week 7
R10.7 The process and protocols of internet security assurance.
Processes:
Installation and configuration of firewalls:
The use of firewalls within an organisation is a key to the protection from both external and internal threats. The more obvious is external attempts to gain access to the internal network to access sensitive data or functions. Firewalls can be both software and hardware, most commonly used are software based, typically found within a router.
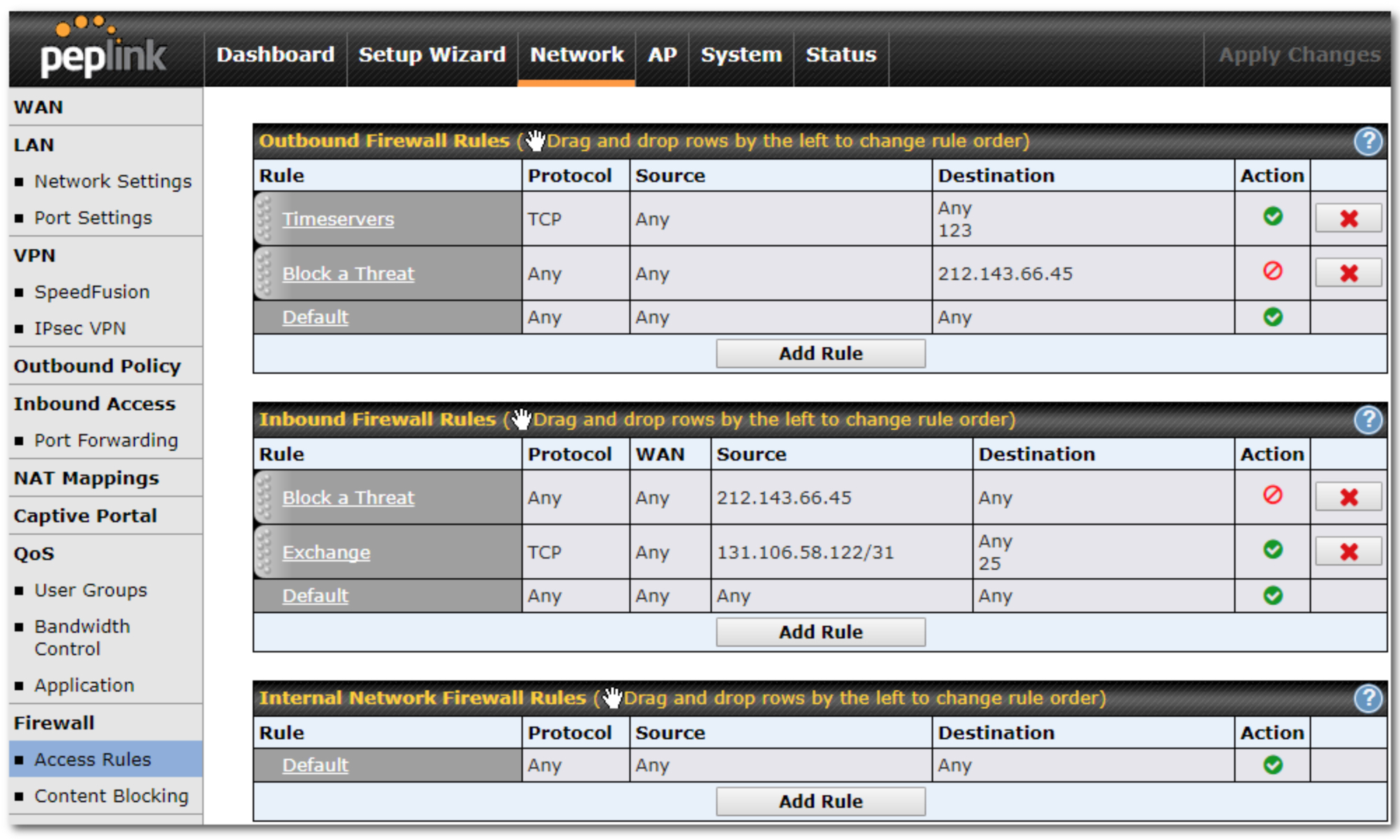 As you can see from the image above the firewall can restrict network and internet traffic and if needed redirect it to a specific attached network server or device.
