week 6
R10.6 Risk mitigation controls to prevent threats to digital systems:
• National Cyber Security Centre (NCSC) Cyber Essentials:

The Cyber Essentials scheme is a UK government-backed certification managed by the National Cyber Security Centre (NCSC). It helps organisations of all sizes protect themselves against a wide range of common cyber threats. Cyber Essentials focuses on five key technical controls, each of which plays a vital role in securing systems and data.
ðŸâ€Â 1. Firewall to Secure Internet Connections
Firewalls act as a barrier between your network and the wider internet. They filter incoming and outgoing traffic based on defined rules, blocking potentially harmful data from entering the system. A properly configured firewall prevents unauthorised access and controls communications to and from the internet.
A small London-based architecture firm installed a boundary firewall with strict rules on incoming ports. After doing so, they detected and blocked multiple scanning attempts from foreign IP addresses that had previously gone unnoticed.
Case Study:
In 2020, a regional law firm in Manchester reported several intrusion attempts via remote desktop ports. After deploying a firewall with geofencing features, they saw a 95% drop in attempted unauthorised access from outside the UK.
Further Reading:
NCSC - Firewalls and Internet Gateways
🛠︠2. Choose the Most Secure Settings for Devices and Software
Default configurations on devices and applications are often designed for ease of use rather than security. Securing these settings includes disabling unused accounts and services, enforcing strong password policies, and enabling security features like encryption.
An online retailer in Leeds changed default admin usernames and disabled unnecessary ports on their routers and software. This reduced their vulnerability surface and prevented an exploit targeting default login credentials used in a recent phishing campaign.
Case Study:
A fintech startup in Bristol was targeted by attackers who exploited the default configuration of a cloud-based database. After hardening their configuration and using encrypted connections only, the attack was no longer effective.
Further Reading:
NCSC - Secure Configuration Guidance
👤 3. Control Access to Data and Services
Limiting access ensures that only authorised individuals can access sensitive data or systems. This involves using role-based access control (RBAC), multi-factor authentication, and keeping user accounts to a minimum.
A marketing agency in Birmingham implemented RBAC, ensuring junior staff could not access client billing information. As a result, a phishing email that tricked a new employee failed to give attackers access to financial records.
Case Study:
In 2021, a logistics firm in Glasgow suffered a ransomware incident after a compromised intern account accessed admin-level services. The company reviewed its access controls and implemented the principle of least privilege, reducing future risk significantly.
Further Reading:
NCSC - Access Control Guidance
🦠4. Protection from Viruses and Malware
This involves using anti-malware software, safe browsing tools, and application whitelisting. The goal is to detect and neutralise malicious software before it can damage systems or steal data.
A recruitment company in Newcastle introduced endpoint protection software that isolated and flagged a malicious attachment in a fake job application email. Prior to this, their systems were vulnerable to such attacks.
Case Study:
A Scottish engineering firm unknowingly downloaded a malware-laced invoice. Their malware protection tool identified suspicious behaviour and quarantined the file. The tool’s behaviour-based detection prevented data loss.
Further Reading:
NCSC - Malware Protection Guidance
🖥︠5. Keep Software and Devices Up to Date
Software updates (patches) fix vulnerabilities that hackers can exploit. Outdated software is a leading cause of data breaches. Ensuring automatic updates and replacing unsupported software is essential.
A London-based consultancy firm enabled auto-updates on all endpoints. When a major vulnerability in Microsoft Outlook was disclosed, their systems were already patched before hackers began widespread exploitation.
Case Study:
In 2022, a retail chain in Wales delayed patching a known flaw in their e-commerce platform. Attackers used the vulnerability to inject code and steal payment data. After this incident, the company adopted strict patch management policies and automated update deployment.
Further Reading:
NCSC - Keeping Devices and Software Up to Date

Cyber Essentials Self-Check Simulation
Imagine you are the IT support technician at a fictional small business called BrightSpark Media, which handles client videos and sensitive marketing data. The company is considering applying for Cyber Essentials certification.
