week 7
R10.7 The process and protocols of internet security assurance.
Processes:
Installation and configuration of firewalls:
The use of firewalls within an organisation is a key to the protection from both external and internal threats. The more obvious is external attempts to gain access to the internal network to access sensitive data or functions. Firewalls can be both software and hardware, most commonly used are software based, typically found within a router.
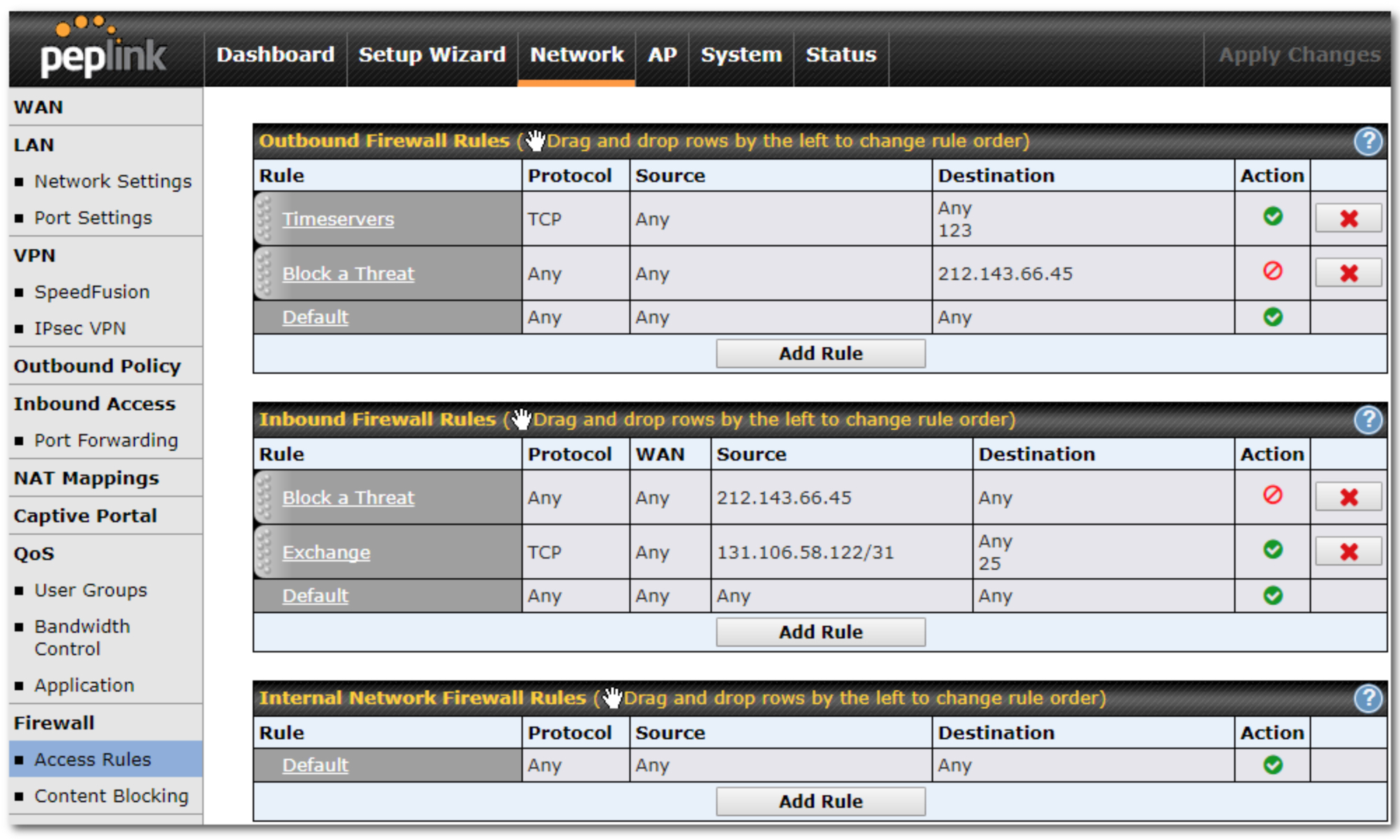 As you can see from the image above the firewall can restrict network and internet traffic and if needed redirect it to a specific attached network server or device.
As you can see from the image above the firewall can restrict network and internet traffic and if needed redirect it to a specific attached network server or device.
These firewall can be bespoke to the device and vendor created, however there are open source options available such as , XXXXXXX. Microsoft also offer thier own firewall options using Microsoft Defender.
o inbound and outbound rules:
▪ traffic type rules
▪ application rules
▪ destination and source rules
Network segregation:
o VLANs
o physical network separation
o offline networks
Network monitoring
Removable media controls
Anti-virus
Managing user privileges
Penetration/vulnerability testing:
Network penetration testing
Social Engineering Penetration testing
Physical Penetration testing
black box testing
white box testing
o port scanning
o SQL injecting testing
o Secure Sockets Layer (SSL)/Transport Layer Security (TLS) scanning
Protocols:
• VPN
o IPSec VPN
o SSL VPN
• SSL/TLS
• SFTP - secure file transfers
• secure shell (SSH) - secure connection to devices
• HTTPS
The HTTP protocol is used to enable the transfer of internet and web traffic, however there are situations where data sent between the server and the client machine is required to be encrypted so that thier is limited opertunites for the data if intercepted to be used by those that it is not intended to be used by. The HTTPS protocol uses an alternative port that works with a secure service to send the data via an encrypted port, this being port 443.
Last Updated
2025-05-06 15:26:05
Links to Learning Outcomes |
Links to Assessment criteria |
|
|---|---|---|
English
Maths
How 2's Coverage
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria.
Anonymous Assessment - Learners assess an anonymous piece of work containing deliberate mistakes against given success criteria.
Files that support this week
Week 7←
PrevWeek 8←
Prev→
Next