicating, we are just listening or reading more than telling or responding. One of the platforms online that we use to communicate in education is via the use of Virtual Learning Environments (VLE), not to dissimilar to this very site. Within our school communities we come across a number of different VLE’s some noteworthy ones are
The use of these covers a wide range of areas of assessment and communication, the ability for the submission of a digital piece of work that can enable the tutor to explain (Communicate) to the student the areas of success and the areas that require improvements. VLE’s a not limited to just the submission of work but also enabling the use of poles, survey and discussion forums around the work. VLE’s also are great for returning to the subject matter at a later time to catch-up or to test knowledge that has been covered in sessions. Socail MediaWe know that this area is one on the most frequently visited web areas on a day to day basis. As mentioned in an earlier “Factoid” approximately 2.8 billion social media accounts are active, that is increadable considering that the reported user levels of the internet are reported to be 3.01 billion. DISCUSSION TIME:
Social Networking
Create your own Linked In profile using your own private email (as any school or college email may be unaccessible once you leave) consider how this platform promotes your self and your skills and qualities. It is worth remembering that this could be a window in to employment as employers review your social presence online as a way to see if your the right candidate for them.
Instant MessagingAs we have covered previously, Instant messaging enables a real time communication between users, this could be used in the business area of finance where a stock broker sends a message to another broker to purchase a number of shares in a company, or it would be a message between you and a bank clerk to a question about the interest rates on your bank account.
Discussion time, in groups consider what are the risks of instant messaging are? Have you ever had a situation where you have found it to be misused? What protection measures could you use? What support is there?
Voice over Internet Protocol (VoIP)The use of VoIP over the past 10 years has increase dramatically. VoIP uses digital signals of voice and video and sends these over the Internet between a number of points, this enables the users to have a conversation from anywhere in the world.
DISCUSSION TIME!!!
Email in the most part is informative and is used to make contact with individuals to present them with information that could be focused to thier needs, requirements and or interests. This can be both benificial to businesses and to clients however there are common issues associated with this, these could be,
These issues are likely to stop communication reaching individuals. We must remember that the use of this method of communication has areas that the bussiness must consider inorder for it to be effective, these are,
Discussion Time: in groups of 2, discuss the impact that emails have on a company if misused. What about the risks to users of email. What could you and a company do to reduce these risks?
FACTIOD: Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 4 | T&L Activities: Learning Aims and Objectives:
Exam Time: You will now attempt a mock of an exam that uses similar questions to that in the actual exam.
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 5 | T&L Activities: Learning Aims and Objectives: Online communication
Contemporary social media In our society today people with common interests gather together to share their views and opinions as well as create ideas. In many situations people that share these interests form club’s for example, football clubs, hockey clubs, chess clubs and gaming clubs these are not limited to just clubs there are gatherings of groups that create a society where they read, discuss and develop ideas as well as review others that may have been created already, an example is an historical society. However, with the ever increasing use of the internet there has been an impact on the way that we communicate and share information with each other. Online communities Anyone that has some computer skills and knowledge can use equipment and services to create a groups or ‘societies’ online using things like blogs. The groups are often known as online communities, which allow users access to a place where people with similar interests can come together discuss and swap their views and opinions. Sometimes the communities exist in a virtual world online. This is an unreal world created by the computer. Popular examples include SecondLife, Twinity and Habbo. The World of Warcraft virtual world a wide covering online community covering a large global area the gaming virtual world supports multi-player gaming enables users to buy, sell and share virtual reality products and equipment between them as well as create loyalty and allegiances between groups.
Netetiquette When using the online world to communicate a special behaviour or etiquette should be used and is often know as netiquette. The use of netiquette is designed to reduce, restrict and prevent abusive online behaviour. These rules are used widely across the internet online areas and if a user is found to be breaking these rules they may be removed from the online communication areas that they are in and in more severe cases reported to the police. Other individuals may also report users to the site admins of the possible breach of the netetiquette rules. Information exchanges When using communities’ members often make available information to its members by the use of contemporary social media, this could be information to gatherings offline, special events that maybe coming up soon that have financial gains, for example discounts, or free previews. Other ways that users are able to share information other than through social media would be via the use of
DISCUSSION TIME!!!