🧾 Your Mission: You have been asked to carry out a Cyber Essentials readiness check. Complete the checklist below and then write a short report (around 200 words) outlining what BrightSpark Media must do to meet the Cyber Essentials requirements.
Checklist (Answer YES or NO):
1. Do all devices use firewalls with strict rules configured?
2. Are all default passwords and admin accounts disabled or renamed?
3. Is access to financial files restricted to senior staff only?
4. Is antivirus or anti-malware software installed on every device?
5. Are updates automatically applied to all software and devices?
6. Do you use two-factor authentication for remote access?
7. Is unused software regularly uninstalled from all systems?
anti-virus and anti-malware software
Firewalls:
o software
o hardware
Intrusion detection and prevention systems
Encryption:
o purpose
o process
o protocols
The efforts of those that worked at the famous Bletchley Park site are suggested to have helped shorten the lenght of the second world war by a number of years. Its now your turn to attempt to break the code. Using the link to the Bletchley Park resource below break the code and find out the message.
Code Breaker
User access, policies and procedures:
(Part of Risk Mitigation Controls to Prevent Threats to Digital Systems)
Digital systems like school networks, business IT systems or online platforms are always at risk from threats like hacking, viruses, or people accessing things they shouldn’t. To help stop these threats, organisations use user access controls, policies, and procedures. Let’s break this down into two key areas:
Permissions
What are permissions?
Permissions are rules that decide what each user is allowed (or not allowed) to do on a system. Think of it like having different keys to open different doors. Not everyone should be able to unlock every door!
Why are permissions important?
They help stop unauthorised users from accessing private or sensitive information. If someone only needs to write emails and use Word, there’s no reason they should be able to access finance files or system settings.
Examples of permissions:
-
A student can log in and use Word and PowerPoint but can’t install new software.
-
A teacher might be able to access class folders and mark books, but not see payroll data.
-
An IT technician might have full admin access because they need to maintain the system.
How this helps prevent threats:
-
Stops users from making harmful changes by accident.
-
Blocks hackers from easily moving around the system if they do get in.
-
Reduces the damage if someone’s login details are stolen.
2. IT User Policies
What is an IT user policy?
It’s a set of rules that explains how users should use the organisation’s IT systems. Everyone who uses the system must agree to follow these rules.
What do these policies usually include?
-
Acceptable Use Policy (AUP): What you can and can’t do on the network. For example, not downloading dodgy software or visiting unsafe websites.
-
Password Policy: Rules for creating strong passwords, how often to change them, and not sharing them with others.
-
Data Protection Policy: How to handle private data safely, like student records or customer information.
-
Email and Internet Use: Guidelines to avoid spam, scams, and wasting time online.
How this helps prevent threats:
-
Educates users on safe behaviour.
-
Reduces the chance of someone accidentally causing a security problem.
-
Makes it easier to identify and deal with rule-breakers.
Example situation:
If a student downloads a game full of malware onto a school computer, they’ve broken the AUP. Because they agreed to the rules, the school can take action and also knows where to look to fix the problem.
Staff training and CPD (continuous professional development):
o human firewall
Back-ups:
o full
o incremental
o differential
Software and system maintenance:
(Part of Risk Mitigation Controls to Prevent Threats to Digital Systems)
Keeping digital systems safe and working properly isn’t just about firewalls and antivirus software — it also depends on good maintenance. Just like a car needs regular check-ups to keep running smoothly, computer systems need regular updates and care to protect them from threats.
Let’s break this down into three key areas:
1. Importance of Latest Software Updates
What are software updates?
Software updates are new versions or improvements made to programs and systems you use — like Windows, antivirus software, web browsers, or apps.
Why are they important for security?
-
Fix security flaws: Hackers are always looking for weaknesses in software. Updates often fix these gaps before they can be used to attack the system.
-
Improve performance: Updates can also make software run better and smoother, which reduces system crashes that might be exploited by attackers.