As you can see from the image above the firewall can restrict network and internet traffic and if needed redirect it to a specific attached network server or device.
These firewall can be bespoke to the device and vendor created, however there are open source options available such as , XXXXXXX. Microsoft also offer thier own firewall options using Microsoft Defender.
o inbound and outbound rules:
â–ª traffic type rules
â–ª application rules
â–ª destination and source rules
Network segregation:
VLANs
VLAN stands for Virtual Local Area Network.
A VLAN is a way to split one physical network into several smaller, virtual networks. Even though all the devices are connected to the same switches and wires, VLANs make it so that certain devices can only talk to others in the same group, as if they were on totally separate networks.
Think of it like dividing a school building into different classrooms — the students are all in the same building, but they stay in their own rooms for lessons.
Why Use VLANs?
Here’s why organisations, especially schools and colleges, use VLANs:
1. Security
-
VLANs stop sensitive data from being shared with people who shouldn’t see it.
-
For example, student computers can be kept separate from the admin office network.
2. Better Network Performance
-
If there’s a lot of traffic, VLANs reduce the amount of unnecessary data going to all devices.
-
Devices only receive data from others in their VLAN, reducing “noise” on the network.
3. Easier Management
-
You can group users by department, role, or location (not just by where they’re plugged in).
-
Changes are made with software, not cables.
Education-Based Example: School Network with VLANs
Imagine a secondary school network with the following areas:
| Area | Devices | Why VLAN? |
|---|---|---|
| Admin Office | Staff PCs, printers, servers | Keep financial/student data safe |
| Classrooms | Student PCs, shared printers | Isolate students from admin area |
| IT Support Room | Technician devices, servers | Access to all areas for maintenance |
| Guest Wi-Fi Network | Visitor laptops/phones | Block access to school systems |
Each group is put into its own VLAN:
-
VLAN 10 – Admin
-
VLAN 20 – Students
-
VLAN 30 – IT Support
-
VLAN 40 – Guests
This setup means:
-
Students can’t see or access admin files or devices.
-
Guests can't snoop around on the student or admin network.
-
The IT department can still access all VLANs (using special configuration).
Create VLANs in a School Network
Create a simple school network in Cisco Packet Tracer and configure VLANs to separate admin, students, and guests.
What You’ll Need in Packet Tracer:
1 Switch (2960)
3 PCs:
Admin-PC
Student-PC
Guest-PC
Cables (copper straight-through)
Using the steps below create a set of VLANs
Steps
1 - Connect Devices:
-
Plug all 3 PCs into the switch (e.g. FastEthernet0/1, 0/2, and 0/3).
2 - Label the PCs for clarity.