When we look in to the use of online communication in most parts we think to “Real Time” however online communications can be done in the past and then reused at a later date, this can come in the form of Podcasts. Podcasts are a number of audio or video files that are downloadable from internet sites. These are usually published in episodes of events, this could be a radio shows morning schedule, an example would be that of Radio One or Heart FM. These allow fans of the show to catch up with the music, interviews, news and general chat. This process is also known a vlog when the use of videos are involved. One of the world’s most recognizable vlogs is Youtube.
Communication as we know happens anywhere and at any time, we just have to remember that we are doing it. So when we learn we are communicating, we are just listening or reading more than telling or responding. One of the platforms online that we use to communicate in education is via the use of Virtual Learning Environments (VLE), not to dissimilar to this very site. Within our school communities we come across a number of different VLE’s some noteworthy ones are
The use of these covers a wide range of areas of assessment and communication, the ability for the submission of a digital piece of work that can enable the tutor to explain (Communicate) to the student the areas of success and the areas that require improvements. VLE’s a not limited to just the submission of work but also enabling the use of poles, survey and discussion forums around the work. VLE’s also are great for returning to the subject matter at a later time to catch-up or to test knowledge that has been covered in sessions. Social Media We know that this area is one on the most frequently visited web areas on a day to day basis. As mentioned in an earlier “Factoid” approximately 2.8 billion social media accounts are active, that is increadable considering that the reported user levels of the internet are reported to be 3.01 billion. DISCUSSION TIME:
Social Networking
Instant Messaging As we have covered previously, Instant messaging enables a real time communication between users, this could be used in the business area of finance where a stock broker sends a message to another broker to purchase a number of shares in a company, or it would be a message between you and a bank clerk to a question about the interest rates on your bank account.
Voice over Internet Protocol (VoIP) The use of VoIP over the past 10 years has increase dramatically. VoIP uses digital signals of voice and video and sends these over the Internet between a number of points, this enables the users to have a conversation from anywhere in the world. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 6 | T&L Activities: Learning Aims and Objectives:
DISCUSSION TIME!!!
Email in the most part is informative and is used to make contact with individuals to present them with information that could be focused to thier needs, requirements and or interests. This can be both benificial to businesses and to clients however there are common issues associated with this, these could be,
These issues are likely to stop communication reaching individuals. We must remember that the use of this method of communication has areas that the bussiness must consider inorder for it to be effective, these are,
FACTIOD: Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 7 | T&L Activities: Learning Aims and Objectives: Implications of online communication
DISCUSSION TIME!!!
Social networking Social networking websites have developed, evolved and ultimately changed the way that we communicate with each other. The use of Social media has enabled people to communicate interactively and in real time from anywhere across the world. Groups of people can exchange and share information quickly a benifit of this is cost as the only cost is that of a broadband connection. Social networking provides a great way of staying upto date with friends and businesses.
Instant Messaging Instant messaging is used widely and is a great way to exchange text messages, this is an alternative to the telephone conversations and the costs are very much cheaper. Messages are sent in real time, and the responses are received instantaneously.