-
New features or tools: Sometimes updates add tools that make it easier to manage security or improve user experience.
Example:
If a computer is using an old version of Windows that hasn’t been updated in months, it may be missing vital security fixes, making it an easy target for hackers or viruses.
2. Scheduled Maintenance
What is scheduled maintenance?
This is when system checks, updates, backups, or clean-ups are planned and carried out at specific times – usually when fewer people are using the system, like overnight or on weekends.
Why is it done?
-
To apply updates without interrupting important work.
-
To check that everything is working as expected.
-
To test backup systems in case something goes wrong in the future.
-
To clean up temporary files, unused software or fix minor bugs.
How it helps with risk prevention:
-
Keeps the system running smoothly, reducing chances of crashes.
-
Makes sure systems are always up to date and less vulnerable to attacks.
-
Helps detect problems early before they become serious threats.
Example:
A college IT team might schedule maintenance every Saturday at 3am to update antivirus definitions and apply system patches — so students and staff aren’t affected during class time.
3. Interruption to Service
What does ‘interruption to service’ mean?
It means the system or software might be temporarily unavailable while maintenance or updates are being carried out.
Is this a bad thing?
Not always! Short interruptions are often necessary to protect the system in the long run. It’s better to plan a short break in service than deal with a major crash or a cyberattack.
Why it's important to manage this:
-
Users need to be told in advance so they can save their work and plan around it.
-
Helps prevent frustration and confusion.
-
Ensures updates or maintenance can be done properly and safely.
Example:
If users are warned that the system will be down between 1am and 3am for updates, they won’t try to log in during that time — and the IT team can work without interruption.
Air gaps
Honeypot
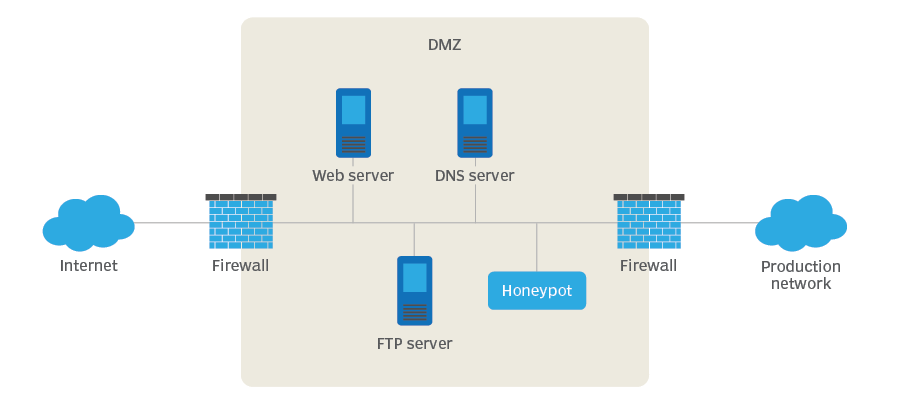
A honeypot in cybersecurity is a decoy system or resource set up to attract cyber attackers. It mimics a real system (e.g. a vulnerable server or database) but is isolated and monitored. The goal is to observe how attackers behave, learn from their methods, and gather intelligence without risking actual systems.
Key Features:
-
Looks like a real target (e.g., a login page, unpatched system).
-
Isolated from critical infrastructure.
-
Heavily monitored and logged
Virtual private networks (VPNs)
What is a VPN, and how does it work?
Demiliterised Zone (DMZ)
Last Updated
2025-05-20 15:31:36
English and Maths
English
Maths
Stretch and Challenge
Stretch and Challenge
- Fast to implement
- Accessible by default
- No dependencies
Homework
Homework
Equality and Diversity Calendar
How to's
How 2's Coverage
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria.
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria.
Links to Learning Outcomes |
Links to Assessment criteria |
|
|---|---|---|
Files that support this week
Week 5→
Next 5Week 6→
Next 6Week 8→
Next 8←
Prev5