3 - Go into the Switch CLI and create VLANs:
enable
configure terminal
vlan 10
name Admin
vlan 20
name Students
vlan 30
name Guests
4 - Assign ports to VLANs
interface fa0/1
switchport mode access
switchport access vlan 10
exit
interface fa0/2
switchport mode access
switchport access vlan 20
exit
interface fa0/3
switchport mode access
switchport access vlan 30
exit
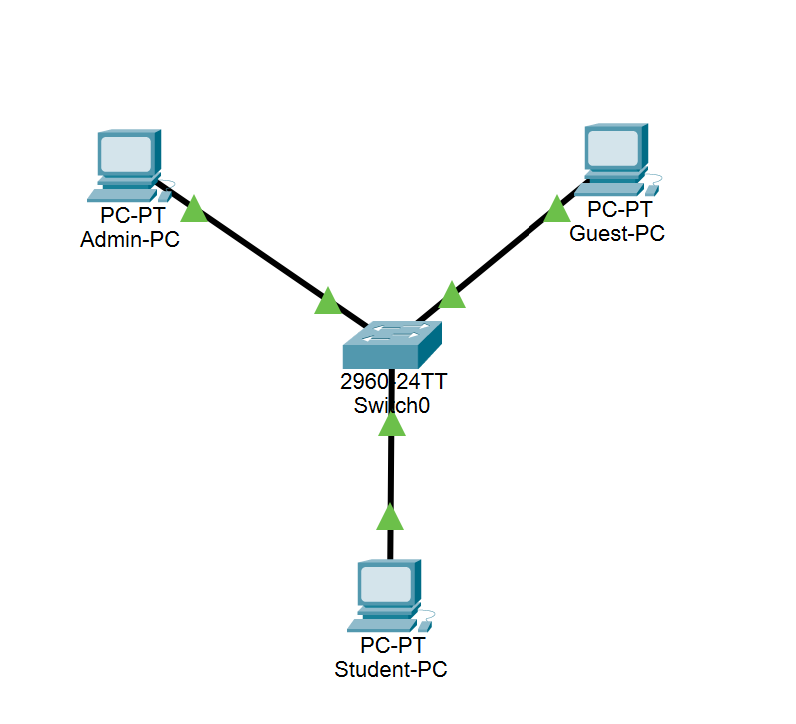
5 - Test the network:
-
Try pinging from Student-PC to Admin-PC. It should fail.
-
Try pinging from Student-PC to Guest-PC. It should fail.
-
Devices on different VLANs can’t talk unless a router or Layer 3 switch is used.
o physical network separation
Physical network seperation is oftern more expensive as dedicated equipment maybe required. Consider a school or college organisation, there are student machines, staff machines and office/admin machines, each of these would require their own switch to allow them to communicate. The 3 networks would then sit within the organisation without access to each other. In principle this works well however there may be the need for access to shared resources, so an additional switch may be required to join all the networks together, at this point further configurations would be required to enable them to talk to each other.
o offline networks
Offline networks are closed networks that do not have access to any internet or external services. The use of these networks may appear in organisations where systems are sensitive and must not allow for any external influences. An air gapped systems is an example of an offline network.
Network monitoring
Network monitoring means watching what's happening on a computer network — like tracking the traffic (data), devices, and users — to make sure everything is working properly and safely.
Think of it like security cameras for a computer network. Instead of watching people, you're watching:
-
Which devices are connected
-
What data is being sent and received
-
Who is accessing what
-
Whether anything suspicious is going on
Why Do We Monitor Networks?
In the same way a school might use CCTV to stop vandalism or bullying, businesses and organisations monitor their networks to prevent cyberattacks, data breaches, or other problems.
Without monitoring, they might not even notice that:
-
A hacker is in their system
-
A virus is spreading
-
Sensitive data is being stolen
-
A device is using way too much internet bandwidth (which could slow everything down)
What Does Network Monitoring Involve?
Here are some of the tools and actions that come with monitoring a network:
1. Traffic Analysis
-
This means checking how much data is moving through the network and where it’s going.
-
It helps spot unusual patterns — like a computer suddenly sending loads of data to a strange website.
2. Alerts and Alarms
-
Monitoring software can send automatic alerts if something looks wrong — for example, if someone tries to log in 50 times in a row (which might mean a brute-force attack).
3. Logs
-
Every device and server keeps a log, which is like a digital diary of everything that’s happened.
-
Network monitoring tools collect these logs and look for signs of trouble.
4. Intrusion Detection Systems (IDS)
-
These are tools that look for unauthorised or dangerous activity on the network, like a burglar alarm for digital threats.
How Does This Link to Internet Security Assurance?
Internet security assurance is all about making sure security controls are in place and working. Network monitoring:
-
Checks if security systems are doing their job (e.g. firewalls, antivirus software)
-
Helps identify problems early, so action can be taken before damage is done
-
Provides evidence — like logs — to show that a company is following proper security procedures
So, it's not just about watching — it’s about proving that the network is safe and secure.