Voice over Internet Protocol (VoIP) Voice over Internet Protocol (VoIP) allows users to interact in real time over the internet using voice and video messaging. Skype is one of the most widely used VOIP services used across the globe. When used across the globe via businesses programmes like Skype can enable companys to reduce thier travel costs, travel time (and therefore loss of productivity during this time) and the cost of hiring a venue. Cloud and Cloud ComputingThe term Cloud computing means the use of a computer service on other company's computers, these are commonly known a hosts. There are a number of well-known hosting companies that offer cloud computing these include, Microsoft and Google. Cloud users are able to use software access data and storage on the host computers, which will be at a remote location, the joy of this is that those with PC's and systems that are limited can still use the software, storage and data. To access these services users will use a web browser or mobile app, without ever directly accessing the servers that the information is stored on. cloud storage is related to cloud computing – it is where only the storage, access and retrieval facilities are provided by the host provider, often via the internet. The term ‘the internet of objects’ is credited as first being used by Kevin Ashton in 1999. Find out about the context in which Ashton used the term. Is it still relevant today? FACTIOD: Ubiquitous computing systemsWe must first understand what Ubiquitous means! ‘existing everywhere’. Processors can be embedded in any device, including clothing, appliances, vehicles, buildings and people, to connect them to the internet so that the data generated by the processors will be readily available. FACTOID: DISCUSSION: Using your research skills, explore the following areas; Because we now know what the term Ubiquitous means lets look in to is application.
In groups of 2, create a list of the Ubiquitous computing systems you interact with in a single day. Some of the most common elements of Ubiquitous computing are in action in the videos below.
RFIDThe use of modern technology in our day to day activities are suprising, you will have used it today to enter the school, college and even work or as part of your journey. DISCUSSION: Over the past few decades this technology has been used to enable people to make the crossings over and under the Thames as trouble free as they could via the use of the Darttag. This device that was located in the frount of the car acted like a key, so when a car got close to the barrier, the sensors would receieve a responce from the RFID chip to say that this car is owned by an individual that has pre-paid for the crossing, so allow them through.
Problems with ubiquitous computing
Privacy issues: Probably the most important problem is that ubiquitous computing environments pose serious privacy risks. By watching everything a user does these systems have the potential to leak all our actions, preferences, and locations to others unknown to us, now or in the future. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 8 | T&L Activities: Learning Aims and Objectives: The Internet
The Internet, the digital platform that none of us can bare to be without! However it is worth remembering that the internet is not limited to the web, it includes email, data storage and wireless networking.
We must first fully understand how the internet works before we go any further. The internet comprises of a number of interconnected computers, these systems have software installed on them that enables them to view information (client) or to present information (server). Now that we have some understanding to the connections between servers and the clients we should look to the terms and vocabulary that are commonly used. Point of Presence (PoP) This term relates to the location or presence of the required hardware that is used to allow the users of the internet to connect too the internet. At this point ISP, or Internet Service Providers may have a number of PoP's in small geographical area to ensure good internet access.
Network Access Point(NAP) This term relates to the networks on the internet that enable ISP's to interchange their connections with other ISP's Service Providers may have a number of PoP's in small geographical area to ensure good internet access. Internet Protocol (IP) This protocol is used to move packets of data across the internet. The packets is an individual unit that information and data is carried in, these packets of data have other elements to them that enable the required information to know where to return to and in what order it is to be put back together again in. It is worth remember that the data that is sent back to a user from a server can take different routes to other bits of the data sent back. Transmission Control Protocol (TCP) This is a protocol that is used to take the information from users applications or programs to then pass it on to the IP to send it across the internet. This process is repeated at the destination but in reverse. Because of the direct link and nature of this protocol to the Internet Protocol (IP) they are combined to create TCP/IP File Transfer Protocol (FTP) This protocol is the stanard used to enable the transfer of files between two computer systems. This allows people like web developers to create a website on thier computers and then once happy for them to send it to the web server using FTP. These web servers then host the website for the worlds users to access.
Internet Service Provider (ISP) Internet Service Providers are the companys that allow users to access the internet. These company's offer packages to users enabling them play games, read the news or to send emails. This then allows users to pay for the type of users that they are, heavy, mild or occasional users. ACTIVITY:
Internet Make-up
The internet is a large network that is made up of lots of networks. These networks are inter-connnected to create large networks that allow users to navigate through to reach the location of the information, or web page that they require.
Server Servers are used to store data and files. These machines are used direclty to serve other computers called clients. These Machines run specific software to enable the connection of other machines to it and to send information to them from it.
Client These are computer systems that are used to connect to servers to enable access to files, printing and email. Router This is a hardware device that is used to connect to the internet. This device takes the messages recived back from the internet and routes it to the device that requested it. Routers have other operations that look at security and check that the information or "packets" of data are not virues or trojans. Connecting Backbone This is the connection between large networks on the internet and other networks in other areas. The internet covers the globe and some countrys are islands and require the connection of a physical cable to enable this connection.
How to connect to the internet?Broadband Connection Now that we have some understanding to the make up of the internet and the structure of the most common part of the network lets look at how we can connect to the internet. Wireless Connection Wireless connections to the internet are where the device requesting the information is not connected physically to another element of hardware. This is common of mobile phones and some tablet computers. The benefit of using wireless connections are that the users is able to move about with the device to an number of location, and it not reliant on a static piece of hardware. The drawbacks of this is that a number of locations are outside of the wireless signal, the speeds in which the data is sent can be extreamly slow and the connections are less secure than that of wired. Dial-up Connection Now that we have some understanding to the make up of the internet and the structure of the most common part of the network lets look at how we can connect to the internet. ACTIVITY: FACTIOD: Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 9 | T&L Activities: Learning Aims and Objectives: World Wide Web
The World Wide Web as we know it is credited to a single persons visions and commitment to enable people to have access to information in an easy linked way. Sir Tim Burners-Lee an Englishman created the core elements to enable the hosting and sharing of information using a number of protocols. When we look in to webpages we can see that these pages are linked together via the use of Hyperlinks, these are a kind of string that allows some one to follow the string to another page. Websites are made up of a number of these links and some of them can be to webpages that have been created by other people. As mentioned earlier, users/clients use special software in order to request these files and webpages, these are often referred to as Browsers. These programs interpret the information that is sent to them by the webserver and present the webpages in a form that we can recognise. The information that is sent by the webserver is the webpages code, this is known as HTML or HyperText Mark-up Language. This code is created by the user/owner of the webpage and uses Tags to create the pages. Theses HTML tags always start with a bracket < and then close with a bracket > and example of this is in the box below. There a lots of HTML tags that are used to create a webpage below is a small example of a few of them It is worth noting that most HTML tags have what are known as closing tags as per the example below a paragraph
URLSAs discussed earlier one of the protocols that is used in the use of Surfing the Web is the use of a URL, these are used to direct a user to the correct location of a website. Lets look a little deeper, an owner of a website will use a computer to Host the website that they have created, this computer will have an address, this address is known as an IP address (this has been covered earlier, week 8) this address like your home address is unique, however the address is a IP number which could be something like 210.68.187.250 this number has no meaning and could be easily forgotten, so we use a service called a DNS or Domain Name Service that links the IP addresses to a written address like http://www.MyStudentSite.co.uk. Search EnginesSearch engines are a great way to find information from across the web, the search engine acts like a form of yellow pages or Thompson Local.
There are number of popular search engines that are available, these are Bing, Google, Ask however there are a number of alternatives to these popular engines, and also there are a number of engines that were popular however they fell out of favour. ACTIVITY: create a time line of web browsers. The search engine will take a word, sentence or phrase and look over its database of web pages and it will look for the keywords and then present the user a list of the possible matches that have been found based on the search. In order for the search engines to gather this data they have a few tools that is uses to gain these vital references. Search engines use of Crawlers to read the webpages content and create a list of common words and terms that occur on the page, these crawlers then return the information to the search engines database to be indexed like a library system. These crawlers are also known as Web spiders, Web crawlers and bots. These are all automated and have no human involvement. Other ways that websites can appear on search engines, and to be listed at the top of the page is by paying to search engine to list them on the top of the criteria when a user enters a Keyword. These are known as sponsored links. Email – Purpose and Use
What is Email? Often referred to as Electronic mail, email is a digital letter sent to someone that may require information or may need to be aware of information that is being discussed and sent. Email systems have a number of points to which are important and essential to enable users to send the mail. When looking at the image above we can see that users have a number of inputs and buttons that can be used and are required to be used to send the message. Let’s look in to them with a little more focus.