Real-Life Example
Imagine you're at college, and someone tries to hack into the Wi-Fi network. If the IT team is using network monitoring tools, they might see loads of failed login attempts or strange traffic at 3am. They can quickly block access, investigate the source, and protect the system before any damage is done.
Without network monitoring, the attack might go unnoticed until it's too late.
Removable media controls
Removable media refers to any storage device that you can easily plug into a computer and take out again. Common examples include:
-
USB memory sticks (also called flash drives)
-
External hard drives
-
SD cards
-
CDs and DVDs
These are really useful for moving files between computers, backing up work, or carrying data with you — but they can also be a big security risk.
Why Do We Need Controls for Removable Media?
Because removable media can:
-
Spread viruses or malware: If someone plugs in an infected USB stick, it could install harmful software onto a computer or even a whole network.
-
Cause data leaks: Someone could copy sensitive files (like customer info or private documents) and walk out with them on a tiny USB drive.
-
Bypass network security: Hackers might use removable media to sneak around firewalls or antivirus software, especially if the device is trusted by the computer.
So, controlling removable media is part of internet security assurance, which is all about keeping data and systems safe from cyber threats.
What Are Removable Media Controls?
These are rules, settings, and procedures that organisations use to manage how removable media is used. Here are some examples:
1. Blocking USB Ports
Companies can use software to stop USB drives from working on certain computers, especially if they're not needed for work.
2. Encryption
If someone has to use a USB drive, it can be encrypted, which means the data is scrambled unless you have the right password or key to unlock it.
3. Antivirus Scanning
Before a device is used, the system might automatically scan it for viruses or malware.
4. Access Control
Only certain people (like IT staff) might be allowed to use removable media. Everyone else is blocked by default.
5. Audit Logs
Some systems track when and where removable devices are used, so if something goes wrong, the IT team can investigate.
Why Does This Matter in Internet Security Assurance?
Internet security assurance is all about proving and checking that systems are protected. That includes making sure:
-
Staff are following the rules
-
Devices aren’t introducing threats
-
Data stays safe
By having removable media controls, a company reduces the chance of a security incident caused by someone plugging in an infected or unauthorised device.
Quick Real-Life Example
Imagine a college laptop is infected by a virus from a student’s USB stick. The virus spreads across the network and deletes important coursework files. If the college had proper removable media controls (like automatic scanning or blocked ports), that might never have happened.
Anti-virus
Managing user privileges
User privileges, also known as permissions, determine the actions a user can perform within a system. These actions can include reading, writing, modifying, or deleting data, as well as accessing specific applications or system settings.
Why Is It Important?
Managing user privileges is crucial in any organisation because it:
Protects sensitive information
Only the right people should be allowed to view or change important data like financial records, personal files, or system settings.
Reduces risk from mistakes
Limiting privileges prevents people from accidentally deleting files or changing settings they shouldn’t touch.
Prevents security threats
If a hacker gets access to a low-level account, they can’t do as much damage as they could with an admin account.
Keeps systems running smoothly
Users can focus on their own tasks without access to areas they don’t need, which improves efficiency and safety.
Different Levels of User Privileges
In most organisations, users are grouped into levels based on what they need access to. Here are the most common levels:
1. Administrator (Admin)
-
Who? IT managers or system administrators.
-
What they can do:
-
Install and delete software
-
Create or remove user accounts
-
Access all files and system settings
-
-
Example: An IT technician installing a new version of Microsoft Office across the whole school network.
2. Standard User
-
Who? Regular employees or students.
-
What they can do:
-
Access their own files
-
Use installed software
-
Save documents to shared folders (if allowed)
-
-
What they can’t do:
-
Change system settings
-
Install or uninstall programs
-
-
Example: A student logging into a school computer to write an essay in Microsoft Word.
3. Guest User (or Temporary Account)
-
Who? Visitors or temporary staff.
-
What they can do:
-
Very limited access, usually internet only or a few basic programs
-
-
Example: A parent using a school computer during a meeting to check their email.
How Do Organisations Manage These Privileges?