Create an infographic that highlights and discusses the advantages and disadvantages of emails. Include the use of CC and BCC and the capabilities of Email.
When we use email we must consider a number of areas and be aware of potential disadvantages of using such a system. We know that we are able to send emails that have attachments to them, however these can spread viruses. We can send these emails to multiple people at once, this could open up more users to virus infections quickly It is faster that Post or Snail mail as it became to be known. How Email works
An email account uses a number of different Protocols to send and receive emails, these are;
Data Exchange Packet SwitchingThe term packet switching refers to the process of data being broken in to parts called packets before it is sent over a network or the internet and then how it is reassembled when it gets to its destination. When we look at the packets each will have a section of the data contained within it, these are limited in their size. A packet will have the following information contained within it; Error Control Bits – This part of the packet checks to see if the packet has been assembled correctly. The life of a packet VOIP and Packet SwitchingAs we have covered in earlier sessions VOIP or Voice Over Internet Protocol is a great way to communicate over the internet. Because VIOP data is sent over the internet these data packet will need to go through packet switching, however there is a small additional step, VIOP makes use of a thing called CODEC, this term is created from the following two process that are done to the data. Why do we use packet switching, what are the benefits? The use of breaking down the data in to packets means that the file if they were big would not clog up the network as parts of it can be sent a chunk at a time and then once the complete packet group arrives it will construct them back in to the correct order. Using packet switching allows for the users to have an added security element as if a packet is intercepted it only contains small parts of the data in it. There is a disadvantage to this method as if a packet is lost or corrupted during transmission the whole file will not be received correctly. Data Exchange and Transmission ModesWe understand that almost everything that communicates will have a sender and a receiver, this is not only computers it could be phones, printers and remote controls. How these communicate are a little more detailed.
Half-Duplex – Consider a conversation or a question one device/person listens then the other reponds one they have all the information. The conversation can go both ways but cannot transmit at the same time
Simplex – This is a one way conversation, this is common of TV remote controls.
Discuss and find 2 examples for each of the transmission.
Characteristics of Data Transfer
Serial – In a serial connection the information communicated across the connection is sent a bit at a time, this allows the information to be sent over large distances, however this infomation is broken in to parts to be communicated. Wired Transmission MethodsLet’s now look at what ways we can send information between devices using a physical method of connections.
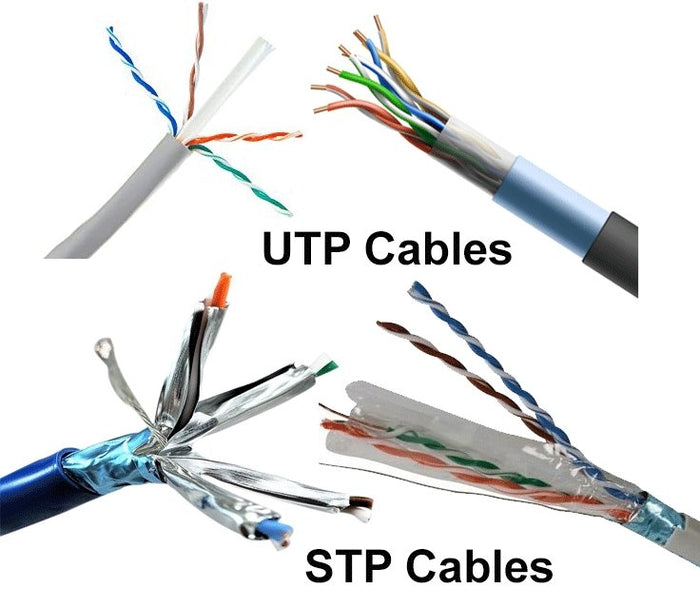
Ethernet Cables
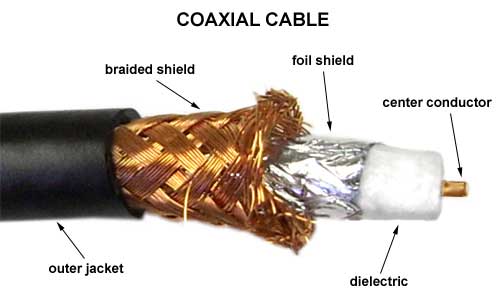
Coaxial
This is commonly used in the connection of TV and aerials, they are very reliable in transferring the TV signals to the TV. This type of communication was previously used in computing before the use of Ethernet cables. Fibre Optic
This is by far the fastest connection that can be used to transfer information. Using light computers send this information down the cables a lightening speeds. This technology is very expensive however and very complicated to install. The cables are made from either glass or high quality plastic. Because the signals sent are light the information can be sent over long distances.These are commonly used in the connections of server on the Backbone of a network. How its made
Wireless Transmission Methods
Let’s now look at what ways we can send information between devices using a wireless method of connections. Infrared
Microwave
This communication transmission uses shortwave to send information. It is one of the most commonly used short range communication methods, it is recognised as bluetooth. Satalite
This is by best for connection, using satalites that are in orbit around the world data can be sent up and down quickly over large geographical areas. Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 10 | T&L Activities: Learning Aims and Objectives: Client-Side ProcessingIn the area of the website development and design the creator/author of the website will use what is known as Client-side processing to enable the use of some code to run on the machine viewing the website. Why is this of value?
Server-Side ProcessingServer side procesing happens once a request has been sent it, this could be an original request for a webpage, or it could be the information to login to the system, things like blog, online commerce sites and online email. The server will have a number of pages that are dynamic that can send a customised webpage back to the user based upon the login details that it has recieved. Server sider processing is brower indepentant so it will not worry what browser the user is using at the other end when it sends its responce.
Databases
As they say in london you are only a matter of feet from a rat, the same is true of databases.
Database RelationshipsDatabases have the ability to make our lives easier, they can tell us things like the current stock levels of a new release of a games or the cost of a train ticket between two locations. This data however is not stored in a single location/table, it is stored acorss a number of them.
Database management systems or DBS systems programs allow you to create databases. Databases use a structured query language or SQL which is a high-level language.
DISCUSSION TIME!!! FACTIOD: Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 11 | T&L Activities: Learning Aims and Objectives: Possible threats to dataDue to the very nature of data being transferred across the Internet data is at risk of attack. These attacks can come in different forms.
Opportunist Threats Opportunist threats where people use opportunities to intercept or gather data. These sorts of attacks can come when a user leaves their computer system logged on and then physically move away from the terminal for another person to then sit at the terminal and for them to look at the data that is open. This data could be changed, duplicate and removed or deleted from the users area. The user may be completely oblivious to this attack until it's too late.
Computer viruses
computer viruses are small programs that have the ability to replicate themselves and for them to spread themselves are crossed a small or large network and even over the Internet. These systems can change personal files and key computer system files this could then result in a computer system not working correctly. Some computer viruses use e-mail to send themselves to other people that you may have communicated with. Malware this sort of threat is usually found when a unsuspecting user downloads or opens a program that has been created to look like a trustable application, file, image or video that upon opening enables malicious programs to install themselves onto the system in some cases without the user ever knowing. Some of these examples include annoying features added to Internet Explorer or web browsing software, pop-ups that are selling on required materials. phishing
This is a common threat to users these days as more and more e-mails and telephone scams are trying to gain access to sensitive data about you so that they can then use this information in some cases fraudulently or in some cases to steal identities. Some of these experiences can be an e-mail that looks like a request from your bank to update your personal information through a link that they have provided that takes you to a webpage that looks identical to the original bank webpage, some users will not notice small differences in the appearance of the webpage as it can be very convincing. Users inputs sensitive information into these fake websites and the owners of the websites then use this information to either gain access to your accounts or for them to use it to set up credit cards and loans in your name without you knowing. A good way to ensure that you are protected against this issue would be the use of software provided by the bank to be installed on your web browser. Always look for the closed padlock symbol in the web browser as this will show that the website you are navigating to is a secure one and that you are able to check the certification of that website. Accidental damage there are other non-underhand threats to data and this can come in the form of accidental damage. These salts of occurrences can happen when data is destroyed due to mechanical failure such as corruption of a hard drive, or it could come in the form of natural disasters such as a computer being on the floor of a room that is susceptible to flooding. A method of ensuring that this potential loss of data is reduced would be to create a number of different backups of the data and to store these separately from the location of where the original is.