IT departments use tools such as Active Directory (on Windows networks) to manage who gets which privileges. They set up groups like “Teachers,” “Students,” or “HR Staff” and assign permissions based on those roles.
They also use policies like:
-
Least privilege principle: Users only get the minimum access they need.
-
Access reviews: Regular checks to make sure users still need the access they’ve been given.
-
Password policies: To ensure secure logins and prevent misuse.
Penetration/vulnerability testing
Penetration testing (or pen testing) is when someone tests a system to find weaknesses — just like a hacker would, but in a safe, controlled way. The idea is to spot problems before real attackers do.
Vulnerability testing is similar, but it focuses more on scanning systems automatically to look for known weaknesses, such as outdated software or misconfigured settings.
These tests are a key part of internet security assurance, which means proving that systems are secure.
Network penetration testing
This involves checking the network itself — like routers, firewalls, and computers — for ways an attacker might break in.
Example: Trying to access private files or control a computer on the school network without permission.
Social Engineering Penetration testing
This tests whether people are the weak point. The tester might try to trick someone into revealing a password or plugging in a dodgy USB stick.
Example: A fake email sent to a staff member asking them to “reset their password” — to see if they fall for it.
Physical Penetration testing
This checks if someone could physically access secure areas — like the server room — to plug in a device or steal equipment.
Example: Can someone walk into the IT office without a badge or keycard?
black box testing
The tester knows nothing about the system beforehand — just like a real hacker. They try to break in from the outside.
white box testing
The tester has full access to system details, like code and internal documentation. This helps find more complex or hidden problems.
o port scanning
A tool checks for open ports on a device — like digital doors — that could be used to break in.
Example: If Port 21 (FTP) is open but unprotected, someone could upload harmful files.
o SQL injecting testing
This tests if attackers can type special code into a website form to trick a database into giving out private data.
o Secure Sockets Layer (SSL)/Transport Layer Security (TLS) scanning
This checks if a website or system is using secure encryption (SSL or TLS). If the system is using an outdated or weak version, attackers might be able to read or steal data.
Protocols:
Here are some protocols (rules and tools) that help protect data and systems during or after testing:
VPN
Creates a secure, private connection over the internet. Useful for working remotely without being exposed.
Example: Staff working from home connect to the school network using a VPN.
o IPSec VPN
A type of VPN that uses IP Security (IPSec) to encrypt data at the network level. It’s very secure and often used by large organisations.
o SSL VPN
A type of VPN that runs in a web browser and uses SSL or TLS to protect the connection. It’s easier to use but slightly less powerful than IPSec.
SSL/TLS
These are the protocols that keep websites safe — you see them as a padlock in the browser bar (https://). TLS is the newer, safer version.
Example: When logging into a school email system, TLS keeps your username and password encrypted.
SFTP - secure file transfers
Used to send files securely over a network. It encrypts the data, so it can’t be read if intercepted.
Example: Uploading student grades from a teacher's laptop to the school server securely.
Secure shell (SSH) - secure connection to devices
A tool used by IT staff to securely log in and control devices over the network. It encrypts the session, so no one can spy on the commands being typed.
Example: A network admin uses SSH to fix a school server from their office computer.
HTTPS
The HTTP protocol is used to enable the transfer of internet and web traffic, however there are situations where data sent between the server and the client machine is required to be encrypted so that thier is limited opertunites for the data if intercepted to be used by those that it is not intended to be used by. The HTTPS protocol uses an alternative port that works with a secure service to send the data via an encrypted port, this being port 443.
Last Updated
2025-06-03 12:56:58
English and Maths
English
Maths
Stretch and Challenge
Stretch and Challenge
- Fast to implement
- Accessible by default
- No dependencies
Homework
Homework
Equality and Diversity Calendar
How to's
How 2's Coverage
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria.
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria.
Links to Learning Outcomes |
Links to Assessment criteria |
|
|---|---|---|
Files that support this week
Week 7→
Next 7Week 8→
Next 8Week 9→
Next 9←
Prev8