Importance of securityAs we've mentioned in the above area data is valuable data can be taken from any system that is not protected with sufficient security software or measures. No computer is 100% safe so caution should be considered when dealing with sensitive data. Companies and organisations that deal with online data has to do buildup a good reputation of being able to keep data safe and secure, the source companies will pay hundreds of thousands of pounds to ensure that all the data it holds is kept securely. However it is worth remembering the issues that some of the large companies have experienced recently with loss of security to their systems, one such example was the access by hackers to the talk talk customer database. This system was hacked by 15 and 16-year-old boys that ended up being arrested a number of days after the issue was brought to light. Other such instances would be the attack on Sony's PlayStation network where personal data was stolen including bank account details user account IDs and other sensitive personal information. Preventative and remedial actionsso as mentioned in the previous area we need to ensure that we protect our data by using preventative measures and software. Some of these are listed below. Physical barriers.
A physical barrier to protect information could be the use of a set process that requires anybody that his leaving a computer system to be aware that they are to lock their machine whenever they move away from the terminal. In the case of environmental threats it would be wise to take backups of Baker on a regular basis, if the location of the system could be changed to move the system to a safer location, this could be in a first-floor room within the building rather than in the basement of a building. Access levels. Users are able to set the access or privileges of a user so that they are unable to gain access to information that is not relevant to them so you are therefore removing the ability for someone to steal data that is not necessary for the user to know. Firewalls
Files are devices that can be hardware and software that monitor all information that is coming into a network or over a network from devices this device or software stops anything that it deems to be harmful so that it can reduce the opportunity of a virus or Trojan horses gaining access to the system. This software and hardware also enables a company to restrict the access to known websites that are of potential threats to the company's systems these could be things like torrents. Backups and recovery
It is essential that this any company and individual create backups of all of their data onto external devices so that if a virus or the threat of corruption to the original data happens that they are in a position where they can restore this information on to another or the same system. Backups are often taken by large corporations and organisations and in some cases these can be done hourly in other situations they may be taken daily ,these backups can be held for as long as the company or organisation or person Dean appropriate. It is well worth remembering that a backup gives an opportunity for a person to rollback to certain versions of files operating systems and programs to allow them to get to a version that may not have been affected by a virus or Trojan, this then reduces the amount of data lost. So as I say to all my learners trying keep free versions of your work this then means that if you have a version that is lost you can roll back to the next version before that if that version was infected by a virus you know that you can restore to a 3rd copy which may not be as advanced as the other 2 but were unable you to have a point where you have not lost all of your work. Backups can be run by assistance that will do a number of different forms of backup, these are,
Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → | |||||||||||||||
| Week 12 | T&L Activities: Learning Aims and Objectives: Files that support this week | English:
|
Assessment:
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria. |
Learning Outcomes:
|
Awarding Organisation Criteria:
|
|||||||||||||||
| Maths:
|
||||||||||||||||||||
| Stretch and Challenge:
|
E&D / BV | |||||||||||||||||||
| Homework / Extension:
|
ILT | |||||||||||||||||||
| → | → | → | → | → | → |









.jpg)
















.png?width=200)